First let’s scan ports with nmap:
nmap -sC -sV 10.10.103.60 -p-
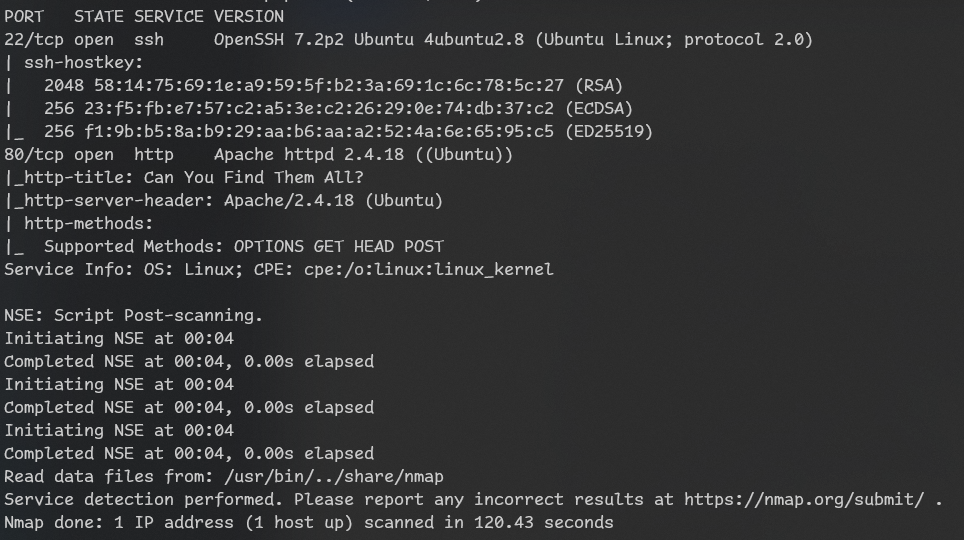
Since we only have port 20 and 80 let’s start with checking http. While exploring it in browser let’s run enumeration:
ffuf -w /usr/share/dirbuster/directory-list-lowercase-2.3-medium.txt -ic -u http://10.10.103.60/FUZZ
Opening page in browser I see modified apache2 default page.
As always we check source code cause it can have some extra information.
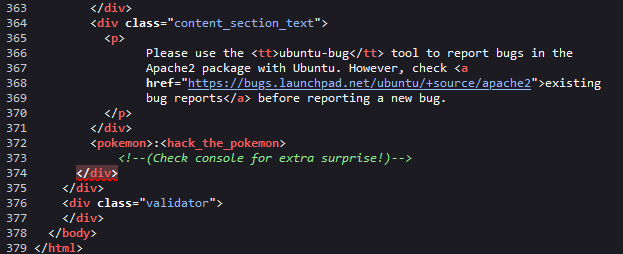
Found strange <pokemon> and <hack_the_pokemon> tags as well as a little hint
Let’s check console like comment says:
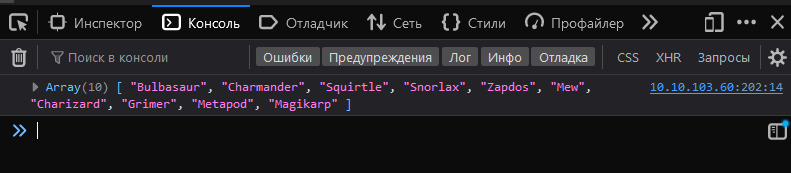
I got this array. Let’s keep it for now.
At this point I got stuck cause enum returned nothing.
After reviewing what I’ve done I recognized that
<pokemon>:<hack_the_pokemon> might be username:password
And yes! It was!
Started researching machine:
- Found users
root,pokemonandashin/etc/passwd - Found P0kEmOn.zip in
~/Desktop - Found
~/Videos/Gotta/Catch/Them/ALL!/Could_this_be_what_Im_looking_for?.cplusplus
Lets download that .zip file After unzipping it only had one file grass-type.txt with contents of hex.
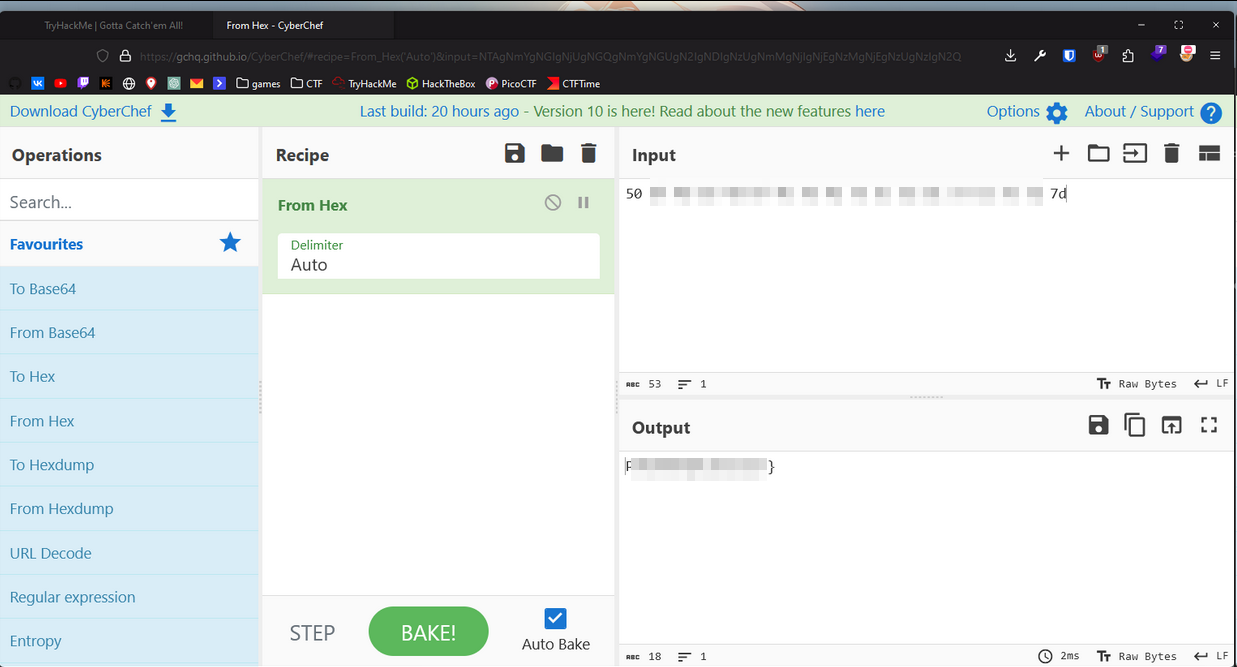
~/Videos/Gotta/Catch/Them/ALL!/Could_this_be_what_Im_looking_for?.cplusplus has creds inside! Let’s try.
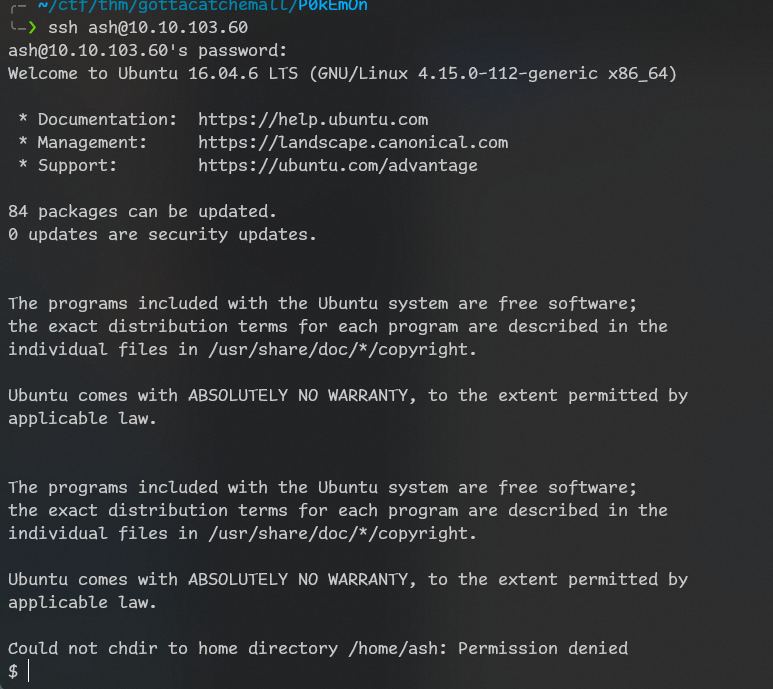
since permission to
/home/ash was denied i tried checking different privesc scenarios to access it and found some interesting things
$ ls /home
ash pokemon roots-pokemon.txt
$ cat roots-pokemon.txt
<REDACTED>
$Got one more flag!
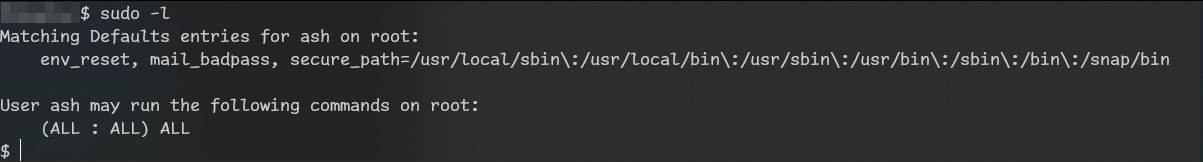
so we have sudo ALL which means we can just run sudo bash
We can just run
# find / -type f -name "*-type.txt"
/var/www/html/water-type.txt
/etc/why_am_i_here?/fire-type.txt/etc/why_am_i_here?/fire-type.txt is base64 encoded string
$ cat /etc/why_am_i_here?/fire-type.txt | base64 -d
<RECATED>/var/www/html/water-type.txt looks like ROT cipher for me!
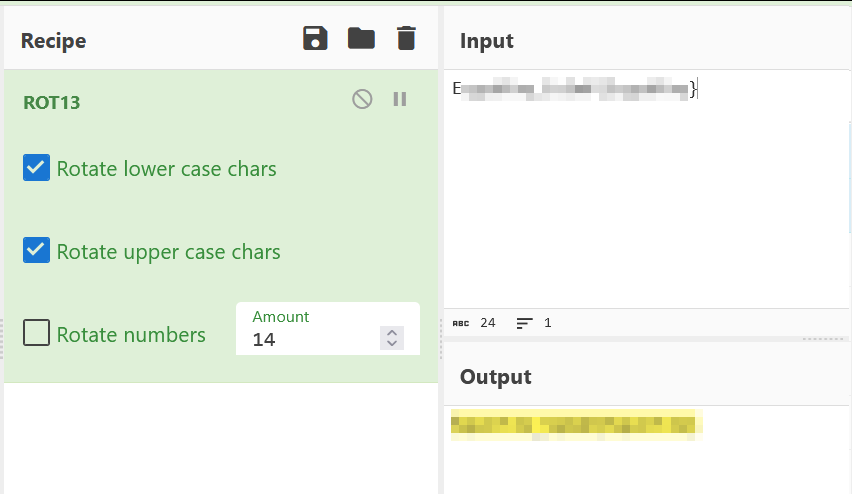
Got all the flags!